Two hackers, Amat Cama and Richard Zhu, working under the pseudonym Fluoroacetate, managed to hack a car - a first for Pwn2Own - Friday afternoon to close out the conference. The pair, targeting a Tesla Model 3's infotainment system, successfully exploited the car's internet browser, a feat that earned them $35,000 and the car itself. The successful attempt allowed the team to walk away from the competition with $375,000, more than seven times as much as any other group in competition this week.
They did it. A successful demonstration by the @fluoroacetate duo on the Model 3 internet browser. Now off to the disclosure room for details and confirmation. pic.twitter.com/GrbZYUvYQa
— Zero Day Initiative (@thezdi) March 22, 2019
It took some time to confirm but according to the Zero Day Initiative, technically the duo exploited a JIT bug in the vehicle's in-browser renderer to win the car.
Confirmed! The @fluoroacitate duo used a JIT bug in the renderer to win $35,000 and a Model 3. What a great way to kick off the automotive category of #Pwn2Own.
— Zero Day Initiative (@thezdi) March 22, 2019
The hack put some wind back into the competition’s sails following news shortly after noon on Friday – early morning Vancouver time – that another group that was planning an automotive exploit, KunnaPwn, was going to withdraw their entry from the category. It was unclear at the end of the day Friday why KunnaPwn withdrew their entry; the group tweeted "We're running out of time. Looks like Kunna!Pwn this time" Friday morning.
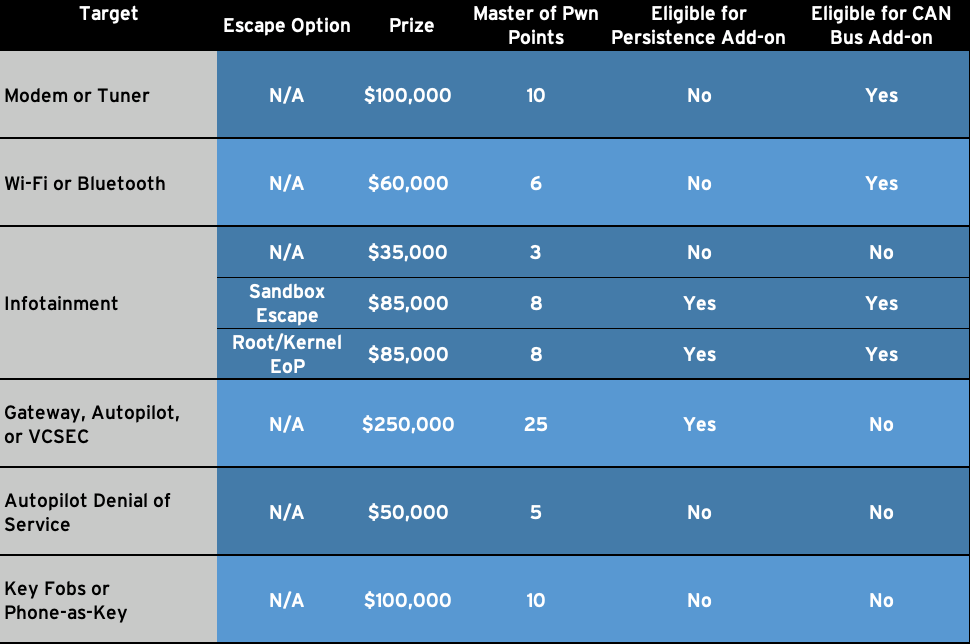
The Zero Day Initiative (ZDI), which sponsors Pwn2Pwn with Trend Micro, announced in January that it was planning on expanding the competition's categories to include an automotive category. As part of the competition the ZDI said it would award different sums for different exploits, against the vehicle's key fobs, infotainment system, modem or tuner, and so on.
Earlier in the week, on Thursday, there were no failures; everyone who attempted an exploit succeeded, a rarity for the contest.
Mozilla's Firefox browser and Microsoft's Edge browser were hit early and often on the contest's second day.
Two hackers, Amat Cama and Richard Zhu, working under the pseudonym Fluoroacetate were able to bring down both - Firefox with a JIT bug and an out-of-bounds write in the Windows kernel, and Edge with a type confusion, a race condition in the kernel, and an out-of-bounds write in VMware. While both were impressive it was the Edge/VMware exploit that netted them the most cash: $130K.
Two other contestants, working solo, also managed to takedown the browsers. Niklas Baumstark, a German hacker, was able to chain together a JIT bug in Firefox and a logic bug to escape the browser's sandbox. Another hacker, Arthur Gerkis of Exodus Intelligence, a Texas-based threat intel firm, took down Edge with a double free in the render and a logic bug to bypass the sandbox.
Earlier in the week, on Wednesday, hackers managed to take down Apple's Safari browser, Oracle VirtualBox, and VMware Workstation
The Fluoroacetate team was responsible for breaking all three. They exploited the browser and managed to escape the sandbox by combining an integer overflow and a heap overflow, netting them $55,000. With their VirtualBox hack the two used both an integer underflow and a race condition, something which allowed them to escalate from the virtual client. The duo also used a race condition, which lead to an out-of-bounds write, on VMware Workstation. That exploit allowed them to go from the virtual client to executing code on the underlying host operating system.
Another group of hackers, working under the name Phoenhex & Qwerty, also took down Safari on Wednesday through kernel elevation, something that resulted in a complete system compromise through a cocktail of bugs including a JIT bug, a heap out-of-bounds read, and a time-of-check-time-of-use bug.
One of the group's hackers, Niklas Baumstark, clearly has a knack for owning Macs. Last year, working aside German hacker Samuel Groß, Baumstark used a JIT optimization bug in Safari, paired with a macOS logic bug, to escape Safari's sandbox.
Phạm Hồng Phi, a/k/a @4nhdaden, working under STAR Labs, a Singapore-based cybersecurity group, also took down VirtualBox on Wednesday. Phi managed to exploit VirtualBox, Oracle's open source virtualization product, via an integer underflow to escalate from the virtual client to execute his code at medium integrity.
