It’s all about the money.
Not surprisingly, when it comes to incentive, the majority of bad actors – or at least the ones behind most data breaches last year - were looking to get paid.
According to Verizon’s 2020 Data Breach Investigations Report, 86 percent of data breaches were fueled by financial gain. For reference, breaches where the end goal was financial gain accounted for 71 percent in 2019.
The publication, known in infosec circles as the DBIR, is a compendium of the year in data breaches. The report, released annually by Verizon Enterprise Solutions, is a deep dive analysis around information security incidents, namely data breaches, and a cornerstone of sorts for the industry over the past 12 years.
This year’s report looked at 3,950 breaches in total across 16 different industries, and four world regions. Last year's report, in comparion, looked at 41,686 security incidents, 2,013 which were quantifiable data breaches.
As usual, the mammoth report (119 pages) has a lot of points to make.
The number of financially-motivated attacks far outweighed attacks where the end result was espionage and was more than double the number of incidents involving what Verizon calls secondary attacks, attacks in which the motive of the incident is to aid in a different attack. Under that definition, something like a breach that comes as a result of a supply chain attack could count as a secondary attack, or for instance, if an attacker were to compromise something like a web server and repurpose it for his own misdeeds, like hosting malicious files or using it to distribute spam.
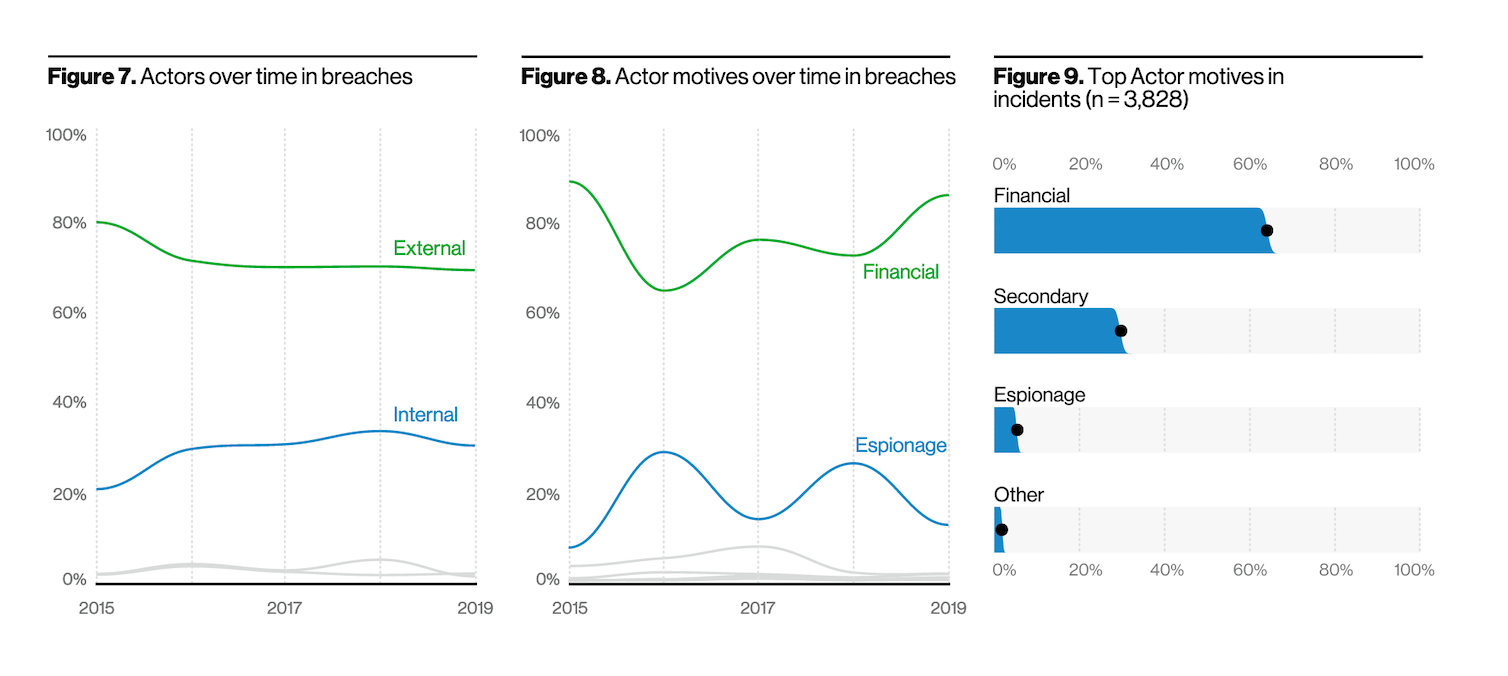
Actors over time in breaches continue to remain the same; roughly 70 percent of actors are external, around 30 percent around internal. They continue to leverage the usual methods too, hacking most of all, followed by social, error, and malware. Most of the numbers around these actions are the same as last year; malware has decreased a little - likely because attackers are getting the job done with hacking and social breaches, Verizon posits.
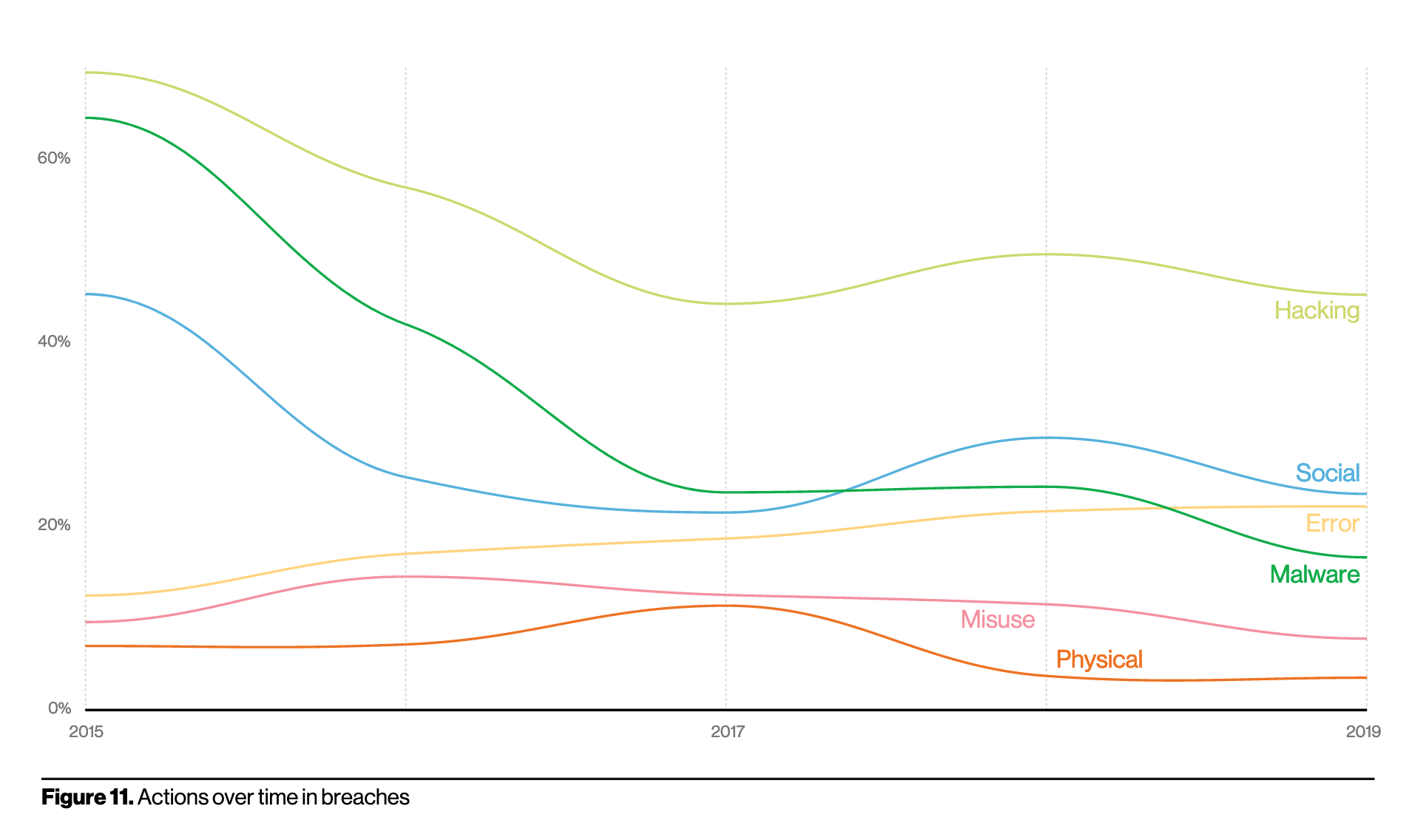
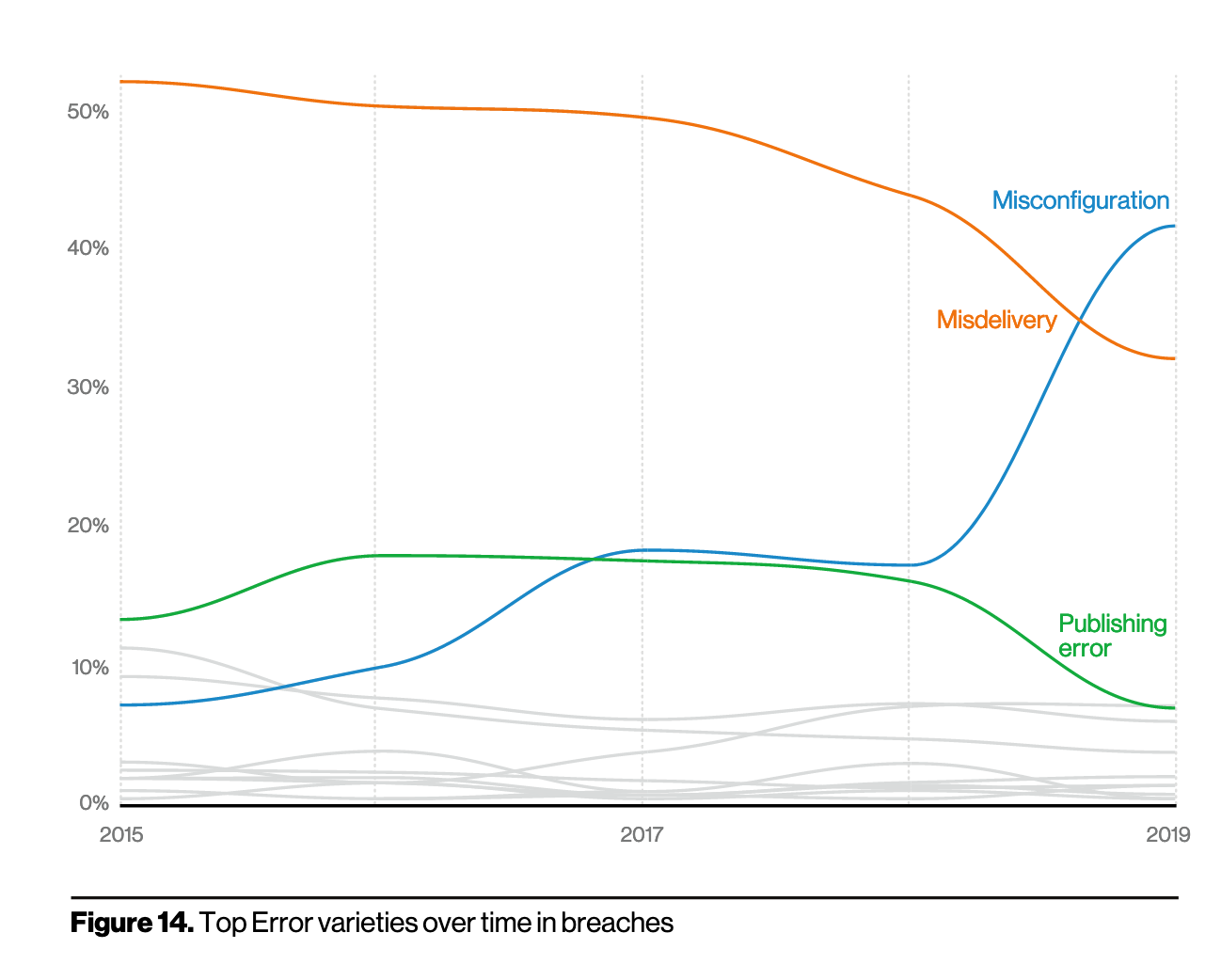
Error is the only action that saw a incremental uptick this year. According to the report, error is as common as social breaches and more common than malware, suggesting misconfiguration errors, which often lead to exposed data in the cloud storage repositories and S3 buckets, aren’t going away any time soon. The rash of poorly secured, internet-exposed storage discoveries by researchers over the last several years almost certainly factors into misconfiguration's rise in the following chart.
One of the biggest stories the DBIR has to tell is around web applications. One of the biggest jumps, a 43 percent increase, comes from attacks on web apps, a figure that the DBIR says is double last year’s and especially a problem for small organizations and those in the EMEA and APAC region.
Most of the breaches (80%) the report combed through involved hacking via either brute force or via stolen or lost credentials – cloud-based email usually – while paired with the exploitation of a web app vulnerability.
Across the board, industry by industry, web app vulnerabilities were a problem. In professional, scientific, and technical services – lawyers, research labs, and consultants, they accounted for 35% of breaches. Public administration, around 38%. Same for real estate. In the financial industry, web application vulnerabilities accounted for nearly as many breaches as miscellaneous errors, a stat Verizon has some fun with: “It is a bit disturbing when you realize that your employees’ mistakes account for roughly the same number of breaches as external parties who are actively attacking you. Apparently, it really is hard to get good help these days, and you can take that to the bank,” the report reads.
“We have spent some time on this over the last year, and it is important to reassert that this trend of having web applications as the vector of these attacks is not going away,” the report adds.
Like last year's report, this year's emphasizes some of the issues caused by denial of service attacks and phishing.
Phishing factors into social attacks in the DBIR and when paired with attacks like business email compromises, collectively caused over 67 percent of breaches. Phishing in particular accounted for 25 percent of all breaches and over 30 percent of breaches at small businesses. Denial of service attacks have dealt a blow in Europe, the Middle East, and Africa, and Latin America. They were linked to over 80 percent of malware incidents there last year, according to the report. Researchers counted over 13,000 denial of service incidents last year and while obviously they don't lead to a breach of data in and of themselves, they do have an effect on infrastructure, especially in Latin American and the Caribbean region, where they accounted for between 50 and 70 percent of incidents.
It’s not all doom and gloom; there were some silver linings, including statistics around breach remediation.
Breaches are getting discovered and contained faster. When looking at the timeline section of Verizon's report, 60 percent of breaches are discovered in days or less, a number the researchers are attributing to breaches detected by managed security service providers. An increase and improvement in detection and response is likely responsible for an uptick in the time it takes to contain breaches over time: 81% are taken care of in days or less.
Cyber-espionage, attacks Verizon attributes to unauthorized network or system access, like when nation states or state-affiliated actors hack into a system, are down, too. Cyber-espionage accounted for 13.5% of breaches in 2018 but only accounted for 3.2% breaches in 2019.
It will fascinating to see how the numbers in next year's report look in the wake of this year's COVID-19 pandemic. Verizon only looked at cases until October 31, 2019 for this report, meaning the full scope of breach patterns relating to COVID-19 weren't yet clear.
