Threat hunting is in high demand as many enterprise security teams are looking to leverage their expertise, analytical skills, and visibility into data activity to proactively discover advanced threats capable of evading detection by legacy security technologies like antivirus or firewalls. But where do you begin?
Understanding cyber threats
The video clip below is taken from our webinar, Cyber Hunting Safety, and will help you understand how to classify a threat.
Getting started hunting for threats requires that you have a strong understanding of the nature of today’s cyber threats. Put simply, to qualify as a threat, three factors must be present: intent, capability, and opportunity:
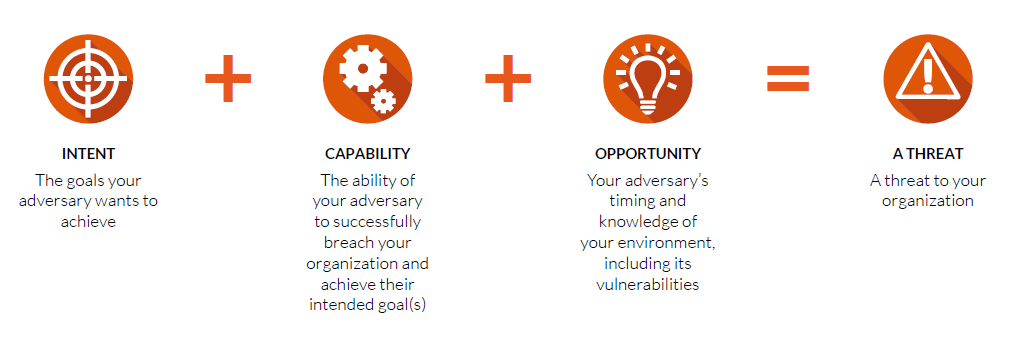
While you could argue that the intent factor remains relatively constant over time, there is plenty of evidence that threat actors’ capabilities and their opportunities to use them have grown dramatically in recent years. Adversaries are more skilled and persistent than ever, constantly finding new methods of attack to keep ahead of defenses. What’s more, trends like BYOD, cloud file sharing, and remote/mobile workforces mean that there are more opportunities for threat actors than ever before.
Lifecycle of a cyber threat
Successful threat hunting also requires an understanding of the typical life cycle of a cyber threat. This lifecycle can include up to 8 stages:
- Infiltration: identification and exploitation of a vulnerability to penetrate defenses
- Backdoor installation: malware is installed on targeted system(s)
- Command & control: communication is established between the malware and the adversary
- Execution: malware payload executes
- Persistence: in some attacks, the malware/threat actor will remain on the compromised system to maintain a foothold for future attacks
- Escalation of privileges: some attacks require threat actors to obtain a higher level of user permissions to gain control of a system
- Lateral movement: threat actors or malware will move from one system to the next
- Exfiltration: final removal of data to an external location under the attacker’s control
Why hunt for threats?
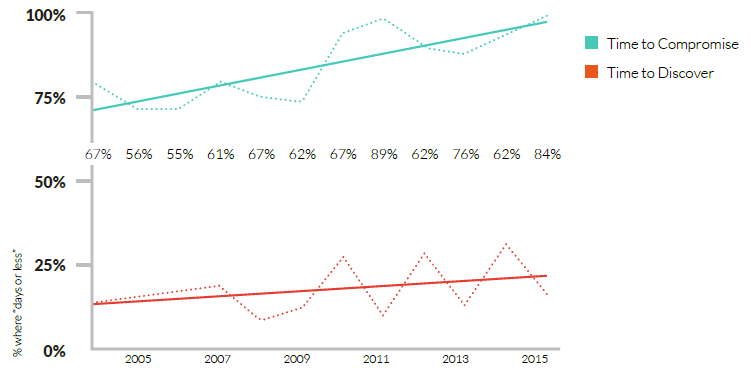
Advanced cyber attacks are sophisticated, targeted and difficult to detect. As shown in Verizon’s latest Data Breach Investigations Report, time to compromise is almost always less than the time to discover. The trends suggest that 70%-90% of all malware reported was unique to an organization and companies on an average went more than 200 days between the time they were breached and the day they discovered it. From the report:
3 fundamentals of threat intelligence for successful threat hunting
The success of your threat hunting efforts will depend on a few factors: chief among them are your level of in-house expertise and visibility into data activity as well as the depth and quality of your threat intelligence. Organizations will vary widely in terms of in-house expertise and data visibility, so let’s focus on the threat intelligence component for now.
Threat intelligence can be defined as knowledge about the tools, tactics, and procedures used by adversaries. Threat intelligence is used to qualify potential threats through the dissemination of this information to security monitoring devices for detection and prevention. The concept of threat intelligence is a little abstract though, and quite honestly could have an entire guide by itself. However, we can break it down into three fundamental pieces:
- Indicators of compromise (IOCs): these are artifacts (IP addresses, domains, file hashes, etc.) that have been linked with a certain level of confidence to an intrusion.
- Threat research and analysis: this component includes statistics, write-ups, analysis of malware, etc. to assist incident responders in detecting patterns of an attack.
- Tactics, techniques, and procedures (TTPs): these describe the specific motivations, intentions, and capabilities of an adversary. When profiling threat actor groups, it’s important to identify these traits to improve overall defenses within the organization.
No matter the size of your company or number of endpoints you’re protecting, it’s critical to leverage threat intelligence to assist in providing context to alerts and deploying indicators to security devices for preventing successful cyber intrusions. Depending on the available resources and budget an organization has, it’s relatively easy to stand up a threat intelligence database that houses indicators of compromise, TTPs, and your malware samples at minimal to no cost.
My budget was thin at my last job so I literally used a spare laptop with 8 gigabytes of memory, installed Ubuntu, and stood up a CRITS instance to manage our intel. Total time: 20 minutes. From there I identified some external Threat feeds like AlienVault, ThreatConnect, etc and ingested them into the solution. You can also use a tool called CIF (Collective Intelligence Framework) that’ll automate the process of pulling in threat feed data and will come with a bunch of sources already out of the box. You’ll discover, though, that some of the BEST threat intel is derived internally from your own incidents.
Get more threat hunting tips in our guide, Stop Security Threats to Your Organization.

