Data Loss Prevention (DLP) is everywhere. On endpoints, on email services or servers, on email and web gateways, on Microsoft Teams, on cloud services and more.
In this article, we'll cut through the complexities and look at what network data loss prevention (nDLP) can do over endpoint data loss prevention (eDLP) and vice versa.
First, a quick primer: What is an endpoint? What is a network? An endpoint is what the end user interacts with. Typically, a desktop or laptop, however tablets and smartphones are included also. The network is the realm between users’ devices, servers, buildings, data centers and really, the internet. nDLP can monitor, track, and analyze activity across a network, uncovering sensitive data in protocols, local and remote repositories while eDLP extends that monitoring to include laptops, servers, and so on.
Looking at the combined features of both eDLP and nDLP
Before looking at what eDLP and nDLP can and can't do, let's define the following actions.
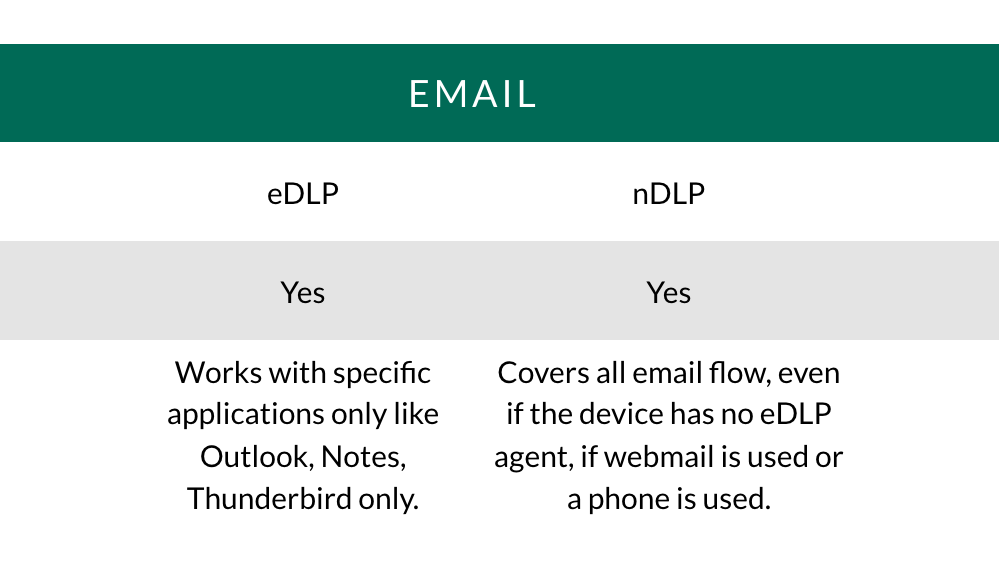
Email: Monitoring and/or blocking of incoming and/or outgoing emails.
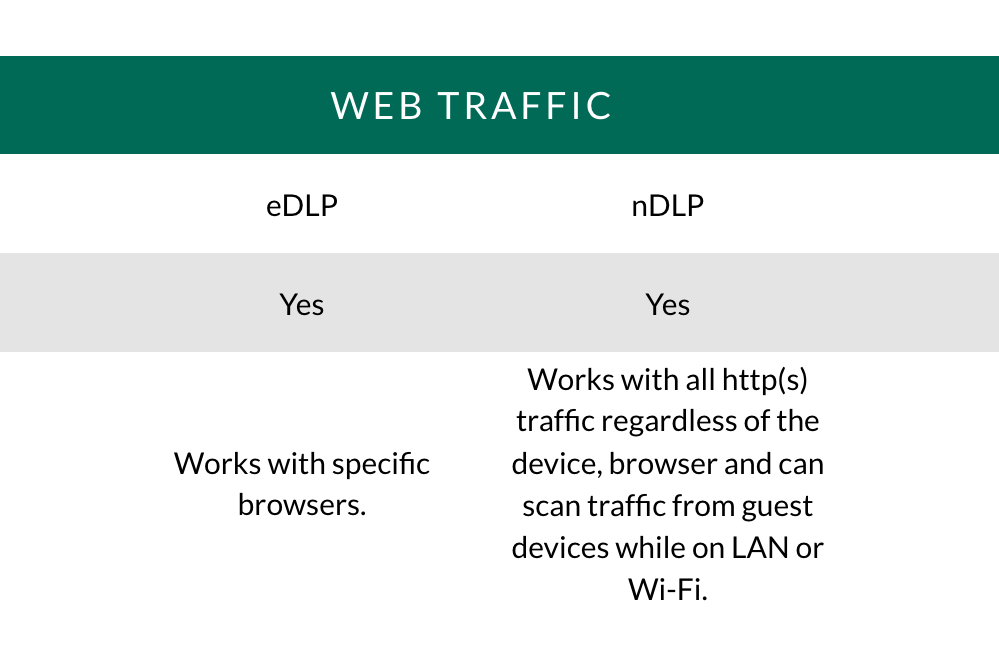
Web Traffic: Monitoring and/or blocking of traffic leaving the network.
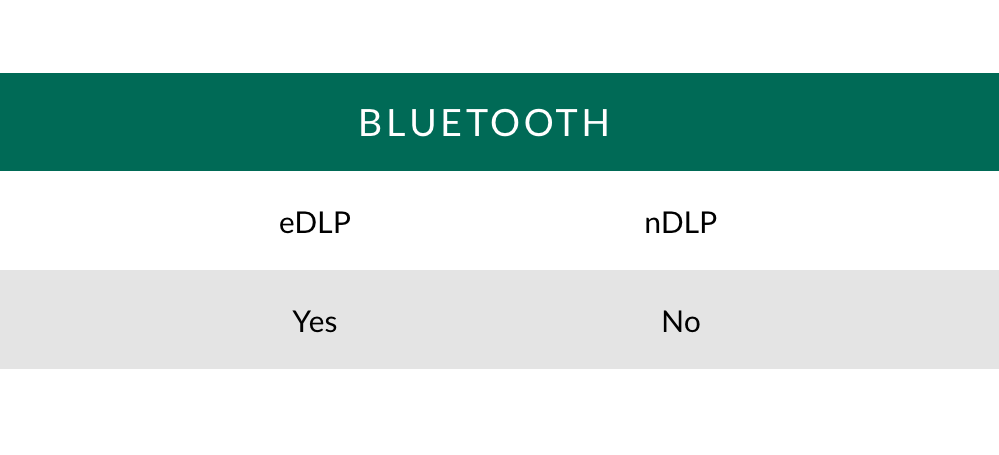
Bluetooth: Monitoring and/or blocking transfers to laptops, phones or tablets.
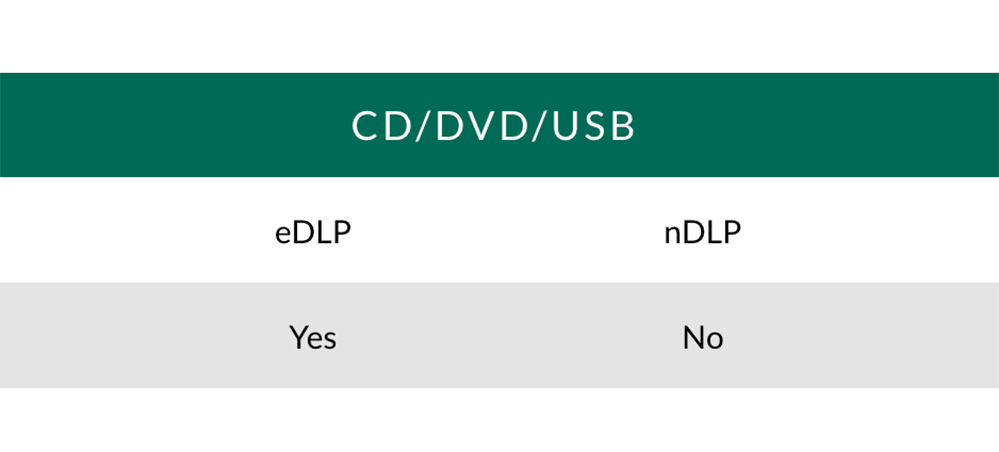
CD/DVD/USB: Monitoring and/or blocking of devices or stopping data going to them.
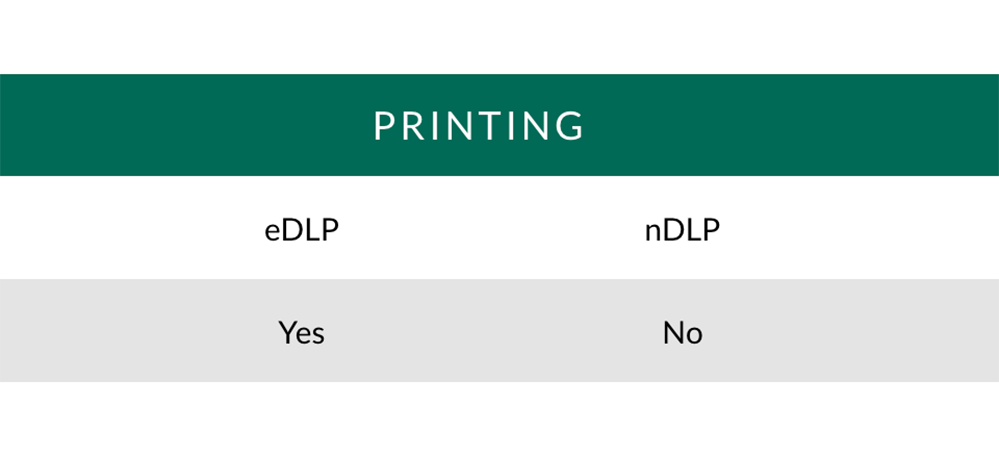
Printing: Monitoring/blocking of physical printing or to PDF.
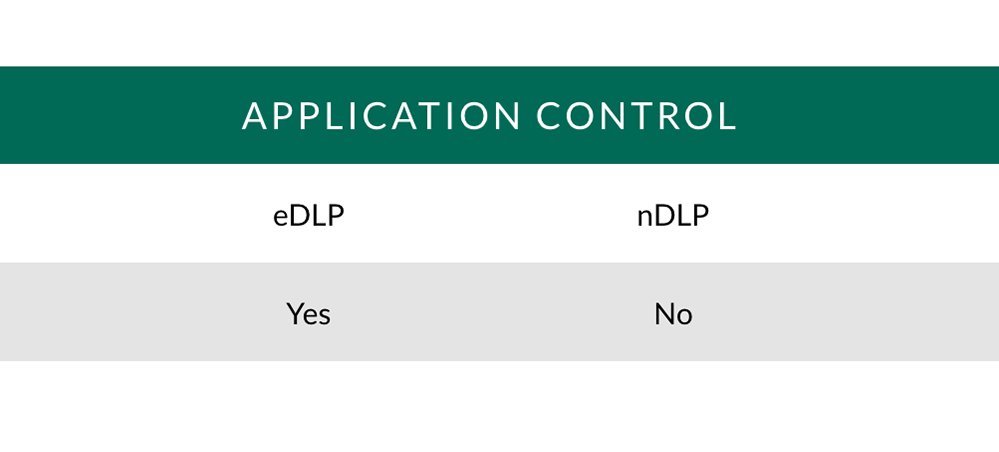
Application Control: Blocking launches of specified applications.
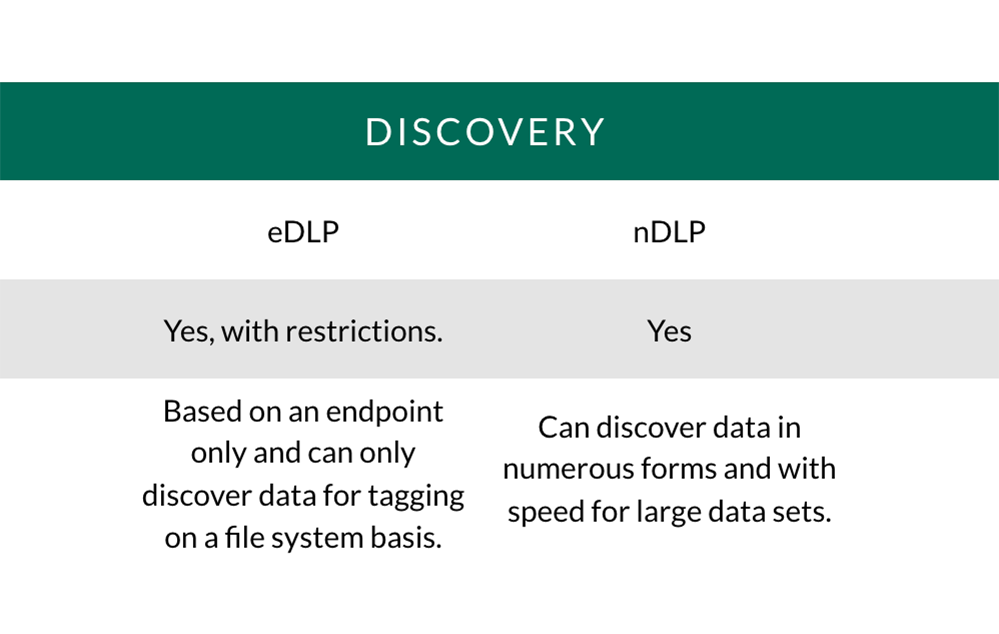
Discovery: Scanning of network shares, cloud repositories & databases for sensitive information.
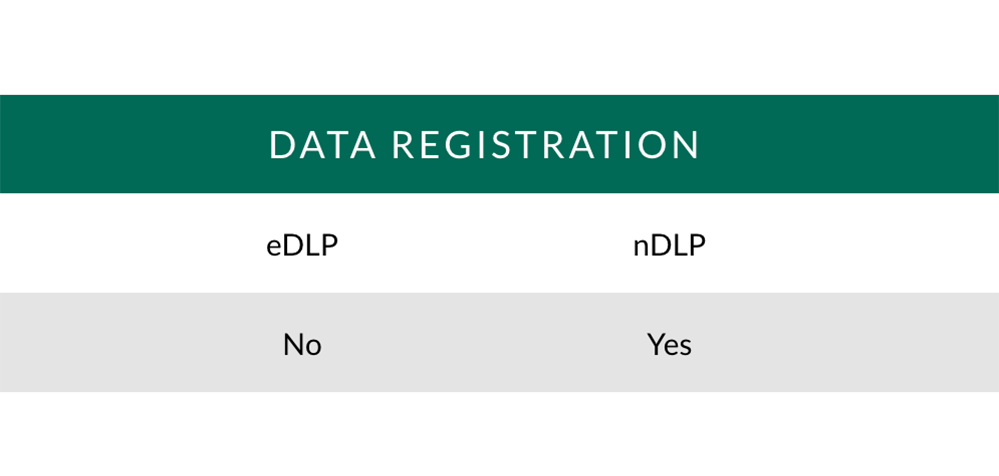
Data Registration: Register data you deem sensitive, then look for it later. Instead of writing pattern-based policies; register the data and detect if egress data matches pre-registered data.
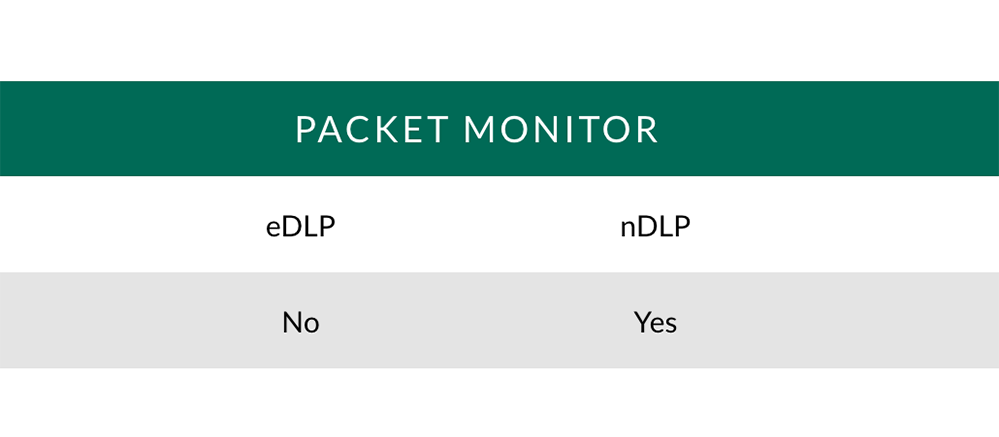
Packet Monitor: Take a feed from a switch, monitor traffic and record triggers.
How do they compare?
Other considerations
Cost
Depending on the features taken, in some scenarios, nDLP can work out being cheaper in licensing and labor costs.
Setup time
nDLP is rolled out centrally and does not need an agent for all devices in the organization, something that can reduce implementation time.
AV exclusions
eDLP requires antivirus exclusions to be done both ways and nDLP does not.
Faster policy deployment
NDLP policies are active in seconds whereas agent new policies updates need to be received by end devices.
In an ideal world, using both eDLP and nDLP would be a perfect way to help increase your organization's visibility and defense-in-depth methodology. Naturally, like most things, everything comes down to your risk appetite, what you want to protect and of course, your budget.
Want to see Digital Guardian in action?
Learn how we can help your organization meet compliance, protect valuable IP and help reduce data loss.

