As we defined “intellectual property” in my last post, we now need to classify each of the “crown jewels” of your organization. Consider using an automated data protection platform like Digital Guardian to classify each asset based on distinct levels of sensitivity, and then define specific rules for each level.
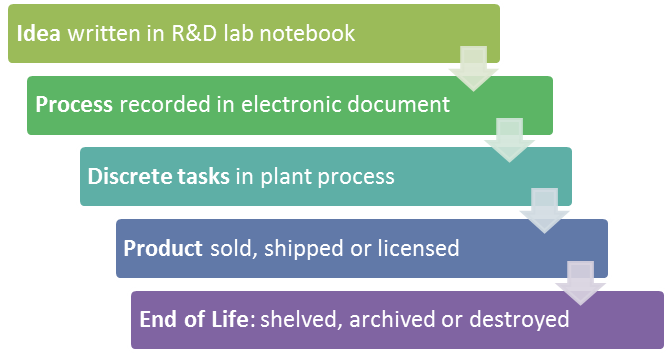
Your crown jewels need to be protected throughout their IP life cycle, which covers their entire journey from concept to process to shipping product. Consider this complete cycle when looking for weaknesses in your IP defenses.
Lock up your crown jewels in secure electronic “vaults” where strong multi-factor authentication and robust account management restrict access by user role. Control access using the principle of least privilege – granting people the lowest level of user rights necessary to do their jobs effectively. Investigate technologies such as digital rights management (DRM) and data loss protection (DLP) which provide data encryption and export restriction capabilities.
As content is removed from the vault, it is controlled and protected by the policies associated with how it was tagged during classification. Monitor and audit IP usage by partners and suppliers throughout your supply chain. Set up alerting whenever an established control such as user privileges or firewall configuration is changed. Secure endpoints such as PCs and mobile devices when off the network, where many data breaches originate. All of these actions will make it very hard for attackers to gain privileged access to any of your crown jewels.
To summarize, follow this checklist to protect your IP from both insider threats and cyber attacks:
□ Consider an automated tool to identify & classify your IP.
□ Create policy rules & privileges for each type of asset.
□ Establish very tight electronic access controls.
□ Tag & monitor IP throughout its lifecycle.
□ Investigate technologies such as DRM & DLP.
Now download my e-book covering 5 key IP protection tips to follow, based on the practical experience of Digital Guardian’s manufacturing industry customers.
Read the full series:
- The Threats to Your Trade Secrets are Real
- Why Offshoring Complicates IP Protection
- Calculating the True Cost of IP Theft
- Make the Case for Investment in Ongoing IP Protection
- How to Form an IP Risk Committee
- 7 Elements of a Holistic IP Protection Plan
- Defining Intellectual Property
- Lock up your IP and Control Access to it
- Discover the Weaknesses in Your IP Security
- Improve Your Ability to Detect Cyber-Attacks
