A complex and malicious platform, believed to be the work of a skilled APT group, has lingered in the wild since 2012 but avoided detection until just recently.
Researchers with Kaspersky Lab’s Global Research and Analysis Team (GReAT) disclosed the APT at its annual Security Analyst Summit (SAS) conference on Friday in Cancun, Mexico.
The main goal of the platform, which researchers have dubbed Slingshot, appears to be cyberespionage. In affected machines Slingshot replaces a legitimate library, scesrv.dll, with a malicious library that's able to go on and interact with a virtual file system, along with other modules.
While researchers with the firm were hazy on the malware's initial infection vector, they were able to confirm that most victims were hit either via a Windows exploit or a compromised Mikrotik router. MikroTik, a Latvian company, makes routers, switches and other wireless systems.
By exploiting an unknown vulnerability in the routers, it appears attackers have been able to infect the router's admin via a router-specific configuration utility called Winbox.
For what it’s worth, on later versions of its routers Mikrotik said that WinBox can no longer download IPV4 packages from the router, something Slingshot was leveraging to infect machines.
Researchers with the firm say they believe activity around Slingshot began back in 2012. Activity around the platform was still active as the researchers began to compile their analysis, in February this year.
According to a lengthy 25-page writeup (.PDF) on Slingshot, Kaspersky Lab researchers stumbled across the platform while looking into an incident that involved what it believed was a keylogger. After diving deeper the researchers discovered the aforementioned malicious library and that it contained strings that looked to be related to Virtual File System handling.
Being able to interact with a virtual file system usually fits the behavior of an advanced persistent threat or APT, researchers behind the report - Alexey Shulmin, Sergey Yunakovsky, Vasily Berdnikov, Andrey Dolgushev - said Friday.
Once in Slingshot reportedly collects screenshots, keyboard data, network data, passwords, USB connections, and any information left on the desktop clipboard. It also uses vulnerabilities likeCVE-2007-5633; CVE-2010-1592, and CVE-2009-0824, to gain full access to the kernel level of systems.
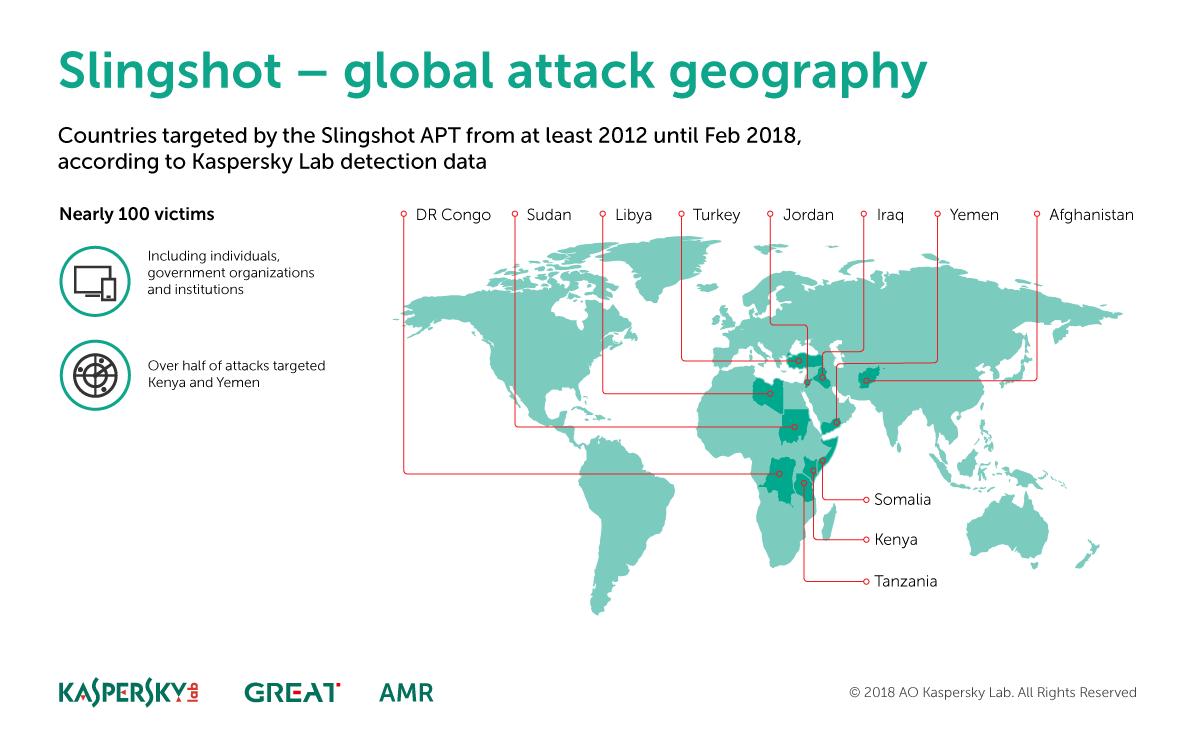
While the bulk of the attacks have been on individuals in Kenya and Yemen, researchers have seen Slingshot attacks hit 100 victims in the following countries: Libya, Afghanistan, Iraq, Tanzania, Jordan, Mauritius, Somalia, Democratic Republic of the Congo, Turkey, Sudan and United Arab Emirate.
While Slingshot has gone unnoticed all these years is fascinating what's particularly interesting is the fact researchers compared the platform’s complexity to ProjectSauron and Regin.
ProjectSauron, an APT platform disclosed in 2016 (.PDF) targeted critical government, financial and communications organizations in Russia, Iran, Rwanda, China, Sweden, Belgium and Italy dating back to 2011. Also notable: A module that moves data from air-gapped machines via a removable USB also figured into the platform.
Regin, another APT platform - announced in 2014 (.PDF) - could spy and exfiltrate email and documents from government agencies, research institutions and banks. Kaspersky Lab said they had seen attacks on 14 different countries at the time of the platform’s announcement. What made Regin particularly dangerous was the platform’s ability to target GSM base station operators to launch additional attacks.
“The malware is highly advanced, solving all sort of problems from a technical perspective and often in a very elegant way, combining older and newer components in a thoroughly thought-through, long-term operation, something to expect from a top-notch well-resourced actor,” the researchers wrote, “All this framework is designed for flexibility, reliability and to avoid detection, which explains why these components were not found for more than six years.
While Slingshot's campaign is focused on Africa and the Middle East, it's unclear exactly who or what group may be behind it.
One of the few things the researchers could deduce about the threat actors was that the authors behind Slingshot are likely fans of J.R.R. Tolkien: There are several references to Lord of the Rings (Gollum, Smeagol) throughout the platform's debug messages.
