Compliance with Payment Card Industry Data Security Standard (PCI DSS) was down this year for the first time in six years; only 52.5 percent of organizations that demonstrated full compliance at an interim assessment. One of the best ways for organizations to achieve PCI Security compliance for effective data protection is to design and maintain sustainable control environments that support the 12 key requirements of the PCI DSS standard.
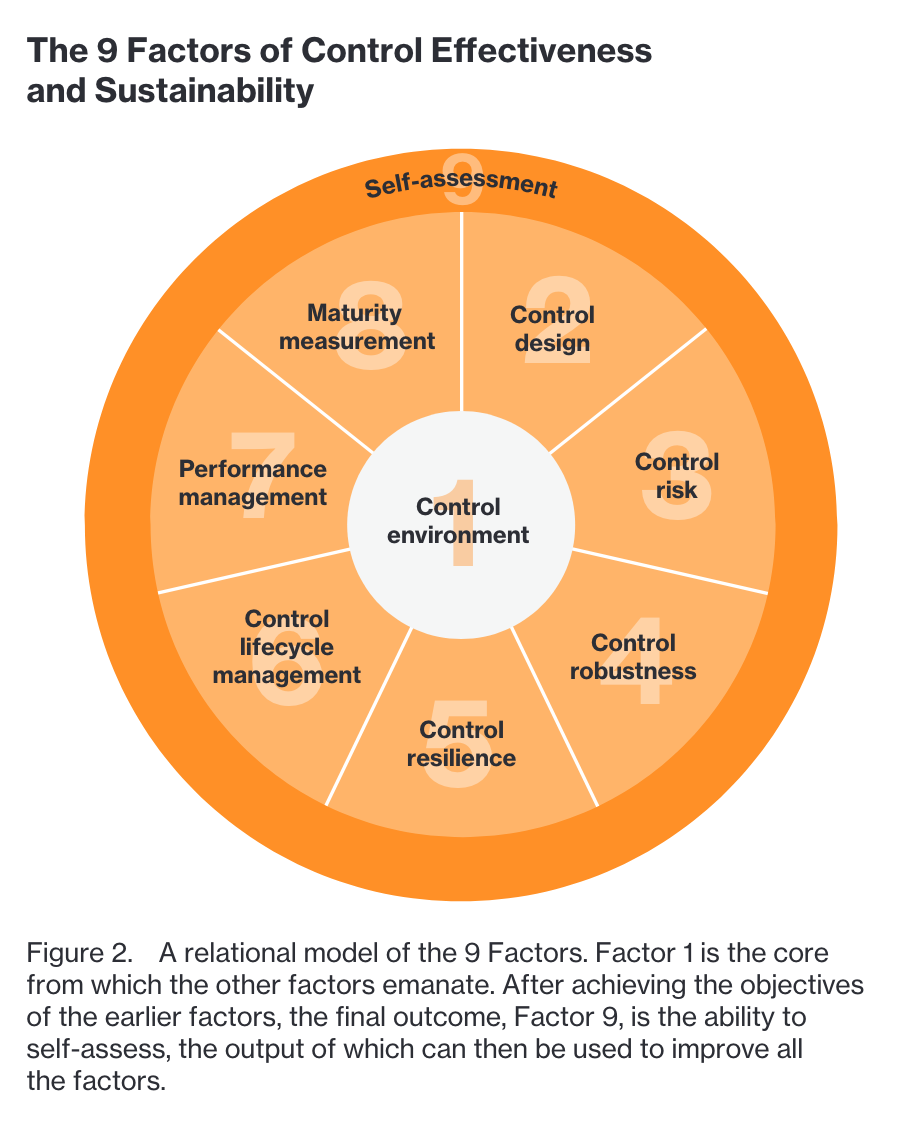
Experts from Verizon's security assurance team - a group that includes members of the company's cyber risk program, threat and vulnerability team, PCI, and governance, risk, and compliance teams - say organizations can structure their data protection and compliance programs around nine different controls.
According to the company’s 2018 Payment Security Report, released earlier this fall, the controls can help organizations detect weak spots in their security system and evolve in the face of mounting challenges.
1. Control Environment
In the eyes of Verizon, a control environment includes the standards, processes, and organizational framework that internal controls are implemented and operated. "In payment card data protection, a control environment with a defined internal control framework contributes to risk mitigation and provides guidance on controls to address card security risks."
Failure to properly manage a control environment can exacerbate PCI DSS control failures. Organizations should formally outline the structure of their compliance program, with defined objectives, defined scope, and support projects. Once it's been defined, an organization can perform a risk assessment to determine its impact on the payment security control environment.
There are two approaches to PCI compliance program management - top-down vs. bottom-up; both need oversight in order to ensure the long-term sustainability (and improvement) of internal controls.
2. Control Design
Proper control design - "the process of systematically planning and specifying the purpose, function, scope, limitations and dependencies of a security control" - is essential when it comes to managing control effectiveness and sustainability. Control design needs to be informed by the needs of the process and the needs of an organization.
They should not be fluid; they should be tailor-made and designed with customization and skill in mind.
Without a systematic method for control design, an organization can't ensure control effectiveness.
3. Control Risk
According to Verizon, control risk is the "likelihood and impact of control failure due to the tendency of controls to lose their effectiveness overtime."
According to the report the factor can be swayed by:
- Known history of control deficiencies or errors
- The nature and probability of the risks that the control is intended to prevent, the frequency with which it operates, and the inherent risks associated with the control and related control system
- Changes that might adversely affect the design or operating effectiveness of the control
- The degree to which the control relies on the effectiveness of other controls (e.g., the control environment or general information technology controls)
- Competence of the personnel who perform the control or monitor its performance and current information on changes in key personnel
- Whether the control relies on performance that is manual or automated
Organizations can evaluate risk by identifying it in the first place, assessing it, prioritizing it, planning risk mitigations, and by managing it. These actions, which ultimately fall to the management, not auditors or assessors, should be thorough.
“All security control systems should be included in a control risk evaluation. At minimum, all critical control systems (collections of DSS and supporting controls) should have a documented control design and associated control risk report.”
4. Control Robustness
Control robustness pertains to "the ability of a control or control system to remain effective in meeting its control objective, despite environmental disruption."
Control environments that can withstand pressure - "IT component changes, changing business requirements, limited resources, external regulatory change, and external threats" - but still operate are considered robust.
In Verizon's eyes using the "Four Lines of Assurance" model is a good fit for payment security environments. In that model individuals like staff, management, and directors, are responsible for managing operational risks, the second line, risk and compliance teams, provide support, internal audits help provide reasonable assurance "of the overall effectiveness of governance, risk management and controls," and external auditors, regulators, and external bodies provide assurance from outside the org's structure.
5. Control Resilience
Security controls aren't a silver bullet; they can still fail - but the idea of control resilience ensures an organization can quickly recover from disruptions and resume operations. "Control resilience brings together the areas of data protection, business continuity, and organizational resilience into an individual control-level concept," the report reads.
The report cites cyber resiliency goals, originally published by MITRE, that say an org should maintain a state of informed preparedness, continue essential functions in the face of attacks, restore functions to the fullest extent possible following an attack, and change functions, following an attack, to minimize adverse future attacks.
6. Control Lifecycle Management
It's important to monitor and manage controls throughout the entirety of the lifecycle, from the conception to the retirement of a control. The idea of security control lifecycle management (SCLM) isn't new but it is somewhat for payment security, only being introduced by Verizon in 2017.
Traditionally the steps of a SCLM are as follows:
- Conception
- Design and build
- Testing
- Introduction and deployment
- Operation and monitoring
- Growth and evolution
- Maintenance and improvement
- Maturity
- Decline and retirement
7. Performance Management
The concept of performance management involves utilizing performance standards to measure how the control environment improves control effectiveness, data protection, and compliance. “The performance management activity includes the clarification of goals and objectives setting standards, measuring actual performance and taking corrective action,” Verizon said in its report.
According to the report, only half of the orgs it talked to manage their PCI DSS compliance program as a standalone project and not as part of a broader data protection program initiative.
“Teams and individuals must know and understand data protection and compliance expectations and have the skills and ability to deliver on these expectations.”
8. Maturity Measurement
Organizations need a way to track the formality and optimization of processes to see how close they're being to be completed. “It’s the ability to continuously improve data protection and PCI compliance performance—an organizational capability that is essential to achieve and maintain an effective and sustainable control environment,” the report says.
This often tends to be the biggest hurdle for organizations, many which fail to let their programs mature. According to the company's survey only 40 percent of orgs use process maturity models to measure aspects of their PCI Security compliance program as a means to gauge how close processes are being to done.
"Being able to articulate not only performance-based metrics, but also the maturity of controls within the control environment and the maturity of the control environment as a whole, contributes substantially toward helping all parties within the organization participate in a meaningful dialog about the state of data protection, its actual effectiveness, sustainability and improvement."
9. Self Assessment
Lastly, the ability to look over the end result, to establish, evaluate, and record outcomes for all of the factors, is an appropriate closing step here. Companies need to look over its:
- Resource capacity (people, processes and technology),
- Capability (supporting processes),
- Competency (skills, knowledge and experience)
- And commitment (the will to consistently adhere to compliance requirements)
Verizon says companies should demonstrate continuous improvement when it comes to evaluating a control environment's control sustainability and control effectiveness. That allows orgs to advance in maturity, improve communication and perspective about the overall state of data protection, compliance, and helps boost confidence in internal team proficiency.
PCI compliance is an ongoing process but necessary to prevent breaches and secure payment card data theft.
Learn how Digital Guardian helps meet compliance initiatives by classifying, encrypting, and protecting sensitive PCI DSS data across endpoints, networks, and cloud environments.

