What is Data Discovery?
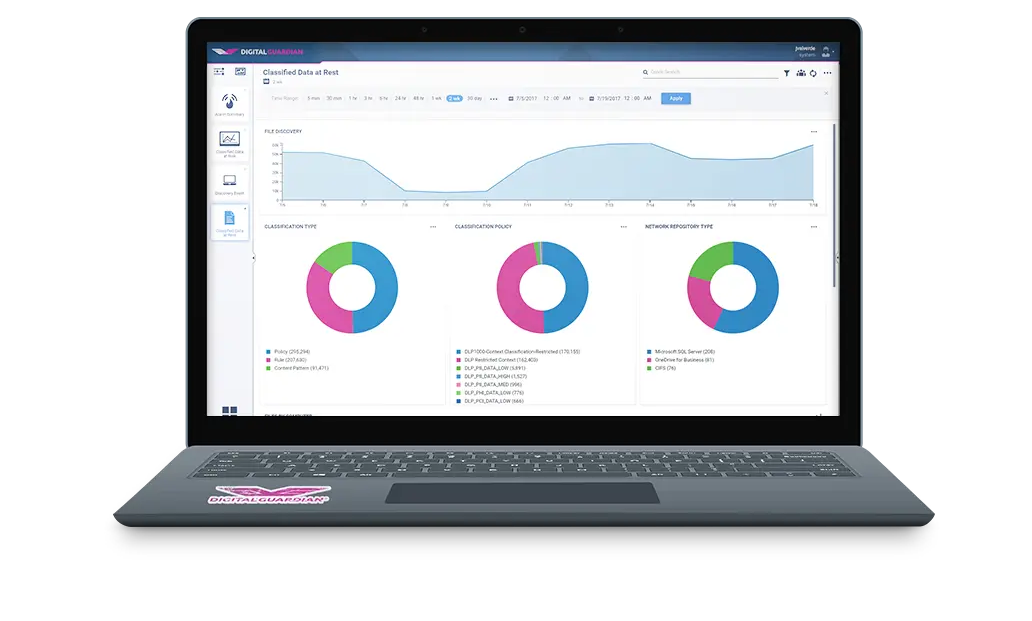
You can’t protect what you can’t find. Digital Guardian for Data Discovery provides visibility and auditing of sensitive data at rest across the enterprise.
Our data discovery appliance uses automatic, configurable scanning of local and network shares using discovery specific inspection policies to find sensitive data wherever it is located. Detailed audit logging and reports provide you with the information needed to demonstrate compliance, protect confidential information and reduce data loss risk.
Key Benefits
Why Digital Guardian?
RAPID DEPLOYMENT AND EASE OF MANAGEMENT
Digital Guardian appliances speed deployment and reduce ongoing maintenance efforts as infosec teams run leaner. Our appliances ship with pre-configured policies to locate common data types including PII, PHI, and PCI, and can be inserted into the existing infrastructure with minimal configuration.
ACCURATE DISCOVERY AND CLASSIFICATION OF SENSITIVE DATA
Digital Guardians Database Record Matching (DBRM) delivers the accuracy needed to reduce false positives and false negatives. DBRM recognizes and registers a wide range of both structured (fields in databases or columns in spreadsheets) and unstructured data (document formats such as Microsoft Office, source code and PDF files) reducing false positives and false negatives during the data discovery process.
INTEGRATION WITH ENTERPRISE DLP
Data Discovery integrates with the Digital Guardian platform to locate and protect sensitive or regulated information in the cloud and on-premises, including laptops, servers and databases.
Schedule a Demo
See how Digital Guardian can help protect your critical data wherever it lives.
Works With Your Existing Security Tools




