Cloud computing is quickly becoming a mainstay for many businesses today because of its superior flexibility, accessibility, and capacity compared to traditional computing and storage methods. But just like traditional storage and data sharing methods, cloud computing comes with its own set of data security issues. In some cases, concerns over cloud security risks can stifle cloud adoption, robbing organizations of the numerous benefits brought by the cloud. In fact, a recent RightScale report found security to be the top cloud concern amongst IT professionals.
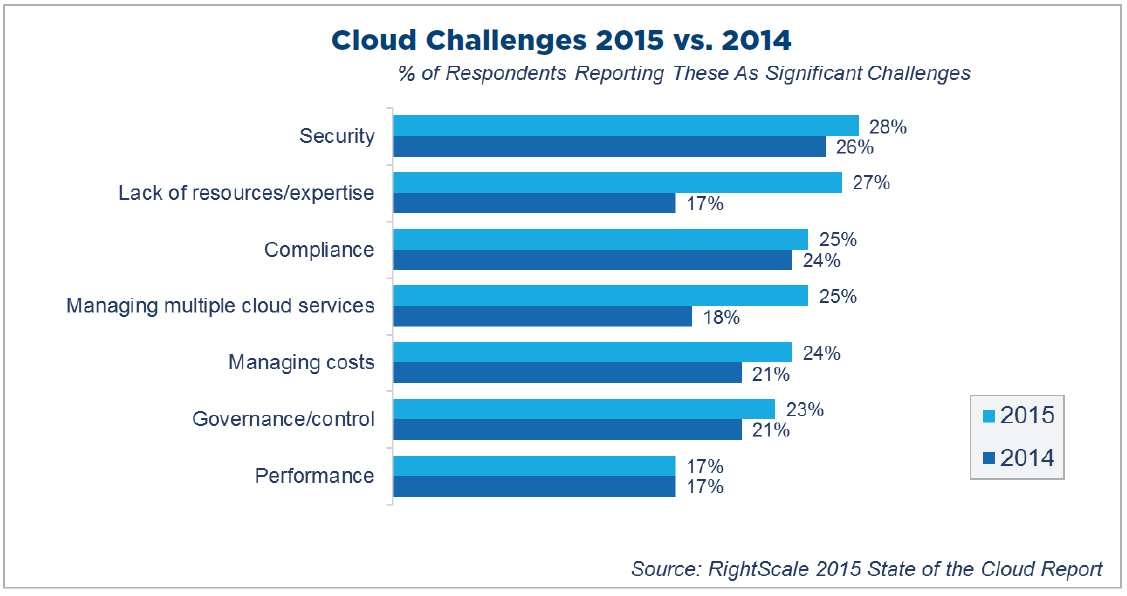
Security was the top cloud challenge amongst IT professionals in both 2014 and 2015. Image via RightScale.
While cloud adoption can seem like a daunting undertaking, starting with a thorough plan and taking a pragmatic, data-centric approach to implementing cloud security measures will make the process manageable and achievable for security teams. This blog post provides an 8 step framework that organizations can follow to build an effective cloud security program.
1. Do your homework
Before selecting a cloud service provider, conduct due diligence to understand:
- What types of data will be uploaded to the cloud and the sensitivity of that data (as well as if any of that data is subject to specific regulations like PCI, HIPAA, HITECH, etc)
-
The security measures that provider has in place. Secure cloud providers should offer:
- Data encryption at rest and in transit – providers should be FIPS 140-2 certified for data in storage and use HTTPS for data in transit
- Secure mechanisms for access control such as two factor/multi factor authentication
- Results from independent security audits to validate the adequacy of the provider’s security measures
- Compliance certifications such as HIPAA/HITECH, PCI-DSS, Cloud Security Alliance Cloud Controls Matrix, and Safe Harbor
- The provider’s terms and conditions for privacy, data ownership, customer support, compliance with any applicable regulations, and policies for data breach liability, notification, and response
- How the cloud will change or impact current business processes
There are several reputable, industry standard resources that companies can use to evaluate the efficacy of cloud providers’ security. Use frameworks like ISO 27002 or the Cloud Security Alliance’s Cloud Controls Matrix to validate your own findings and get an authoritative evaluation of cloud vendor security.
2. Secure the endpoints that will access cloud applications
Cloud applications live outside of your IT environment, outside of the protection provided by many network- or perimeter-based security technologies. Prior to using cloud storage or services, it is critical to secure the devices that will be used to access the cloud. Those endpoints should be protected with controls for data exfiltration, end-to-end encryption, and secure access. By doing so you will prevent the unauthorized upload of sensitive data to the cloud, or at the very least ensure that data is encrypted prior to upload. Data should remain encrypted in the cloud and decrypted only when it has reached an authorized user’s device.
Once data reaches the cloud, it is no longer within your direct control, so encrypting sensitive data or preventing upload of certain data types is critical to keeping that information out of criminals’ reach.
3. Monitor access to cloud data and services
Visibility into data access and usage is critical to effectively securing that data. In addition to securing the endpoints that will be used to access cloud data, make sure that you have visibility into who is accessing the cloud as well as what data they are uploading to or downloading from the cloud. This visibility will increase the effectiveness of your endpoint security controls and enable your security team to quickly detect and respond to risky behavior involving cloud data, whether that behavior comes from insiders such as employees or outside intruders who have compromised your systems to gain access.
4. Leverage cloud APIs to extend data protection measures
If your organization is going to allow use of cloud-based email or storage services (such as Box, Egnyte, ShareFile, or Dropbox), leverage providers’ APIs to extend existing data protection measures to those platforms. Doing so can improve visibility over cloud data access and enable better control – such as encryption or access control – over data that is stored in the cloud. Many network security appliances offer cloud integrations via APIs, so ask your providers which cloud platforms they integrate with and take advantage of these features where available.
5. Secure your cloud applications
Beyond endpoints and networks, cloud security also hinges on the security of the applications running in the cloud. Far too often, security takes a back seat to form and function in cloud application development – particularly for cloud applications that are produced by single developers or small teams.
Test your own cloud applications for commonly exploited security vulnerabilities, and require third party cloud application providers to share the results of application security testing (such as static or dynamic analysis or penetration testing) performed on their own software. Any vulnerabilities discovered in the application testing process should be securely patched before those applications are used.
6. Implement policies and controls to secure BYOD cloud usage
If you’re going to allow access to cloud data via employee-owned mobile devices (whether laptops, smartphones, or tablets), it is imperative that you first create a BYOD policy and implement controls to enforce proper data access and usage by BYOD users. Consider using two-factor authentication, end-to-end encryption, and mobile device management (MDM) software to secure BYOD usage in the cloud. Two-factor authentication helps to prevent unauthorized access, while encryption will ensure that any sensitive cloud data accessed by BYOD users is only viewable by authorized parties. Mobile device management software is a good last line of defense if a device is lost or stolen, as MDM enables IT departments to restrict BYOD access or wipe a device remotely if necessary.
7. Perform routine backups of your cloud data
As cloud providers and applications are increasingly targeted in cyber attacks, companies must prepare for the worst-case scenario: permanent loss of cloud-stored data. While it won’t protect you from many of the costs of a data breach such as financial losses, brand damage, or regulatory penalties, performing regular data backups will at the very least ensure that you can recover any critical data lost in a cloud data breach, ransomware attack, or destructive malware infection. Make data backups a frequent and regular process prior to transitioning to the cloud.
8. Provide ongoing employee security awareness training to teach and reinforce good cloud security hygiene
No matter how secure your endpoints, applications, and network connections are, you’re ultimately only as secure as the users that are operating them. Social engineering tactics like spear phishing remain among the most common, simplest, and successful methods used by cyber criminals. Ongoing security training is critical to ensure that employees can effectively recognize and avoid social engineering attacks and build secure web habits. Conduct simulated social engineering attacks periodically to gauge your employees’ ability to recognize and avoid them.
