Threat Hunting with MITRE’s ATT&CK Framework Part 2 – Advanced Use Cases
| Contact Us | |
| Free Demo | |
| Chat | |
In part two of a three part series, Tim Bandos, Digital Guardian's VP of Cybersecurity, describes how to best leverage MITRE's Attack Framework for threat hunting.
If you haven’t gotten a chance already, please check out Part 1 of this series for a basic overview of leveraging MITRE’s ATT&CK framework for threat hunting. If you have done this, then welcome to the major leagues. Let’s have some fun and drill into some more advanced threat hunting uses cases to seek out evil.
Let me introduce you to my playground shown below. Yes, my playground has 42 million alarms for one of our customers with close to 48,000 endpoints but I’m not scared. Keep in mind from our prior post, these alarms aren’t all bad. These alarms are intended to enrich the data. Making it easier for us to pivot, search, slice, and dice. In today’s blog, I’d like to walk through three hunting use cases: Command & Control, Lateral Movement, and Data Exfiltration.
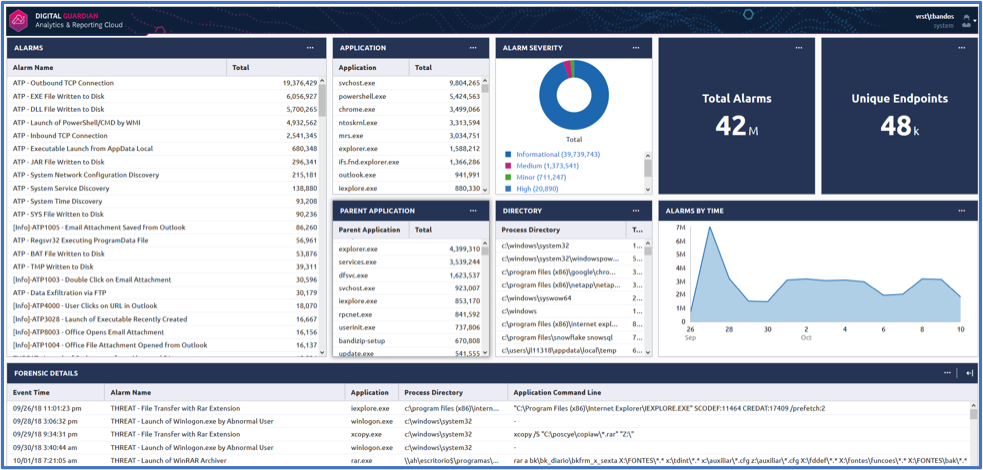
Hunting for Command & Control

Let’s start off with selecting a couple of techniques from the ATT&CK Framework to hunt for Command and Control activity; aka malicious network traffic. Our top hitting alarm, ATP – Outbound TCP Connections, will show all outbound connections made by process. Although close to 20 million hits is a lot, we can whittle it down by looking at alarms that are mapped to one of the Command & Control techniques: Uncommonly Used Ports.
First we’ll look at a table with remote outbound port connections that triggered our ATP – Uncommonly Used Ports rule by frequency and scroll toward the bottom to look for some of the outliers/unique binaries making these connections.
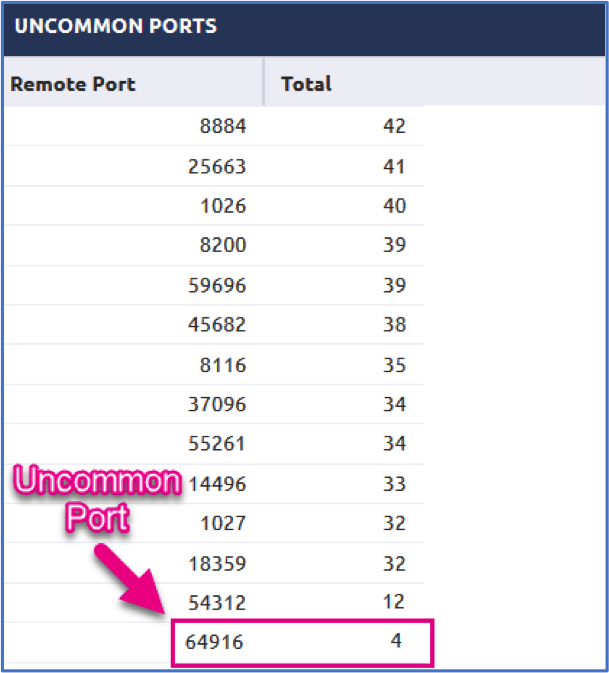
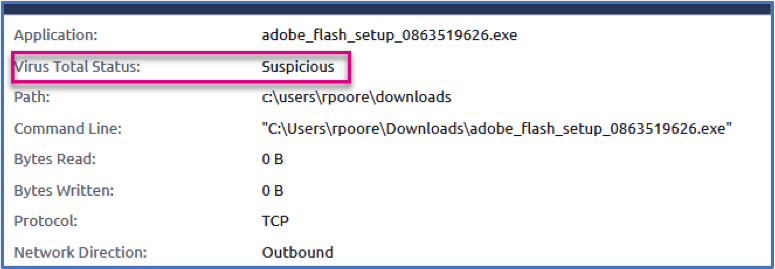
The first thing that piques my interest is the 64916 port which is linked to a binary named adobe_flash_setup_0863519626.exe. We’ve probably all seen this trick - where executables are attempted to be named as legitimate applications to fool the end user - a boatload of times. Throwing a large number on the end totally defeats that purpose and makes a hunter question it even more!
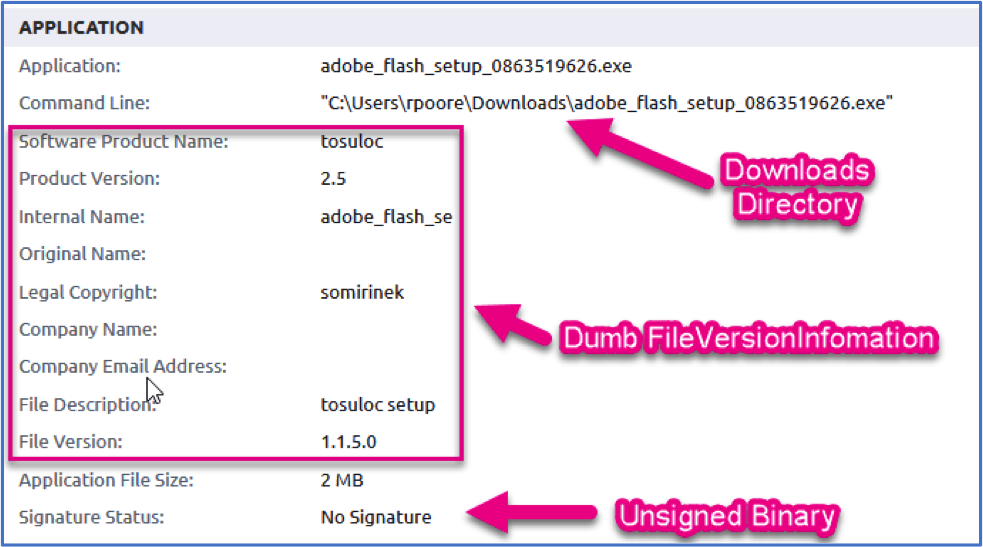
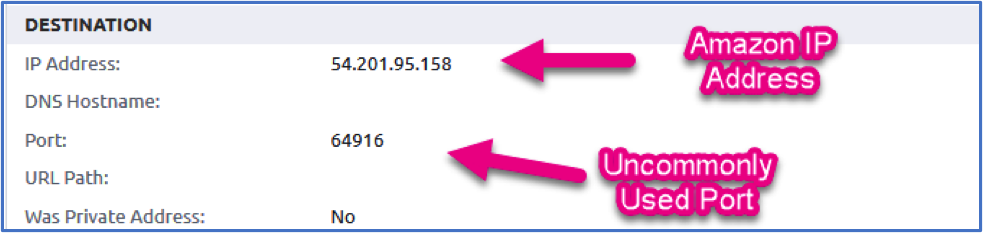
Taking a peek at the binary’s metadata, the plot begins to thicken. The end user clearly downloaded this directly from the web (hence the Downloads directory shown in the metadata below), there’s a bunch of odd FileVersionInformation, and it’s unsigned. As mentioned, the network connection made was directly to an IP Address over an Uncommonly Used Port that is owned by Amazon; malware’s best friend.
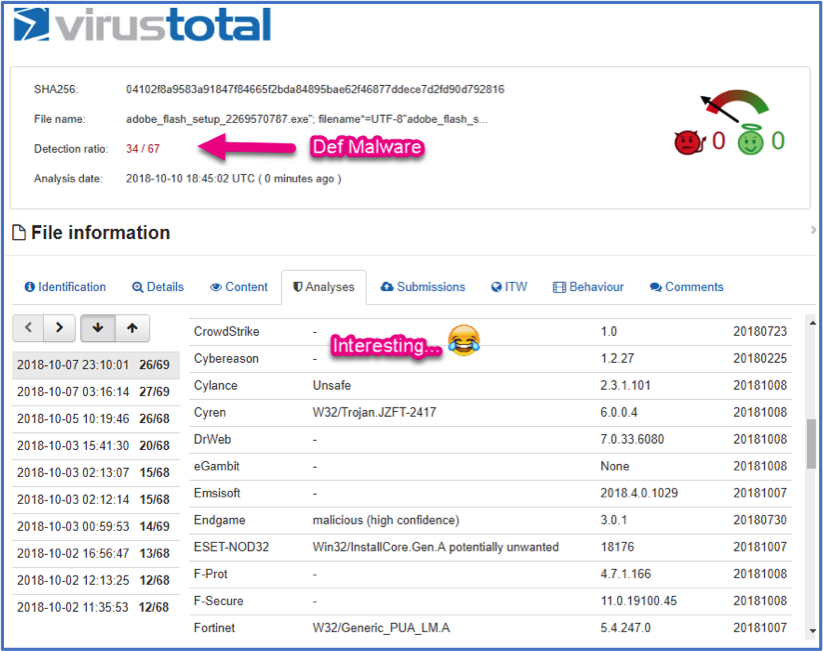
We discovered this relatively quickly during the hunt but I could have just cheated on this particular one and looked at any of the threat feed integrations like VirusTotal to see if there were any known malware hits; as it turns out there are. VirusTotal has a detection ratio of 34 out of 67 for this being a malicious file. Below shows the VT report along with the vendors that have marked it as such.
But leveraging VirusTotal is not the mission.
Not all hashes are going to be known and we need to assume this out the gate if we’re going to truly find the hidden infections.
Hunting for Lateral Movement
Hunting for Lateral Movement activity is one of my favorite techniques to identify. Coming across this type of behavior always gives me an ‘Uh Oh’ moment. I may use some different vernacular there but the feeling is the same! This is the stage at which the adversary has successfully penetrated your environment’s defenses, a backdoor has most likely been established, and they are now scoping out the lay of land looking for treasure - your data! One of the most effective methods I’ve used for years is baselining PsExec activity. PsExec is a remote administration tool and has been observed across many threat actor groups as being one of the tools of choice for conducting lateral movement. Why? Because it’s a legitimate, Microsoft signed tool which allows them to blend in.
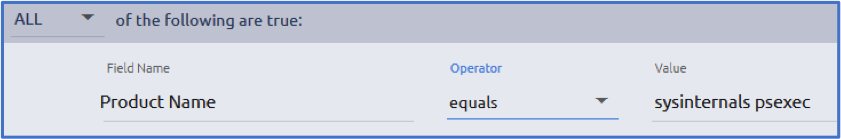
For this analysis, we’re going to look at a few key fields. The process path, process name, and command line being executed. First though, we need to set up a filter on our data. The most effective way of doing that is leveraging the Product Name field within the executable’s metadata. This will help to identify renamed tools as well to trigger and track down Defense Evasion techniques such as Masquerading.
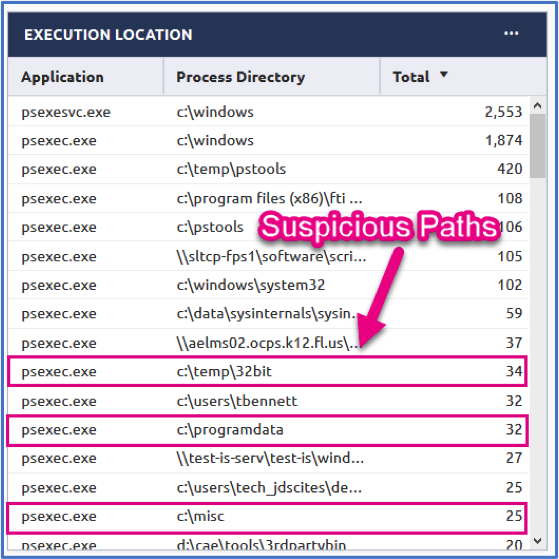
Process Path: The path by which a program runs can be quite relevant when it comes to threat hunting. Executing tools out of their standard locations isn’t cool so the bad guys create their own little hidden folders on the endpoint to be slick and remain clandestine. Aggregating on the process path may yield a few suspicious directories that require some additional investigation. Below, we see psexec.exe running from a c:\temp\32bit, c:\programdata, and a c:\misc. Those are all odd and should be further analyzed. Note: The c:\temp\pstools shown below is typically your savvy IT guy, but always good to double check on that one as well!
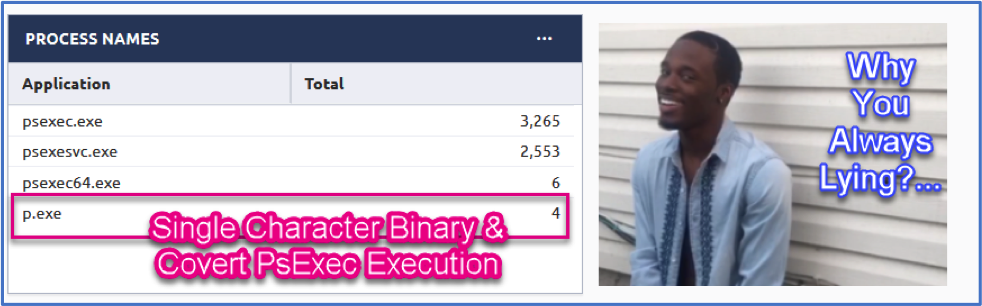
Process Name: The process name may, or may not indicate suspicious behavior but threat actors love to rename their toolsets and are super lazy on the command line. They love single character and two character binary names since it’s less to type. In the picture below we see a p.exe. Yikes… in this case, someone is covertly running the psexec tool or Masquerading.
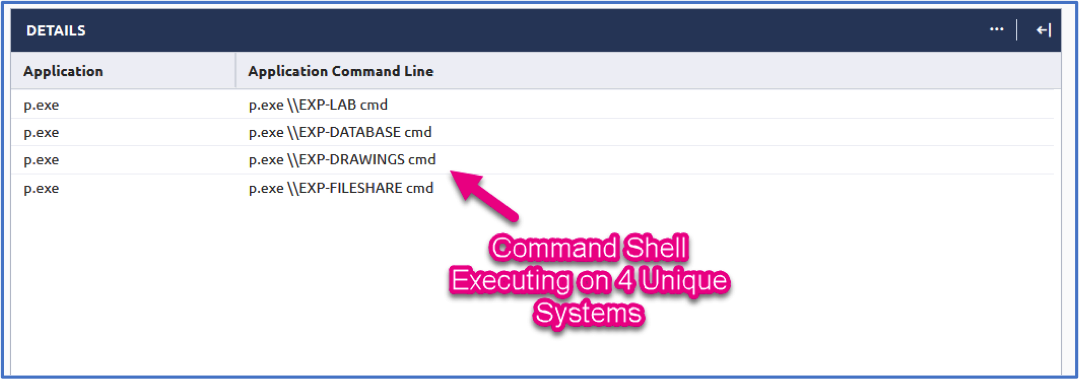
Command Line: Looking at the commands that are being executed by PsExec can be insightful as well. In this case we’re going to want to immediately check out what p.exe is up too. From the table below, we see that psexec is spawning a remote command shell on four unique systems. This is when I take a deep breath and get secretly excited. There can be an explanation for this but this is very strange to see and would require some additional looking into.
10 minutes later after looking into... Confirmed lateral movement. Blue Team Engaged...

And yes that’s a yellow TK35u-RW Forensic Bridge Kit in his hand. Never leaves my side.
When confirming whether or not Lateral Movement is malicious, it’s good to conduct a ‘look around’ for everything that is executing around that time. Once a threat is on a box, they’ll engage in several additional techniques outlined within MITRE’s framework. Look for some of these types of commands being executed:
Account Discovery – net user, net group
System Network Configuration Discovery - ipconfig /all, arp -a, nbtstat -n
File and Directory Discovery - dir
Remote File Copy – look for commands transferring additional tools/binaries to a machine
Data Staged – look for data being compressed and staged in directories via the command line
Etc.
Having these signatures pre-defined and applied to your data will make this task simple when you’re seeing a ton of ATT&CK techniques triggering on a device during the lateral movement phase.
Hunting for Data Exfiltration

Since Digital Guardian is known for being a DLP company, it of course makes sense to also highlight data exfiltration hunting! This hunting technique will come down to the types of tools and visibility you have in your own environment as it relates to outbound data egress, but I’d like to highlight the importance of being able to track data movement by process in this exercise to search for suspicious behavior.
The first place I like to take a look at are my top talkers…
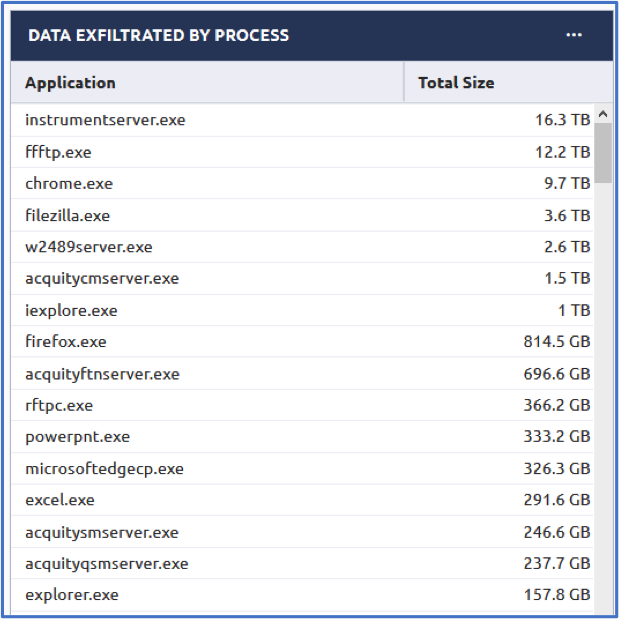
Above you’ll see a chart of the processes that are sending data outbound aggregated by total size. The first one that jumps out would be that ffftp.exe program since it’s oddly named but as it turns out, it’s legitimate (#boring). Each of these processes can be broken down even further as well by items like Source File Extension, if searching for archives being exfiltrated, or even process directory which can be interesting if they’re ran from suspicious locations. Scrolling a bit further down the list though we come across curl.exe. Curl is typically used for transferring data with URLs but it supports a variety of protocols making it a pretty clever tool to leverage for data exfiltration and seeing over a gigabyte and a half leaving the network is rather peculiar.
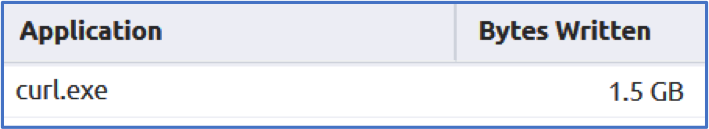
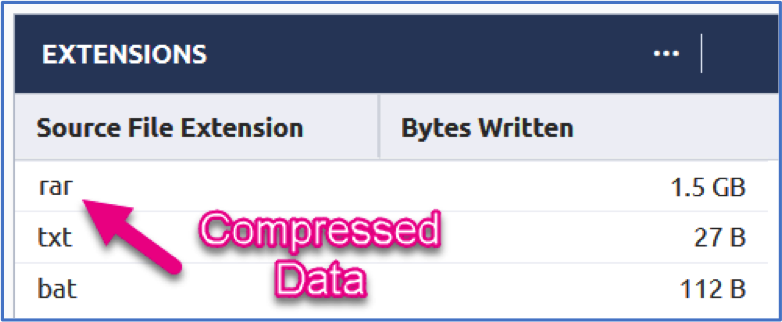
The file extensions associated with this activity includes ‘rar’ which I always feel is pretty threat-actor-esque and lines up with one of our MITRE ATT&CK stages for Data Compressed. Not all compressed data leaving the network is bad but tagging this activity with rules will help speed up the hunt process to zero in on possible exfiltration.
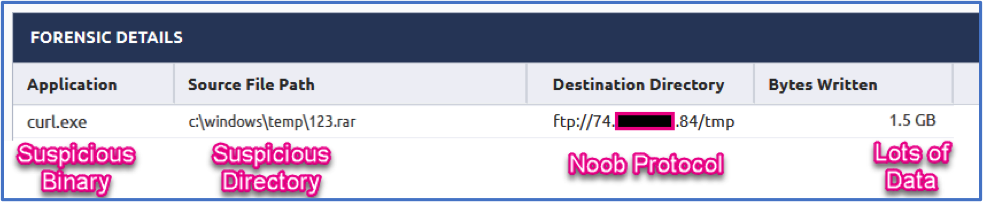
Looking at the forensic details for this event, we see the source file is named 123.rar and it’s going directly to an IP address (forgive the redaction) over FTP. Not sure if it gets any easier than this. Threat actors will commonly stage their data in a hidden or temporary directory so seeing this paired with the lazy naming convention of that file is enough to sound the alarms.
Data exfiltration hunting isn’t always going to be this effortless, but developing signatures to detect various types of events such as the one above will make your hunt a bit easier, especially when you’re able to pair this information with source process name/directory/command line etc. I remember back in the day when only being able to hunt through web proxy logs. If you found something interesting, you’d have to go through the rigamarole of tracking it back to a specific machine, then back to a process, etc. and it just took so much extra time investigating.
A couple other tips to look for when it comes to data exfiltration include:
- Destination Domains being dynamic DNS Sites
- Source file extensions equal .rar, .7z, .zip, .tar, .cab, etc. (be careful here because this is easy to obfuscate with an extension name change)
- Protocols such as FTP, SFTP, SCP, SSH
- Tor traffic/domains
This concludes our second installment of Threat Hunting with MITRE’S ATT&CK framework. I hope this was helpful in demonstrating how to at least begin leveraging the framework for threat hunting purposes and some of the key areas to focus on right out the gate. For our third and final chapter - Part 3 - I'll be exploring the higher fidelity phases that will often lead to the identification of a compromise.

Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.