101 Data Security Tips: Quotes from Experts on Breaches, Policy, News & More
| Contact Us | |
| Free Demo | |
| Chat | |
Get 101 data security tips on mobile security, password security, secure browsing and more.
Data security is a top concern not only for enterprises and small business, but for everyday consumers as well. With widespread data breaches exposing everything from customer login credentials to credit card information to personal health records, consumers must be savvy about data security and take steps to protect their own information. Fortunately, there are many ways individuals and families can take extra precautions to ensure their personal data is safe and secure from hackers and malicious criminals. While few security measures can guarantee that no data security breaches will affect you, implementing multiple layers of personal data security protections substantially reduces the likelihood that your data will be compromised. Educating yourself on what to do should your identity be stolen or your personal data exposed will help you take the proper steps to minimize damage after the fact.
To that end, we've compiled a list of 101 informative quotes on data security, ranging from quotes about the state of modern data security to useful tips on protecting your family's personal information, how to teach your children proper data security measures and keep them safe online, identifying hoaxes and scams, and more. The following 101 data security quotes are categorized for simple perusing and are not listed in any particular order of importance.
Table of Contents:
- General Computer and Device Security
- Securing Your Mobile Devices
- Email Security Quotes
- Identifying Hoaxes and Scams
- Password Security
- Phishing Attempts
- Identity Theft
- Malware, Spyware, and Viruses
- Secure Browsing
- Security on the Social Web and in the Cloud
- Data Security Quotes for Parents, Teens, and Kids
General Computer and Device Security

1. "If there are other people using your computer, you may be worried that someone else may accidentally access, modify, and/or delete your files. Most operating systems (including Windows XP and Vista, Mac OS X, and Linux) give you the option of creating a different user account for each user, and you can set the amount of access and privileges for each account. You may also choose to have separate accounts for your work and personal purposes. While this approach will not completely isolate each area, it does offer some additional protection. However, it will not protect your computer against vulnerabilities that give an attacker administrative privileges. Ideally, you will have separate computers for work and personal use; this will offer a different type of protection." - United States Computer Emergency Readiness Team (US-CERT) Twitter: @uscert_gov
2. "It's always a good idea to lock your PC if strangers are nearby and you step away for a few minutes. Just press Windows key+L to lock your PC. Alternatively, you can set your screensaver (via the Screensaver tab in Display Settings under Control Panel) to require a password if it's deactivated by checking the box in 'Settings' that says 'On resume, password protect.'" - ComputerShopper.com (The Best Computer Tips and Tricks: Data Security) Twitter: @computershopper
3. "Practice the principle of least privilege. Do not log into a computer with administrator rights unless you must do so to perform specific tasks. Running your computer as an administrator (or as a Power User in Windows) leaves your computer vulnerable to security risks and exploits. Simply visiting an unfamiliar Internet site with these high-privilege accounts can cause extreme damage to your computer, such as reformatting your hard drive, deleting all your files, and creating a new user account with administrative access." - Indiana University (Best practices for computer security) Twitter: @insideUITS

4. "Software updates often fix security problems, so download updates as soon as they become available. To make this easier, more software programs–including Windows, Office, Flash, Java and Adobe Acrobat—now offer options to download and install updates automatically; these can generally be accessed through 'Settings' or 'Preferences.'" - California SBDC (10 Tips to Computer Security for Your Small Business – June 2012) Twitter: @SBDCLosAngeles
5. "Your computer operating system may allow other computers on a network, including the Internet, to access the hard-drive of your computer in order to “share files”. This ability to share files can be used to infect your computer with a virus or look at the files on your computer if you don’t pay close attention. So, unless you really need this ability, make sure you turn off file-sharing. Check your operating system and your other program help files to learn how to disable file sharing. Don’t share access to your computer with strangers!" - CyberSmart.org (Internet Safety Tips for Elementary and Middle School Students, Educators and Families)
6. "The biggest mistake any hardware user can make is to ignore backing up their data. Software can be reinstalled; data lost is irreplaceable. We are in a digital age and a lot of our data is stored digitally – bank records, photos, letters, music. A recent NCSA/Symantec study showed that over 68% of Americans store more than 25% of their photos digitally, for example. There are any number of ways data can be lost. Accidental deletion is common. Device failure happens. Natural events, such as electrical or wind storms, fires, or floods can eradicate data. Cyber events such as viruses, spyware or other cyber attacks can remove data, as well." - SafetyWeb (Cyber Security Tips)

7. "The Internet of Things arrived in force at this year's International CES, the huge trade show here. But while manufacturers at the event painted a rosy picture of connected grills, coffee makers, refrigerators, and door locks, security experts and regulators warned that the Internet of Things could be a threat to both security and privacy. Hackers have already breached Internet-connected camera systems, smart TVs, and even baby monitors. In one case, someone hacked a networked camera setup and used it to scream obscenities into a baby nursery." - Molly Wood, The New York Times (CES: Security Risks from the Smart Home) Twitter: @mollywood
8. "You have to make sure that your hard drive is external from your computer. If you put yourself in the minds of the thief, they want to make a quick buck. They don’t really care about your hard drive, just your computer. An external hard drive is critical. In my case they left the hard drive behind and I was able to plug it into my new computer. It was the key to everything." - Michael Stelzner, Social Media Marketer (Theft: 9 Ways to Protect Yourself from Losing Your Data) Twitter: @SMExaminer
9. "It is important to properly handle data erasure and disposal of electronic media (e.g. PCs, CDs, thumb drives) in order to protect confidential and sensitive data from accidental disclosure. Become familiar with the proper methods of sanitizing, destroying, or disposing of media containing sensitive information." - Multi-State Information Sharing and Analysis Center (Safeguarding Your Data) Twitter: @CISecurity

10. "Disable the Auto-Run feature in Windows. This built-in Windows component allows silent programs to execute without your knowledge because auto-run grants them permission to initiate without obtaining active consent." - ComboFix.org (15 Tips for Online Safety and Security)
11. "Many recommendations across the 'Net sound like this: 'Don't keep your information on the cloud.' Fair enough, but it's the same as if you asked, 'How not to get my house burned down?' and the answer would be, 'Do not have a house.' The logic is solid, but a better way to translate such advice is, 'avoid storing sensitive information on the cloud.' So if you have a choice you should opt for keeping your crucial information away from virtual world or use appropriate solutions." - Victoria Ivey, CIO.com (5 Tips to Keep Your Data Secure on the Cloud) Twitter: @CIOonline
12. "Your Windows login password is not encrypting your computer (surprise!). Full-disk encryption (used by very few people) is a good step, but by itself it still will not completely protect your data from prying eyes, overzealous governments, or your own mistake of leaving your company's crown jewels at the local coffee shop." - Brandon Gregg, CSO Online (Three steps to properly protect your personal data) Twitter: @CSOonline

13. "Nearly 60 percent of Americans use three or more Internet-connected devices at home across three different operating systems, according to a recent survey by the Internet security company AVG. With so many gadgets connected to online marketplaces, credit-card and Social Security numbers, banking information, passwords, family photos, and more accumulate in places you might not expect—say on that 7-year-old Nintendo Wii collecting dust on a shelf in your family room or on a hard drive you used to back up your PC at some point very early in President Obama's first term." - ConsumerReports.org (Avoid ID theft and protect personal data when getting rid of a gadget) Twitter: @ConsumerReports
14. "A security system with several layers is difficult to hack. So, even if your data is targeted, getting through the many tiers of security will be a hassle. The simplest of programs, such as free online email accounts, have multi-layered security, too. Even if accessing your accounts takes a few extra steps, it is still worth the effort, certainly better than losing your data. Using a firewall, making sure your antivirus software is updated, running antivirus checks frequently and updating your programs regularly are all part of maintaining your personal data security." - Doug Theis, Innovative Integration, Inc. (3 Simple Tips for Protecting Personal Data) Twitter: @InnovativeII
Securing Your Mobile Devices
15. "You likely use your mobile devices to access or store personal and private information—notes, photos, contacts, financial accounts, saved passwords, and more. Accordingly, it is important that you properly secure and manage your mobile devices to protect your personal information." - University of Michigan Information and Technology Services (Protect Your Mobile Device) Twitter: @its_umich
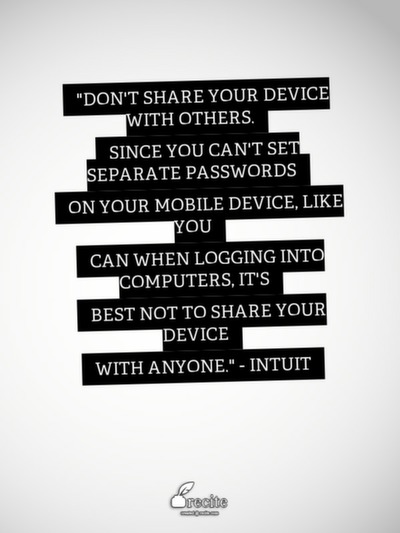
16. "Don't share your device with others. Since you can't set separate passwords on your mobile device, like you can when logging into computers, it's best not to share your device with anyone." - Intuit (Protect Your Mobile Device) Twitter: @intuit
17. "This might seem like a 'duh' tip, but it surprises me how many people I meet who don't have a lock screen enabled. Your password is the first line of defense in keeping your data secure, and is the easiest security feature to set up. Of course it's also worth noting that newer phones on the market like the iPhone 6 and Samsung Galaxy S5 have a fingerprint sensor for locking your phone." - Brian Burgess, Gizmag (Essential Tips to Keep Your Smartphone Secure) Twitter: @gizmag
18. "SnoopWall, a cybersecurity firm led by a founding member of the U.S. Department of Homeland Security, found that all of the top 10 most popular flashlight apps required user permission to access sensitive data and could actually control and change phone settings. We recently reported that many free flashlight apps that are so popular may be spying on users and stealing their data." - James Geddes, Tech Times (Free apps like Flashlight can spy and steal personal data: Protect your smartphone with these tips) Twitter: @TechTimes_News

19. "The popularity and adoption of smartphones has greatly stimulated the spread of mobile malware, especially on the popular platforms such as Android. In light of their rapid growth, there is a pressing need to develop effective solutions. However, our defense capability is largely constrained by the limited understanding of these emerging mobile malware and the lack of timely access to related samples." - Yajin Zhou and Xuxian Jiang, Department of Computer Science, North Carolina State University (Android Malware Genome Project) Twitter: @NCState
20. "Attacks that proved successful on PCs are now being tested on unwitting mobile device users to see what works – and with the number of mobile devices with poor protection soaring, there are plenty of easy targets. 'Attackers are definitely searching after the weakest point in the chain,' and then honing in on the most successful scams, says Lior Kohavi, CTO at CYREN, a cloud-based security solutions provider in McLean, VA." - Stacy Collett, CSO Online (Five new threats to your mobile device security) Twitter: @CSOonline
21. "Mobile computing devices can store large amounts of data, are highly portable and are frequently unprotected: They are easy to steal or lose, and unless precautions are taken, an unauthorized person can gain access to the information stored on them or accessed through them. Even if not stolen or lost, intruders can sometimes gain all the access they need if the device is left alone and unprotected, if data is 'sniffed out of the air' during wireless communications, or if malware is installed. The results can include crippled devices, personal data loss, disclosure of non-public University data, and disciplinary actions for the device owner." - Stanford University IT, Secure Computing (Guidelines for Securing Mobile Computing Devices) Twitter: @Stanford

22. "Today's mobile devices are as powerful and connected as any PC or laptop. Take the same precautions on your mobile device as you do on your computer with regard to messaging and online safety. The first step is STOP. THINK. CONNECT." - StaySafeOnline.org (Mobile Devices) Twitter: @StaySafeOnline
23. "Whether you're traveling with a laptop, netbook, smartphone, iPad, or all of the above, the risks and defenses against them are basically the same, according to Joe Nocera, an information security expert and a principal with PricewaterhouseCoopers. 'Many of the security concerns that people think about when they think about their personal computers are applicable in the mobile world.' As mobile devices become more sophisticated, they lend themselves to the same types of access to e-mail, passwords, and other secure information that PCs have done in the past." - Logan Kugler, PCWorld (9 Ways to Keep Your Mobile Devices Secure While Traveling) Twitter: @pcworld
24. "Consider using an image that provides a contact point should someone find your device and wish to return it. For example, the 'If Found Lock Screen' for Apple products." - The University of Chicago IT Services (Mobile Device Security Best Practices) Twitter: @UChicagoITS

25. "Mobile phones, smart phones (phones that support email, documents, and applications) and tablets (such as iPads) are getting fancier and more popular all the time. This makes them a target for theft -- hundreds of thousands of mobile devices are reported lost or stolen each year. A thief could use your wireless access, steal your identity and credit card information, or cause you to pay for a new phone and unauthorized charges on your bill." - MIT Information Systems and Technology (Risks of Mobile Phones and Tablets) Twitter: @mit_istnews
Email Security Quotes
26. "Microsoft never sends out patches or updates by email. There are no exceptions. Keep that in mind and you won't be a victim of a Microsoft patch hoax. The first time I received one of these, I sat down at my workstation and saw an email message from Microsoft telling me to install the patch they had handily supplied as an attachment. I knew this was bogus immediately. We sent out a voicemail quickly warning all employees not to fall for opening attachments that offer to install any kind of software. That was March, 1999. Every 18 months or so, someone tries this hoax again by crafting and sending out a phony email complete with a Microsoft look-alike logo, spoofed return address, links, etc., and some text assuring you that this is all the real thing. It isn't." - SANS Security Awareness Tip of the Day Twitter: @SANSInstitute
27. "Be suspicious of any unexpected email attachments even if they appear to be from someone you know. A simple rule of thumb is that if you don't know the person who is sending you an email, be very careful about opening the email and any file attached to it. Should you receive a suspicious email, the best thing to do is to delete the entire message, including any attachment." - KPBSD Connections

28. "Never send your credit card number, Social Security number, bank account number, driver's license number, or similar details in an email, which is generally not secure. Think of email as a paper postcard — people can see what's written on it if they try hard enough. Be suspicious of any company that asks for this type of information in an email or instant message. Most legitimate companies will never ask you to confirm sensitive data in an online form or in an email; instead, they'll use postal mail to request this information." - Yahoo Safety Center (How can I prevent identity theft?) Twitter: @Yahoo
29. "One of the first things that I recommend checking in a suspicious email message is the integrity of any embedded URLs. Often times the URL in a phishing message will appear to be perfectly valid. However, if you hover your mouse over top of the URL, you will see the actual hyperlinked address (at least that’s how it works in Outlook). If the hyperlinked address is different from the address that is displayed, then the message is probably fraudulent or malicious." - Brien Posey, TechRepublic (10 Tips for Spotting a Phishing Email) Twitter: @TechRepublic
30. "By using botnets, spammers are able to send millions of spam e-mails every day. The test institute AV-TEST from the German city of Magdeburg recently carried out an 18-month-long study in which it collected and evaluated over half a million spam emails before coming to the conclusion that the risk posed by spam is higher than ever." - AV Test (Spam – More Dangerous than Ever Before) Twitter: @avtestorg
Identifying Hoaxes and Scams

31. "Be a little suspicious. A very large number of attacks rely on simple social engineering. Ask yourself next time you receive an e-mail claiming you have won an iPad or received a FedEx package — is this probably real? Would it happen to me walking down the street? Scams today aren’t all identifiable by poor grammar and spelling mistakes, as they once were." - James Lyne, TED Speaker (6 basic tips for better online security, from TED speaker James Lyne) Twitter: @jameslyne
32. "The practice of trying to trick or manipulate people into breaking normal security procedures is called 'Social Engineering'. The principle behind social engineering and scams in general is that people are the weak link in security – that it can be easier to trick people than to hack into computing systems by force. Social engineers exploit people’s natural tendency to want to trust and be helpful. They also take advantage of our tendency to act quickly when faced with a crisis." - University of California Santa Cruz Information Technology Services (Beware of Scams)
33. "Hoaxes attempt to trick or defraud users. A hoax could be malicious, instructing users to delete a file necessary to the operating system by claiming it is a virus. It could also be a scam that convinces users to send money or personal information." - U.S. Department of Homeland Security (Internet Hoaxes) Twitter: @DHSgov

34. "It is unclear why people create Internet hoaxes and chain letters in emails. Most people are not able to generate any money from those who read the email or forward it. The intent appears to be malicious in that those who respond to such emails become the victims of a cruel joke. The hoax or chain letter may also contain viruses and malware that will seriously harm a computer." - DateHookup.com (Internet Hoax and Chain Letter Information Center) Twitter: @datehookup
Password Security
35. "A password manager is a secure storage location for all your different passwords. It integrates with your web browser and automatically enters your username and password for you when you are logging in to a website. A good password manager will also generate secure passwords for you when you register with a new site or change a password. The password manager protects its contents by using a special “master” password. Needless to say, it is critical to choose a very strong master password. Some password managers allow you to add multi-factor authentication in addition to your master password to give you an extra layer of security. There are plenty of good password managers to choose from (far too many to mention here) and many of them are free. I often recommend LastPass, KeePass or Password Safe." - Dave Herrald, GTRI (Five Cyber Security Tips for Computer and Online Safety) Twitter: @GTRI_Global
36. "Choose strong passwords with letters, numbers, and special characters to create a mental image or an acronym that is easy for you to remember. Create a different password for each important account, and change passwords regularly." - MIT Information Systems and Technology (Top Ten Safe Computing Tips) Twitter: @MIT_ISTnews

37. "Cyber criminals can use personal details, such as your favorite color, the last four digits of your credit card and your email addresses, to make educated guesses about your sign-in credentials. They might contact a service provider posing as a user, provide identifying details and gain even greater access to accounts. This is why it is so important to prevent your security credentials from becoming stagnant. Rotate your password every few months and consider using new security questions and answers, too." - Larry Alton, Entrepreneur.com (3 Simple Precautions for Protecting Your Personal Data in the Cloud) Twitter: @Entrepreneur
38. "Nowadays, both mobile and desktop users can use password managers designed to house all-important credentials in one spot and create difficult passwords for sensitive sites. All a user needs to do is remember the password for actually getting into the application, like 1Password or Password Manager, and he or she has full access to important accounts. Such password managers are important: They act as a repository for credentials, they create strong passwords, and they can populate password fields whenever the user goes to a particular site. Definitely check them out." - Don Reisinger, eWeek (Securing Sensitive Personal Data in Cloud Services: 10 Best Practices) Twitter: @eWEEKNews
39. "Rather than lecture you yet again on why you should use good passwords, let me suggest that you use easy-to-remember, but hard to crack passwords that use phrases rather than random characters. So, for example, 'Steelers?Win!Cowboys?Lose!' or 'Volt!Amp!Tesla!Edison?' won't be cracked by any common password cracker program but you'll be able to recall such phrases much more easily than say 'ufc#1310.' Safe passwords don't have to be memory twisters. They just have to be hard for computers to work out, and phrases make great passwords." - Steven J. Vaughan-Nichols, ZDNet (After alleged iCloud breach, here's how to secure your personal cloud) Twitter: @ZDNet
Phishing Attempts

40. "When internet fraudsters impersonate a business to trick you into giving out your personal information, it’s called phishing. Don't reply to email, text, or pop-up messages that ask for your personal or financial information. Don’t click on links within them either – even if the message seems to be from an organization you trust. It isn’t. Legitimate businesses don’t ask you to send sensitive information through insecure channels." - OnGuardOnline.gov (Phishing)
41. "Phishing is a form of social engineering. Phishing attacks use email or malicious websites to solicit personal information by posing as a trustworthy organization. For example, an attacker may send email seemingly from a reputable credit card company or financial institution that requests account information, often suggesting that there is a problem. When users respond with the requested information, attackers can use it to gain access to the accounts." - United States Computer Emergency Readiness Team (US-CERT) (Avoiding Social Engineering and Phishing Attacks) Twitter: @USCERT_gov
42. "When conducting online transactions, look for a sign that the site is secure such as a lock icon on the browser’s status bar or a 'https:' URL whereby the 's' stands for 'secure' rather than a 'http:'. Also, beware of phone phishing schemes. Do not divulge personal information over the phone unless you initiate the call. Be cautious of emails that ask you to call a phone number to update your account information as well." - Identity Theft Killer (Are You Phishing for Trouble?)

43. "'Many people think that computer security concerns only relate to viruses, but personal security is equally important,' said Kathy Kimball, director of Security Operations and Services (SOS). 'There are numerous types of fraud that can endanger computer users on a personal level—and e-mail is an extremely effective way to distribute fraudulent messages to potential victims.'" -Kathy Kimball, Director of Security Operations and Services (SOS), as quoted by Penn State University Information Technology Services (Phishing Tips) Twitter: @pennstatenews
44. "When fraudsters go on 'phishing' expeditions, they lure their targets into a false sense of security by hijacking the familiar, trusted logos of established, legitimate companies. A typical phishing scam starts with a fraudster sending out millions of emails that appear to come from a high-profile financial services provider or a respected Internet auction house." - U.S. Securities and Exchange Commission ("Phishing" Fraud: How to Avoid Getting Fried by Phony Phishermen)
45. "Social engineering scams are a particular concern. With these scams, attackers present a post intended to get the target user to click on a link. That link usually leads to the user downloading some malicious code that has the potential to steal information on the user’s computer or mobile device. These scams are sometimes also called phishing and baiting, as well as click-jacking. Whatever they’re called, just know that not every post on social media is safe to click on. You should take special care to treat every link with suspicion, especially those that look like click bait." - Rick Delgado for the National Edition, Tech Cocktail (The Biggest Security Concerns with Social Media You Need to Know) Twitter: @TechCocktail

46. "Two-factor authentication is coming soon to Twitter, but it's not likely to happen overnight. And it won't solve the world's online security woes when it does roll out. Phishing attacks -- like the one that may have been behind the recent Twitter AP hoax -- will persist because they work. Social engineering scams will grow more creative in their efforts to con people into coughing up bank account info, network credentials and other sensitive data. And social sites -- all of which are predicated upon words like sharing and connecting -- will be a prime breeding group for such activity, even with tighter perimeter defenses such as two-factor authentication. We're still human, after all, and therefore susceptible to making mistakes." - Kevin Casey, InformationWeek Network Computing (Twitter Trouble: 9 Social Media Security Tips) Twitter: @networkcomputin
Identity Theft
47. "For years, popular opinion held that the threat of identity theft was overblown and that we in the business of resolving it were selling fear. All that has changed." - StaySafeOnline.org (The Best Privacy Solution? Assume There Is None) Twitter: @StaySafeOnline
48. "President Obama proposed two new data protection laws Monday, calling cybercrime a 'direct threat to the economic security of American families.' One of the measures, the Personal Data Notification and Protection Act, would give hacked businesses 30 days to notify customers of a data breach." - Jeff Stone, International Business Times (Obama: Cybercrime, Identity Theft Pose 'Direct Threat To Economic Security Of American Families') Twitter: @IBTimes

49. "In an increasingly interconnected world, American companies are also leaders in protecting privacy, taking unprecedented steps to invest in cybersecurity and provide customers with precise control over the privacy of their online content. But as cybersecurity threats and identity theft continue to rise, recent polls show that 9 in 10 Americans feel they have in some way lost control of their personal information — and that can lead to less interaction with technology, less innovation, and a less productive economy." - The White House, Office of the Press Secretary (FACT SHEET: Safeguarding American Consumers and Families) Twitter: @WhiteHouse
50. "Neal O'Farrell, executive director of the Identity Theft Council, calls the U.S. postal system 'an absolute gift' for identity thieves, who can reach into your mailbox and grab whatever's there. Subvert them by doing as much banking and bill paying online as possible. Doing this makes you less vulnerable, not more." - Jean Chatzky, AARP The Magazine (Protect Your Personal Data) Twitter: @AARP
51. "At least twenty states have passed laws requiring small businesses to implement procedures to prevent personal information from being disclosed or improperly used. Some states specifically require that small businesses encrypt personal information that is sent over the Internet. Unlike federal laws, these state laws apply to all small businesses — not just those that are financial institutions or health care providers. Additionally, almost every state has passed legislation requiring disclosure of any incidents involving the loss of consumer information." - Better Business Bureau (Securing Your Personal Data) Twitter: @bbb_us
52. "Data privacy and security is about much more than keeping hackers at bay. It is also about assuring consumers that the trust they place in a consumer product brand is warranted. The results of a recent survey of consumers and executives show that consumers have a keen sense of awareness of the risks surrounding data security and privacy, and that many consumer product executives are likely overestimating the extent to which they are meeting consumer expectations related to data privacy and security." - Pat Conroy, Frank Milano, Anupam Narula & Raj Singhal, Deloitte University Press (Building Consumer Trust) Twitter: @DU_Press

53. "Federal agencies need to do a better job handling data breaches. The number of security incidents involving personally identifiable information has more than doubled just in the past four years, a new report by the Government Accountability Office says." - Elena Malykhina, Information Week (Federal Agencies Fail To Protect Personal Data) Twitter: @InformationWeek
54. "Many online services require users to provide some personal information in order to use their service. Prior to providing personal information, users should try to think about what can potentially be done with their personal information and assess whether they are still happy to pass on these details." - Cybersmart.gov.au (Protecting Personal Information) Twitter: @CybersmartACMA
55. "Data. We love it. And we also know just how important it is to keep it safe. These days we’re plugged in anywhere and all the time. Sometimes, we may not even realize how plugged in we actually are while our apps, web searches, and credit card purchases are constantly storing our actions in the background." - Katie Atkinson, Survey Monkey Blog (Protecting Personal & Workplace Data: Do Americans Really Care?) Twitter: @SurveyMonkey

56. "You might think that your government is vigilant when it comes to securing your personal information, or that of your children. You would be wrong. Hackers have discovered one of the biggest potential security holes of the modern era, one that can leave data exposed to any hacker willing to find it. And in at least one instance, that vulnerability has resulted in a data breach impacting almost three dozen children and their families." - Jake Tapper, CNN Chief Washington Correspondent (Government agencies not securing your data, or your kids') Twitter: @TheLeadCNN
57. "Over the past four years 39 states have enacted laws mandating consumer notifications if there is a theft of personal data from the company computers. The Federal Trade Commission ('FTC') has also brought enforcement actions against companies for not properly protecting sensitive personal data. These state and federal laws are in addition to general privacy laws and policies that require advance disclosures to those giving personal information." - Dorsey.com ("Protecting Personal Data in Franchise Systems: New Notification Laws," (co-author) LJN’s Franchising and Business Law Alert) Twitter: @DorseyWhitney
58. "'Identity theft is a serious issue and anyone who doesn’t take precaution is putting themselves at risk of becoming the next victim,' said Gail Cunningham, spokesperson for the NFCC. 'Being aware and proactively protecting yourself from identity theft is much easier than cleaning up the pieces after being exploited.'" -Gail Cunningham, spokesperson for the NFCC, as quoted by SimplifiedTechSolutions.com (Top 11 Tips For Protecting Personal Data )

59. "'I always tell people that if you haven’t had your identity stolen already, you will,' said Mike Sullivan, director of education for Take Charge America, a nonprofit credit counseling firm. 'There are just so many outlets and so many ways it can happen.'" -Mike Sullivan, director of education for Take Charge America, as quoted by Nick Diulio, The SpareFoot Blog (What Everyone Needs to Know About Protecting Personal Data) Twitter: @TCAsolutions
60. "Around 55 percent of all businesses acknowledge that they secure credit card information but not Social Security numbers, bank account details, and other personal data, according to a survey of more than 500 companies released Wednesday by Imperva and Ponemon Institute." - Lance Whitney, CNET (Survey: Half of businesses don't secure personal data) Twitter: @CNET
61. "Few frequent travelers appear fully aware of the wider risks involved when loyalty data—including travel schedules and other personal data—is lost or stolen. Roughly one in seven (15 percent) are simply concerned that a breach would result in a loss of loyalty points, while the majority of travelers (76 percent) worry about the loss of credit card numbers." - LODGING (Survey Finds Consumers Don’t Trust Hotels to Protect Personal Data) Twitter: @LodgingMagazine
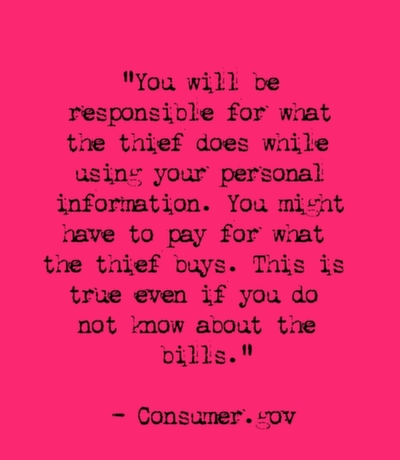
62. "You will be responsible for what the thief does while using your personal information. You might have to pay for what the thief buys. This is true even if you do not know about the bills." - Consumer.gov (Avoiding Identity Theft)
Malware, Spyware, and Viruses
63. "Malware (for 'malicious software') is any program or file that is harmful to a computer user. Thus, malware includes computer viruses, worms, Trojan horses, and also spyware, programming that gathers information about a computer user without permission." - Margaret Rouse, TechTarget (malware (malicious software)) Twitter: @SearchMMSec
64. "Malware is defined as computer virus software that spreads through malicious programs. Malware is short for 'malicious software' and can commonly be referred to as a 'computer virus.' Malware viruses includes worms, Trojans and other software created to conduct malicious activity. Malware usually appears in the form of a useful program that is available for download from a genuine-looking company website, email or pop-up advertisement. The malware program is written into the program and can cause harm to the user's computer, as well as monitor computer use and copy sensitive data." - Kaspersky Lab (Essential Malware Protection Advice for Families) Twitter: @kaspersky

65. "Although there is no guarantee that you’ll always be free from spyware, there are some things you can do to seriously lower your risk. First and foremost, you need to use an anti-spyware program that detects and prevents spyware from installing itself on your computer (and removes it). Anti-spyware software can also periodically scan your computer for spyware that may get through and remove it." - SchoolCounselor.com
66. "Thieves gather SSNs in many ways, from the high-tech – e.g., hacking, phishing, malware, spyware, and keystroke loggers – to the low-tech – e.g., dumpster diving, stealing workplace records, stealing mail or wallets, and accessing public records containing SSNs. What is not known, however, is the prevalence of each of these methods. This is due in large part to the fact that victims frequently do not know how their information was compromised. Moreover, even if reliable prevalence data were available, it likely would become outdated quickly as identity thieves change techniques to harvest consumers’ data." - FTC. gov (Security in Numbers: SSNs and ID Theft) Twitter: @FTC
67. "Malware is short for 'malicious software.' It includes viruses and spyware that get installed on your computer, phone, or mobile device without your consent. These programs can cause your device to crash and can be used to monitor and control your online activity. Criminals use malware to steal personal information, send spam, and commit fraud." - Federal Trade Commission (Consumer Information) Twitter: @FTC
68. "A security researcher examining the website of North Korea's official news service, the Korean Central News Agency, has discovered that the site delivers more than just the latest photo spread of Democratic Peoples' Republic of Korea leader Kim Jong Un inspecting mushroom farms. There's a little extra surprise hidden in the site's code—malware. The news site appears to double as a way for North Korea to deliver a 'watering hole' attack against individuals who want to keep tabs on the 'activities' of the DPRK's dear leader." - Sean Gallagher, Ars Technica (Surprise! North Korea’s official news site delivers malware, too) Twitter: @arstechnica

69. "Network monitoring software or abnormal user behavior are two ways to detect an attacker within your network, but new malware dubbed 'Skeleton Key' can evade both." - Sara Peters, Information Week Dark Reading ('Skeleton Key' Malware Bypasses Active Directory) Twitter: @DarkReading
70. "In May 2012, the IC3 posted an alert about the Citadel malware platform used to deliver ransomware known as Reveton. The ransomware directs victims to a download website, at which time it is installed on their computers. Ransomware is used to intimidate victims into paying a fine to “unlock” their computers. The ransomware has been called 'FBI Ransomware' because it frequently uses the FBI’s name, but similar ransomware campaigns have used the names of other law enforcement agencies such as DHS and IC3." - FBI.gov (New e-Scams and Warnings) Twitter: @FBI
Secure Browsing
71. "Many people use the Internet on a daily basis without trouble, but it can harbor some hidden dangers to you and your computer. These risks can include exposure of sensitive personal information and infection by malware, which includes viruses, spyware, and adware. Safe browsing means being aware of these online threats and taking the necessary steps to avoid them." - Northwestern University Information Technology (Tips for Safe Browsing) Twitter: @NU1HELP

72. "You can increase your privacy and security by shopping only at sites and using only services that have been certified by an Internet trust organization. For more information about trust organizations, go to the TRUSTe website, the BBB Online website, or the WebTrust website. Note: These seals don't always guarantee that a website is trustworthy. Some unscrupulous websites might display the trust logos fraudulently." - Microsoft Safety & Security Center (How do I know if I can trust a website) Twitter: @Safer_Online
73. "Most people still use Internet Explorer or Safari for browsing. They’ve come on in recent years- especially Internet Explorer. Still, my personal recommendation is to use Google Chrome as your browser as it’s been hailed as the most secure of browsers again and again." - Ian Anderson Gray (10 Tips to Make Your Computer More Secure) Twitter: @iagdotme
74. "Chrome's phishing and malware protection put up a warning screen whenever you visit a website that Google has identified as potentially malicious, whether it spreads malware or tries to steal your personal information. Meanwhile, Chrome's URL autocorrect feature usees a Google-provided online service to fix misspelled URLS to help you avoid visiting the wrong site—and perhaps a nefarious site—by accident. Indeed, 'typosquatting' is still a threat." - Eric Geier, PCWord.com (Google Chrome: Best Security Tips for Safer Browsing) Twitter: @pcworld

75. "Steer clear of websites of ill repute. These are havens for malicious and annoying intruders like spyware." - GeekSquad (Six Tips to Keeping Your Data Safe) Twitter: @GeekSquad
76. "'Spoofing' means duplicating a legitimate website, by including familiar logos and by using a nearly identical website address or domain name, to solicit the user to submit personal information. While the website address may appear similar to that of a legitimate company, it was actually created by a copycat. Criminals often lure customers to 'spoofed' websites using “phishing” type emails." - William Francis Galvin, Secretary of the Commonwealth of Massachussetts (Eight Tips to Avoid Phishing Scams)
77. "Before entering sensitive information into a website, look for the security padlock symbol. The padlock is one way of checking that a website is safe and indicates that the information you submit is secure." -AppRiver for IT Business Edge (Five Tips for Safe Web Surfing, Whether at Your Desk or On-the-Go) Twitter: @ITBusinessEdge

78. "Every time you indulge into any sort of online activity, your data can be easily monitored and checked. The websites you visit receive your IP address, location, browser and operating system, screen resolution, ISP and more. You can check on what information you give away at stayinvisible.com. I have nothing against sharing this data when I do simple browsing. I am like Dutch windows without curtains -- doing nothing wrong, peep in whenever you want, I have nothing to hide." - Victoria Ivey, Beta News (5 tips to make your browsing safe and secure) Twitter: @BetaNews
79. "Secure web browsing is a game of changing tactics. Just when you think you’ve made your computer as safe to use as possible, the landscape changes. Cyber criminals are constantly developing new methods to hijack your system, and unless you stay ahead of the game you could find yourself with a very large problem." - Pat Heck, Lieberman Technologies (7 Tips for Safe Web Browsing) Twitter: @tweetLTnow
80. "Internet Explorer is widely considered the least secure browser compared to the other popular offerings. While IE has certainly gotten better over the years due to the backlash of public opinion on the matter, I still recommend you install Firefox or Chrome. Both offer better security, more helpful plug-ins and easier to understand configuration options to enable security features. No matter what browser that you use, always stay up to date on the browsers updates or patches." - Brad Dormanen, GWI (Five Safe Internet Browsing Tips) Twitter: @gwimaine

81. "Read website privacy policies. They should explain what is being collected, how the information is being used, whether it is provided to third parties and what security measures the company takes to protect your information. The privacy policy should also tell you whether you have a right to see what information the website has about you. If you don't see a privacy policy - or you can't understand it - consider doing business elsewhere." - MIT Information Systems and Technology (Secure Browsing) Twitter: @MIT_ISTnews
82. "Search without footprints via the 'other' search engines truly anonymous Web surfing requires the use of a VPN service that blocks your IP address as well as other personal information... If you simply want to prevent a search from being recorded in your Google Web History, use a different search service." - Dennis O'Reilly, CNET (Ten simple, common-sense security tips) Twitter: @CNET
83. "If you use Firefox, consider installing the Add-on Adblock to reduce the number of ads that show on your sites." - Georgia Tech Information Technology (Tips for Safe Browsing) Twitter: @GeorgiaTech
Security on the Social Web and in the Cloud

84. "What exactly is the cloud? It is basically the collection of computers on the internet that companies are using to offer their services. One cloud service that is being offered is a revolutionary storage method for your data. From music files to pictures to sensitive documents, the cloud invisibly backs up your files and folders and alleviates the potentially endless and costly search for extra storage space. An alternative to buying an external hard drive or deleting old files to make room for new ones, cloud storage is convenient and cost-effective. It works by storing your files on a server out in the internet somewhere rather than on your local hard drive... This allows you to back up, sync, and access your data across multiple devices as long as they have internet capability." - Boston University Information Security (How to Safely Store your Data in the Cloud) Twitter: @BU_Tweets
85. "So the cloud is a really nebulous term - no pun intended - for computing done remotely. So you're using the cloud if you are working off of your Google Drive and you're creating a document in Google Drive, you're working from the cloud. You are using the cloud when you do online banking. You're using the cloud when you store something in a Dropbox account. And you're even using the cloud when you're watching Netflix because Netflix outsources its data storage to Amazon's Web Services, which is a cloud-computing provider." -Nichole Perlroth, technology reporter for The New York Times, as quoted by Michael Martin for NPR (Clouds Are Convenient, But Be Paranoid To Protect Personal Data) Twitter: @nprnews
86. "Though seemingly private, IM sessions are vulnerable to hackers, spammers, and online predators. If you or your children use instant messaging, make sure you have IM protection from an Internet security suite or other means." - ZoneAlarm (How to Protect Your Family's PC) Twitter: @zonealarm

87. "As revealed by a Digital Trends piece last year, Facebook works with the three largest data brokers: Datalogix, Epsilon, and Acxiom. Any information you divulge on Facebook, Twitter or any other public social network is fair game. And if your public profile is filled with personal information, anyone can access it by paying $25 for an all-you-can-eat 'people search' service."- David Gorodyansky, Inc.com (If You Don't Protect Your Personal Data, Who Will?) Twitter: @inc
88. "Across the board, there is a universal lack of confidence among adults in the security of everyday communications channels—particularly when it comes to the use of online tools. Across six different methods of mediated communication, there is not one mode through which a majority of the American public feels 'very secure' when sharing private information with another trusted person or organization" - Mary Madden, Pew Internet (Public Perceptions of Privacy and Security in the Post-Snowden Era) Twitter: @pewresearch
89. "A recent poll conducted by Information Week has revealed that 40% of respondents are currently less confident about saving data, specifically private pictures, in the cloud." - Daniel Mauerhofer, LinkedIn Pulse (Securing personal data? Clouds are not all the same...) Twitter: @WD_PR_Guru

90. "To avoid Facebook, Twitter and other social media scams, beware of any prize that appears too good too be true. Always check the original page and assess factors such as, are they a respected organisation? Do they have adequate likes? Do they post often? Are their posts free from spelling errors?" - Elli Summers, Social Media Monitors (How to Identify an Online Scam) Twitter: @SMediaMonitors
91. "One example is the untrue story that some maniac is placing HIV-infected needles in the coin returns of public pay phones which unsuspecting people discover by accident--after they've pricked their fingers checking for returned coins. As realistic and frightening as this may sound, before forwarding it to everyone in your address book, take a little time to verify its authenticity. To me, the most annoying aspect of these emails is not so much their falsehood (though that's bad enough) as that they're forwarded repeatedly by completely naïve folks. With a little information, however, you can overcome this naïveté." - Rev. Michael L. White, ParsonPlace.com (Scam Spam: Identifying Those Pesky Internet Hoaxes) Twitter: @parsonp
92. "IBM's X Force security researchers found an easy way to gain access to Web accounts by taking an advantage of an oversight in how some social login services are configured. Those services allow someone to login to a Web service using, for example, their LinkedIn credentials. It's a convenient way for users to create new accounts on websites by using existing information." - Jeremy Kirk, IDG News Service, CSO Online ('SpoofedMe' attacks exploited LinkedIn, Amazon social login flaws) Twitter: @CSOonline

93. "Social media offers important business advantages to companies and organizations, but also has well-known security risks. In order to mitigate these security risks and still enjoy the benefits of social media organizations must establish and enforce good social media usage policies. But many organizations are unsure of how to develop effective social media policies. Instead, many organizations either simply prohibit social media use altogether, or have no policy at all regarding social media use." - SANS Institute InfoSec Reading Room (Reducing the Risks of Social Media to Your Organization) Twitter: @SANSInstitute
94. "Social media is the modern Pandora's box: It has had a meteoric rise as a tool to interact and engage with customers, but also a dark underside, exposing companies to new types of risk. Almost two-thirds of companies surveyed say that social media is a significant or critical risk to their brand reputation, yet 60% of companies either never train their employees about their corporate social media policies or do so only upon hiring. Moreover, 43% of companies have less then one full-time equivalent (FTE) dedicated to managing social media risk." - Data Breach Today, white paper by Nexgate (Guarding the Social Gates) Twitter: @DataBreachToday
95. "Social media platforms such as Twitter, Facebook and LinkedIn increasingly are being used by enterprises to engage with customers, build their brands and communicate information to the rest of the world. But social media for enterprises isn't all about 'liking,' 'friending,' 'up-voting' or 'digging.' For organizations, there are real risks to using social media, ranging from damaging the brand to exposing proprietary information to inviting lawsuits." - Chris Nerney, NetworkWorld (5 top social media security threats) Twitter: @NetworkWorld
Data Security Quotes for Parents, Teens, and Kids

96. "Don't let your children risk your family's privacy. Make sure they know how to use the Internet safely. For younger children, install parental control software that limits the Web sites kids can visit. But remember - no software can substitute for parental supervision." - State of California Department of Justice, Office of the Attorney General (Protect Your Computer from Viruses, Hackers, and Spies) Twitter: @CalAGHarris
97. "Whether or not you wish to restrict your child’s Internet usage, parental controls work well for logging computer use. Most modern computers come with built-in parental controls, or try a third-party solution." - LavaSoft.com (Back to School Online Safety Tips) Twitter: @Lavasoft
98. "Talk to your kids. Watch your kids. Consistent parental involvement is the best protection kids have against online risks. Educate yourself and talk to your kids about proper online behavior. Limit the risks further by installing parental controls that allow you to set criteria for Internet content, programs used, time spent online, and online chat partners." - Constant Guard by Xfinity (Top 10 things you should do to protect yourself) Twitter: @XFINITY
99. "My Talking Tom is a game where you raise a virtual cat. The gimmick: You speak to him, and he repeats everything you say. But the app takes your voice recordings, and shares that data with advertisers. And if you connect your phone to a computer, it can delete or modify files on that computer -- for a reason CMU researchers can't yet figure out. Update: The makers of Talking Tom reject the findings, saying no personal information or recordings are shared with advertisers. And it only has access to connected computers so that users' videos can be saved." - Jose Pagliery, CNN Money (Apps aimed at children collect a shocking amount of data) Twitter: @CNNMoney

100. "From cyber bullying to sexting to prowling predators, the Information Age has brought with it a new spectrum of risks and threats for parents to guard their children against, and now that spectrum of threats has expanded to include child identity theft." - Richard Power, Distinguished Fellow, Carnegie Mellon CyLab (Child Identity Theft) Twitter: @cylab
101. "There are some cases that appear to be identity theft but are not. Receiving a pre-approved credit card offer in your child’s name might upset you as a parent. However, it might only be an innocent marketing tool sent by an affiliate of your bank because you opened a college fund for your child. (Please refer to ITRC Fact Sheet FS 120B – A Guide for Parents – Child Identity Theft Indicators.) A quick check of credit reports will help you sort out the truth. Currently, all three reporting agencies use automated systems for ordering credit reports. You should contact them directly and request a credit report for your child. If you are told that there is no credit report, that is good news. The reality is that a credit report should not exist until that child’s first credit application as an adult." - Identity Theft Resource Center (ITRC Fact Sheet 120 Identity Theft and Children) Twitter: @ITRCSD
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.