Malware spread through USB devices poses a serious challenge for security teams due to its difficulty to detect and contain. It is also a well-known technique to trick end users into – often unknowingly – introducing malware into a corporation’s network. The infamous Stuxnet malware is believed to have been introduced to its industrial control system targets via USB. USB malware attacks even made it to mainstream media last year in a scene from the acclaimed TV show Mr. Robot in which the hackers litter a prison parking lot with infected USB sticks in hopes that an unsuspecting employee will insert one into their computer.

Infected USB sticks in the parking lot of a prison in Episode 6 of Mr. Robot.
Our managed security team recently identified a Trojan that is using USB devices to self-propagate in the wild – this was a real attack on a customer device that we were able to detect and mitigate. What makes this malware particularly pernicious is its ability to avoid detection by the AV software installed on the customer’s devices. Here’s how the Trojan works and what can be done to contain an attack.
This attack starts with the Trojan attempting to infect the user’s machine. This could happen through a number of means, including the user opening infected attachments in phishing emails, downloading infected files off the web, or – as in this case – connecting an infected device to their computer.
The Trojan avoids detection by masquerading as a common image viewer. Once deployed, the Trojan hides itself by creating an application called “Windows Photo Viewer” – a spoofed version of the built-in Windows utility – in the user’s roaming profile and linking the application in the startup menu.
In this particular case, the DG Advanced Threat Protection solution was deployed to the host in November, at which time the incident was declared and mitigated. Prior to ATP deployment, the customer was already running the DG agent in “monitor-only” mode. Because of this, the managed security team was able to review forensic logs to identify the initial attack vector and infection sequence. For the sake of this post, we’ll start our analysis of the attack with the ATP solution’s discovery of the attack and work backward from there to analyze the attack sequence.
The incident was initially established when the ATP solution detected a process being launched from the user’s roaming profile; once the process launched itself it immediately began to connect out to its C&C servers.
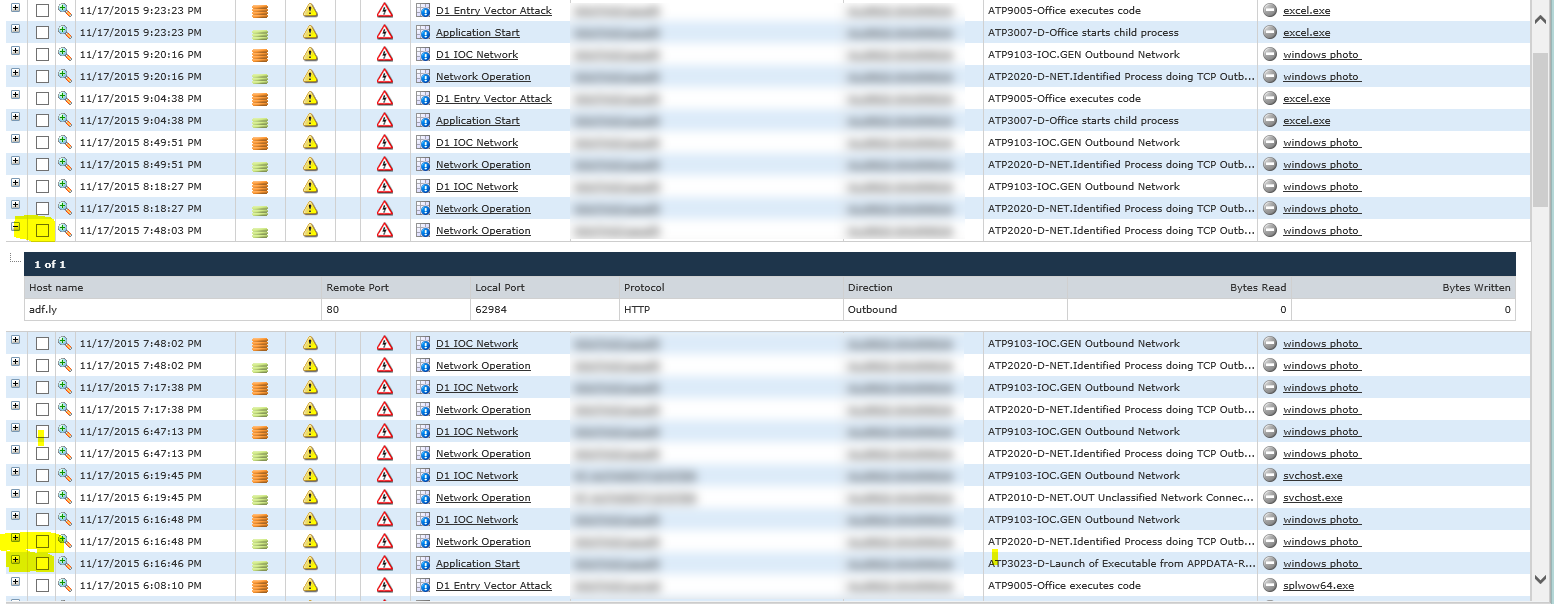
The analysis of these network artifacts shows the Windows Photo Trojan communicates out on common web ports, thus circumventing controlled Internet access via outbound proxies that this customer uses to control and monitor network traffic (hence the appearance of all traffic connecting to the same destination).
The Trojan attempts to connect to a short URL of hxxp://adf[.]ly/q33vd, which then tries to access multiple sites through redirection, including known malware hosts. We see the process re-launching itself multiple times during the captured events and continuously trying to get the next stages of the attack.
As part of the security team’s incident response process, and in order to establish a detailed timeline for the customer, the next step was to backtrack further through the event logs collected while in monitor-only mode (before ATP had been deployed).
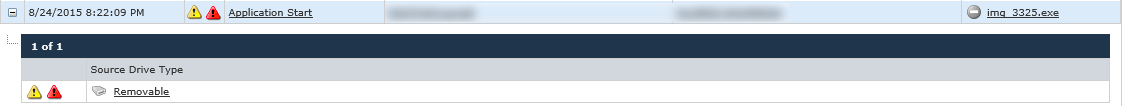
Through this analysis, the events showed that the Windows Photo Trojan was originally dropped when the user inserted an infected USB – most likely one that was being shared around the office without employees knowing that it contained malware. Going back, we can see the Trojan attempting to write itself to the user’s device from a USB:

The original Trojan is named “img_3325.exe” – an executable disguised as an image file. The first attempt is blocked, so the Trojan then attempts to launch directly from the USB:
A closer look at the executable:
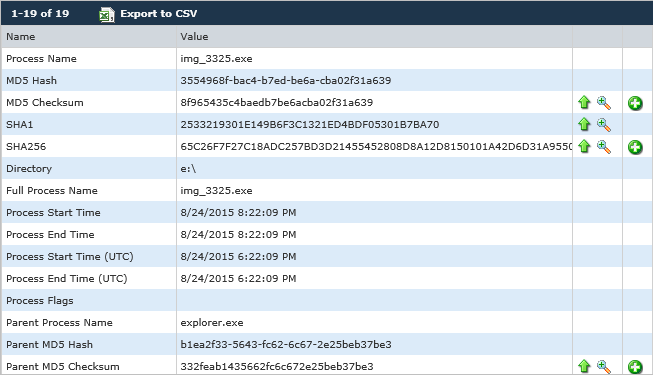
In this initial attempt, the launch attempts are also blocked as img_3325.exe was already identified as an unwanted application. From here we suspect that the infected USB drive may have contained a malicious link or a secondary launch mechanism like the user copying the PDF locally. That allowed the Trojan to deploy itself to the user’s device as a file named “Windows Photo Viewer.exe” – again masquerading as the Windows Photo Viewer software.
Due to the nature of the entry vector – an infected USB drive – a search was conducted to identify any proliferation of the attack. Through DG process reports, it was discovered that the process was seen on 29 distinct endpoints within the organization:
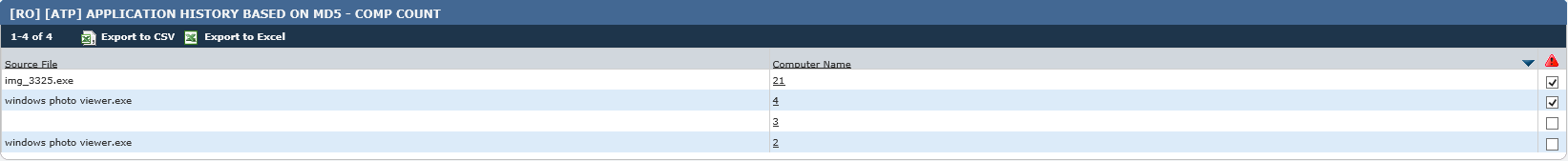
The list of host names and indicators were provided to the customer who was able to carry out full response and mitigation.
So what can organisations do to prevent and contain malware attacks that spread via removable media?
- Disable AutoRun functionality for removable media
- Educate your users on removable media risks and techniques for using removable media safely, such as holding down the SHIFT key while inserting any USB flash drive they have received from a third party to temporarily disable AutoRun
- If you decide to limit or outright block removable media usage are not required, consider deploying an endpoint security solution to enforce removable media usage policies, such as blocking executables from running of a USB device
While these attacks will continue to plague IT departments and security teams for some time to come, implementing a solution that provides the contextual awareness to recognize malware behavior in real time enables organizations to more effectively detect, contain, and mitigate these attacks. With the right combination of technological solutions and employee education, it is possible to use removable media safely – no hot glue required.
