The company impacted by last week’s ransomware incident, Colonial Pipeline, says it plans to have most of its pipeline operational by the end of the week.
If successful, it will mark a quick turnaround, especially after some reports suggested addressing the compromise could take weeks.
To ease the burden on the company, the United States over the weekend issued an emergency declaration to relax rules on the transportation of gasoline, diesel, jet fuel, and other refined petroleum to affected states. The attack, which happened on Friday, brought a major pipeline, the largest refined-products pipeline in the U.S., stretching from New Jersey to Texas, to a standstill.
The attack, carried out by the DarkSide ransomware-as-a-service crew, affects Colonial Pipeline, an Alpharetta, Georgia company that oversees a system that carries 2.5 million barrels a day, roughly 45 percent of fuel supplies for the Eastern US. Following the attack, approximately 5,000 miles of pipeline have been shut down.
The FBI confirmed on Monday that DarkSide was responsible for the pipeline attack, and that its continuing to work with the company and its government partners on the investigation.
At a press conference on Monday, Homeland Security Adviser Elizabeth Sherwood-Randall stressed that there's not currently a petroleum supply shortage and that the company has told the government it believes it bring its systems back online "relatively quickly."
Perhaps because of this, according to Sherwood-Randall, the company hasn't asked the government for cyber help, yet. In the same White House briefing, officials reported that Colonial shut down its systems before the ransomware could spread from its business IT systems to operational technology networks, something that sounds like it helped lessen the ransomware's impact as well.
Still, because of the significance of the compromise, the FBI issued a flash alert on Monday with indicators of compromise and mitigations for organizations to review.
In a press release on Monday, the company said it plans to substantially restore operational service across its pipeline by the end of the week and that its "executing a plan that involves an incremental process that will facilitate a return to service in a phased approach."
"Restoring our network to normal operations is a process that requires the diligent remediation of our systems, and this takes time. In response to the cybersecurity attack on our system, we proactively took certain systems offline to contain the threat, which temporarily halted all pipeline operations, and affected some of our IT systems. To restore service, we must work to ensure that each of these systems can be brought back online safely," the company wrote.
On Sunday, the company specified that because of the attack, its main lines are offline but that small, lateral lines between terminals and delivery points, presumably lines it runs as offshoots from Atlanta, Spartanburgh, SC, and Greensboro, NC, are still operational. Judging by the below map, that still leaves a vast swathe of the pipeline, including the length from Linden, New Jersey, to Houston, Texas, impacted.
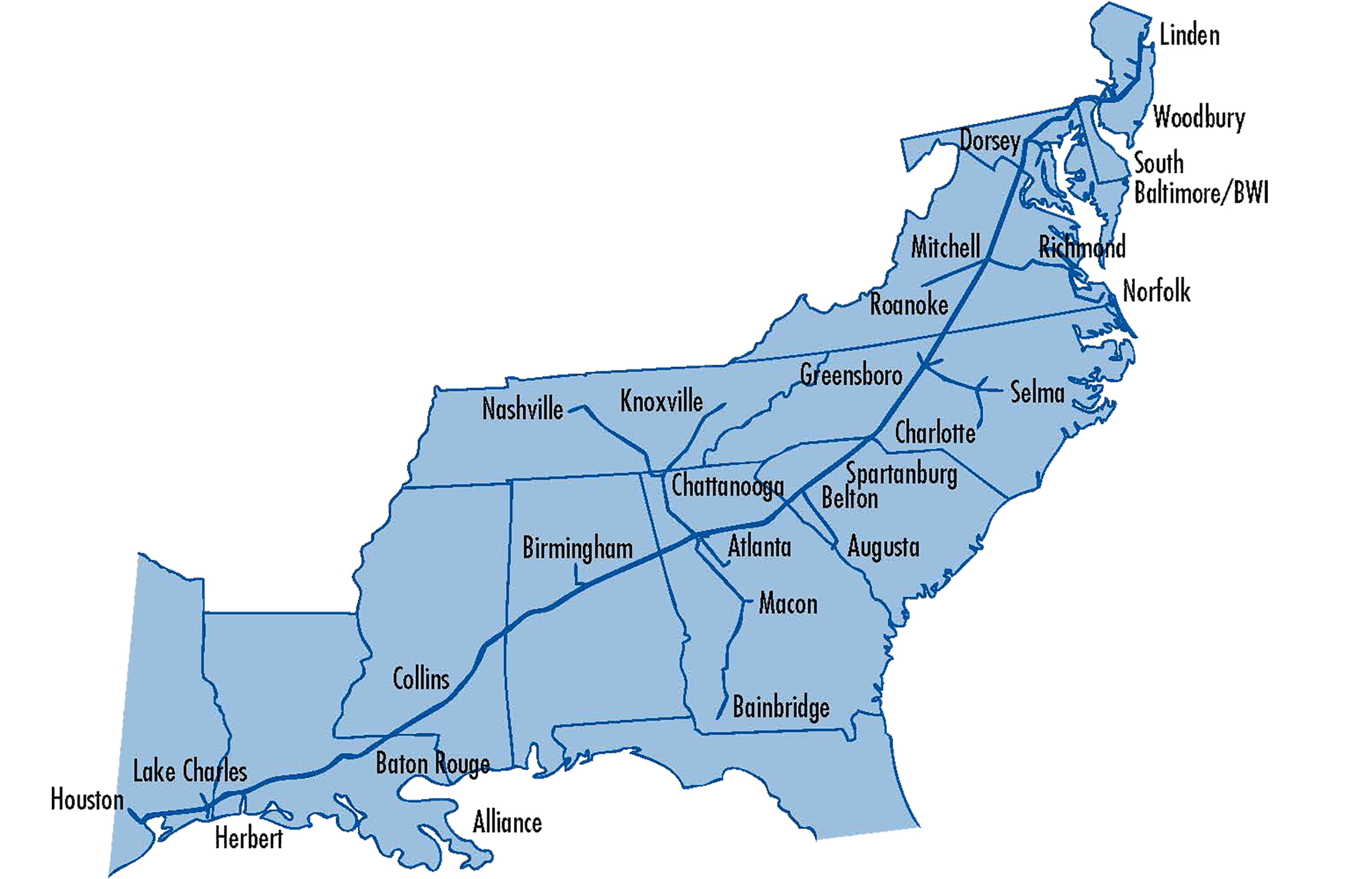
The emergency declaration, a temporary action taken by the Department of Transportation and Federal Motor Carrier Safety Administration (FMCSA), allows oil products to be transported across state lines via tankers. The emergency legislation also relaxes laws for drivers in 18 states - Alabama, Arkansas, Delaware, Florida, Georgia, Kentucky, Louisiana, Maryland, Mississippi, New Jersey, New York, North Carolina, Pennsylvania, South Carolina, Tennessee, Texas and Virginia, in addition to the District of Columbia - so they can work more flexible hours when transporting petroleum products.
The incident has also prompted emergency meetings at the White House as President Biden reportedly preps a cybersecurity executive order designed to strengthen federal agencies and contractors.
The group behind the ransomware posted a half-hearted notice on its dark web site Monday that its only goal behind the attack was to make money and ironically, not "creating problems for society." The group has previously gone on record stating that it doesn't target hospitals or hospices, school or universities, or non-profit organizations or organizations in the government sector.
The group has mostly been resolute in that stance. Its hit a variety of victims, including two of the largest power companies in Brazil, Eletobras and Copel, a Canadian car rental company, Discount, and a managed IT services company, CompuCom, but no big hospitals or schools.
Having an ethical code of sorts as to who the group will target certainly makes for an interesting ground to stand on but it mirrors the group's offbeat activity since it first surfaced last August.
In October, the group made headlines after donating thousands of dollars it received as part of ransom demands to charities, Children's International and The Water Project; the charities ultimately couldn't keep the funds as they were publicly announced and of course, illegally procured.
Still, the group had to have known that hacking one of the country's largest pipelines was going to get them attention, especially on a federal level. DarkSide's statement from Monday, which also claims the group will begin moderating and checking companies before they ransom them "to avoid social consequences," seems like hopeless backpedaling at best.
Interestingly, as a precursor to the attack, DarkSide infiltrated Colonial's network a day prior to the attack, on Thursday, and managed to exfiltrate almost 100 gigabytes of data. That's according to a report in Bloomberg, citing two people involved in the Colonial's investigation, late Saturday. Little else about the purported data theft has been reported and there’s no mention of it in Colonial Pipeline’s press releases.
The attack, just a few months after the water hack in Oldsmar, Florida that could have poisoned thousands, is another example that attacks targeting both IT and OT, operational technology, environments are becoming more prevalent.
Looking to learn more about Fortra's Digital Guardian?
Have a question about data loss prevention, secure collaboration, or SaaS data protection? Don't hesitate to get in touch. We're here to help.
