Many times, when a malicious insider opts to steal data it's to use the ill begotten funds for financial gain but other times it's simply because it's fun.
There are a handful of reasons but over the last year the top motivations for malicious insiders has been financial at 47.8 percent, fun at 23.4 percent, and espionage at 14.4 percent. Simply having the convenience to steal the data, the employees harboring a grudge, it being baked into the employees’ ideology, and fear are the remaining motivations.
The figures come from Verizon's Insider Threat Report, a report released this week that reframes data from the company's 2018 Data Breach Investigations Report (DBIR) and incorporates new statistics. Verizon doesn’t debate the fact that insiders are driven by money but it does highlight the concept of an insider hacking an organization’s data simply because they can or a healthcare worker snooping on medical records simply because they have access in the first place.
The report, which clocks in at a hefty 71 pages, breaks down insider threat scenarios, case studies, the types of sensitive data that’s breached industry by industry, and varieties and vectors of data misuse, and indicators of insider threat activity.
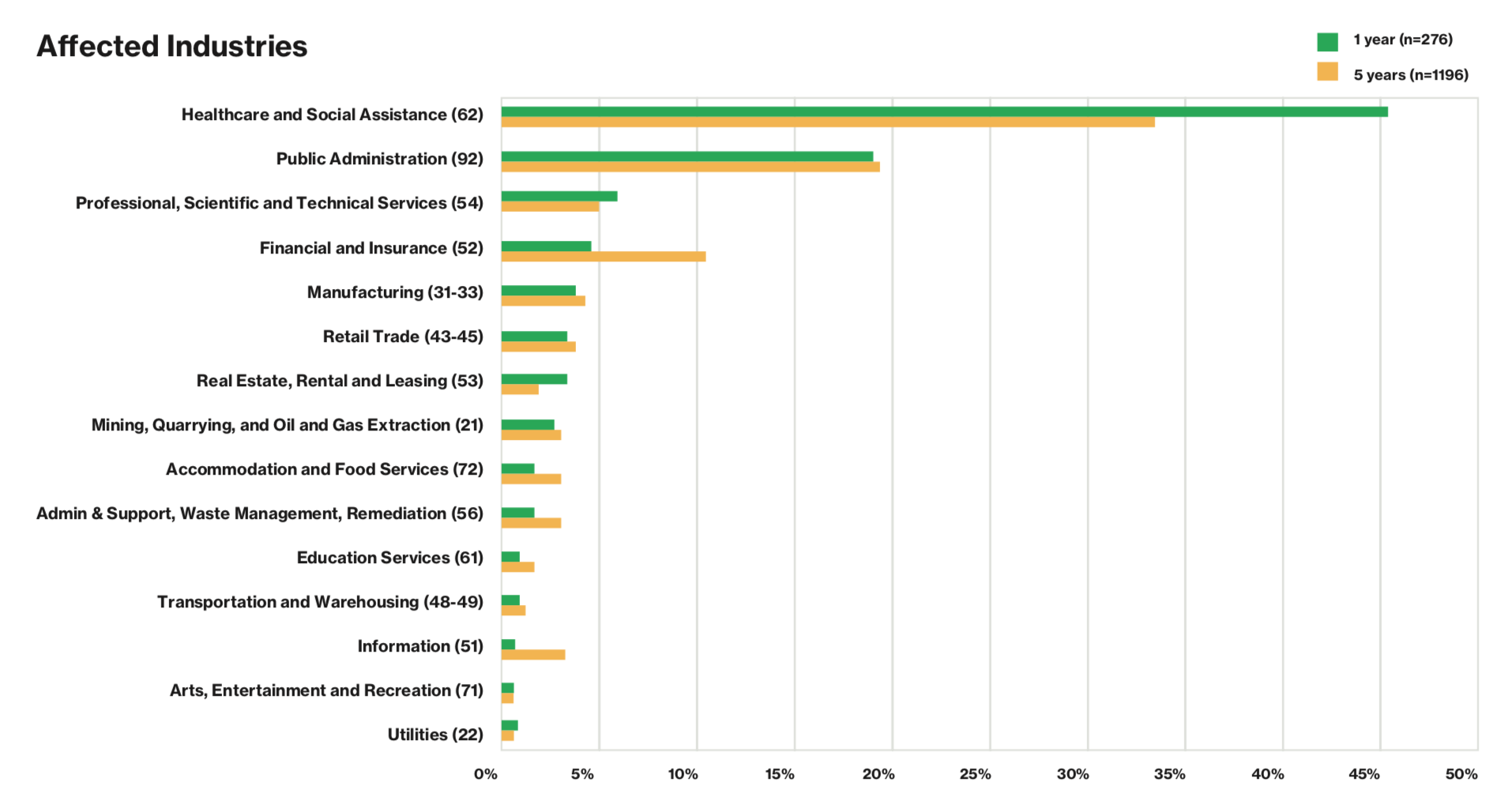
It also looks at the top industries affected by insider and privileged misuse – Healthcare and Social Assistance businesses were the most affected at 46.4 percent, public administration services were second at 18.5 percent.
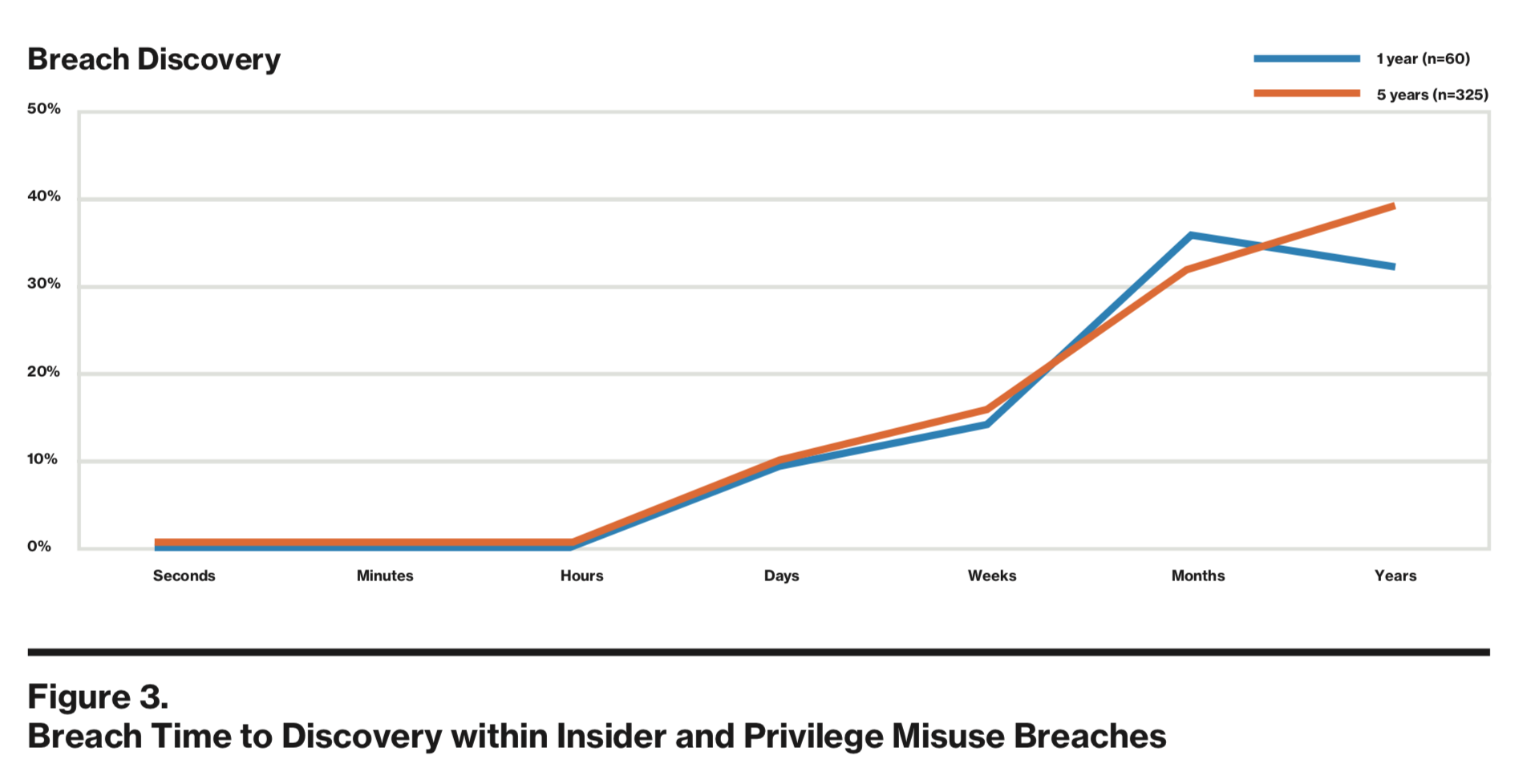
It also looks at the timeline around data breaches, like the amount of time it takes for discovery, over the past year, and over the past five years. While it can only take a few minutes ordinarily for an attacker to compromise a system, it can take months to actually discover the misuse:
The report throughout largely aggregates incident statistics classified using the Vocabulary for Event Recording and Incident Sharing (VERIS) Framework, a taxonomy that standardize a common language for describing the security incidents.
The report also breaks down what Verizon categorizes as the five different insider threat actors, including:
- The Careless Worker, essentially any employee or partner who steals data, mishandles data, installs unauthorized apps, these insiders traditionally operate counter to those who act maliciously.
- The Inside Agent, employees who steal data on behalf of outsiders, insiders who are recruited, solicited or bribed by external parties to exfiltrate data.
- The Disgruntled Employee, an employee which is usually out to destroy property, or harm their organization by destroying data or disrupting business activity.
- The Malicious Insider, the employee who is out to steal data for personal gain.
- The Feckless Third Party, Business partners who compromise security through negligence, misuse, or malicious access.
Perhaps more importantly the report outlines 11 countermeasures organizations can take to help reduce risk and assist in incident response, from preparation to mitigation, including:
1. Integrate Security Strategies and Policies
2. Conduct Threat Hunting Activities
3. Perform Vulnerability Scanning and Penetration Testing
4. Implement Personnel Security Measures
5. Employ Physical Security Measures
6. Implement Network Security Solutions
7. Employ Endpoint Security Solutions
8. Apply Data Security Measures
9. Employ Identity and Access Management Measures
10. Establish Incident Management Capabilities
11. Retain Digital Forensics Services
Being able to classify data for proper access and protection measures is critical for balancing the data management life cycle according to Verizon, too.
“Accurate classification is the basis for a successful data protection program,” the report reads, “classification must be meaningful – if data is classified as sensitive, that should come with a clear definition and classification policies.”
“Instead of only blocking potential intrusions, protecting data (such as by encryption) is an important approach, and also helps employees carry out daily tasks more seamlessly. Data protection should be based on a data classification policy and be uniform throughout the organization,” the report adds.
Looking to learn more about Fortra's Digital Guardian?
Have a question about data loss prevention, secure collaboration, or SaaS data protection? Don't hesitate to get in touch. We're here to help.

