Paid in Full: Why the MICROS Data Breach Could be More than Meets the Eye
Data breaches come in all shapes and sizes. Some, like the attacks on Target and Home Depot, are big, public, and expensive. Others can be small and quiet, but no less expensive in the long run.
Ransomware Protection & Removal: How Businesses Can Best Defend Against Ransomware Attacks
What steps should businesses take for ransomware protection? 44 security experts weigh in.
What is Advanced Threat Protection (ATP)?
Learn more about advanced threat protection solutions and services in Data Protection 101, our series on the fundamentals of data security.
Getting Successful with DLP: Two Approaches for Quick DLP Wins
While once considered a headache, deploying DLP no longer needs to be a months-long, complex process. Part 11 of our Definitive Guide to DLP series offers two approaches to getting “quick wins” when starting your DLP program.
What is Threat Intelligence? Finding the Right Threat Intelligence Sources for Your Organization
Learn more about the different approaches to threat intelligence in Data Protection 101, our series on the fundamentals of data security.
How to Evaluate DLP Solutions: 6 Steps to Follow and 10 Questions to Ask
Evaluating and selecting a new solution is always an undertaking, but following a standard framework and criteria set for each solution you’re considering will help simplify the process. Part 10 of our "Definitive Guide to Data Loss Prevention" series provides six steps and ten criteria to guide this process.
Obama Details Federal Cyber Attack Response Plan
Yesterday saw the release of a new Presidential Policy Directive for government cyber attack response. Read on for more about this milestone in federal cybersecurity policy.
Insider vs. Outsider Data Security Threats: What’s the Greater Risk?
47 data security experts compare the risks of insider threats vs. outsider threats.
What is Malvertising? How to Identify and Protect Against Malvertising Attacks
How does malvertising affect companies and individuals differently? Learn how to identify and avoid malvertisements in Data Protection 101, our series on the fundamentals of information security.
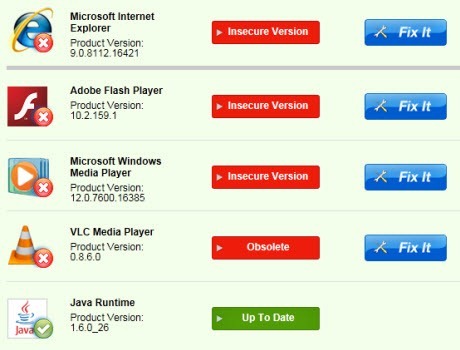
Kicking Plugins to the Curb in the Name of Security
For many years, the web browser has been the most dangerous piece of software on a computer. They have blindly trusted the content served to them by virtually any site, allowed users to be hit by all manner of malware and drive-by downloads and generally been that friend you don’t want to follow down a sketchy side street.
Don't Fall Behind
Get the latest security insights
delivered to your inbox each week.