If your company allows employees to bring their own computing devices to the workplace – whether they are smartphones, tablets, or laptops – you need a BYOD security policy. Initially, employees used only company-issued devices in the workplace. Today, smartphones and tablets have proliferated in the consumer market to the point that nearly every employee comes to work with their own internet-connected device. This means higher potential for an employee introducing security risks to your company.
Devices at Work vs. Devices for Work
It’s one thing for an employee to bring a personal device to work and use it strictly for personal communications. This practice can still create risks, but the most substantial security risks are associated with employees using personal devices to conduct business, whether simply sending work-related emails or actually accessing secure company applications from their own smartphones or tablets.
The difference is essentially that in one case, employees are using their personal devices at work; in the other, employees are using their personal devices to conduct work. Devices that are brought to the workplace but do not have access to the company network are not usually problematic; however, due diligence is necessary in all cases with strict, clearly defined BYOD policies and enforcement.
The Challenges of BYOD Security
BYOD security is often a challenge for enterprises and SMBs alike. This stems from the fact that in order to be effective, companies must exert some form of control over smartphones, tablets, and laptops that are not owned by the company but are employees’ personal assets. As BYOD has become increasingly common and awareness of security risks has grown, BYOD security policies are becoming more widely adopted and accepted by both companies and their employees.

Image via Trend Micro
BYOD is more prevalent in the workforce than just a few years ago. In fact, a November 2014 survey from Tech Pro Research found that 74 percent of organizations either already allowed employees to bring their own devices to work or were planning to do so. As of 2016, 87% of companies were relying on employees to use their personal smartphones to access mobile business applications, and 45% of U.S. employees were required by their employers to use their personal smartphones for business purposes.
Companies adopting BYOD benefit from reduced hardware and software costs, but at the same time, BYOD places additional responsibilities on IT departments, which must maintain the devices as well as ensure that the practice does not introduce unnecessary vulnerabilities to the company network and data. Interestingly, among the 26 percent of Tech Pro Research’s survey respondents not adopting or planning to adopt BYOD, security concerns were the most common reason cited for ruling out the practice.
The Need for BYOD Security

Image via Druva
According to one recent study, the BYOD market will reach more than $350 billion by 2022 (up from $94 billion in 2014), and significant growth is expected in the global BYOD market between 2020 and 2026. This growth is driven by heightened smartphone demand and employee’s desire to perform work-related tasks such as sending emails even when they’re outside the office.
Of course, in 2020, the world experienced significant disruption resulting from the COVID-19 pandemic, which accelerated the work from home culture and, in many cases, made it necessary for employees to access work-related applications from their personal devices. While 95% of organizations allow the use of employee-owned devices in the workplace in some way, two out of three employees use their personal devices at work, regardless of the company’s BYOD policy. That means some employees are using their personal devices to access company networks and applications even if those activities are forbidden.
These findings illustrate the likelihood for employees to use personal mobile devices to conduct business activities whether or not the company has prior knowledge and/or policies regarding the use of personal devices. In other words, companies who choose to ignore the likely use of personal devices are ignoring what could be a serious security risk.
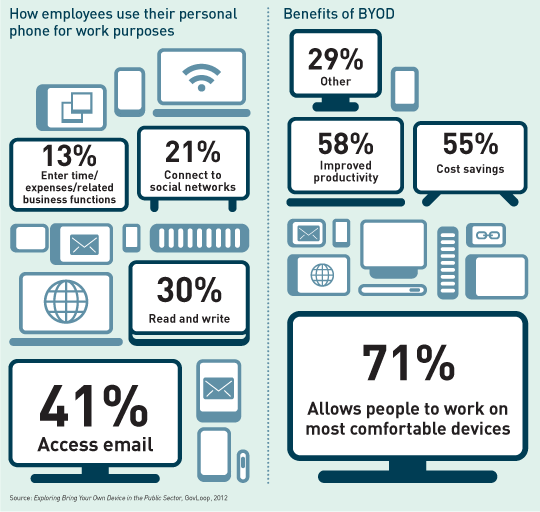
Image via Networking Space
Employers have two options: either embrace BYOD by enacting BYOD policies and security measures to make the practice a safer one, or prohibit BYOD entirely and find a way to enforce it. For most companies, it makes sense to embrace the BYOD trend and capitalize on the benefits it offers, such as increased employee productivity and greater employee satisfaction through better work-life balance, while implementing security measures that mitigate the risks involved.
Stakeholder and Employee Buy-In
To adapt to the growing use of BYOD among enterprises and SMBs, many companies may be inclined to jump immediately to policy creation, but that approach is often met with friction. The first step, before working on policy, is to gain both stakeholder and employee buy-in.
Stakeholders will be essential to the policy planning process, providing a variety of perspectives from various departments and interests within the organization. Executives, human resources, finance, IT operations, and the security team should be represented within a BYOD project management team and can each contribute to policy development.
In addition to these stakeholders, employee input is essential for creating effective BYOD policies. Blindly creating policies based solely on the company’s interests can backfire. Policies that are too restrictive or fail to offer support for the right devices will lead to a lack of participation by employees, ultimately wasting the resources the company invested in creating the policies.
An employee survey is an effective way to gain data on the devices employees currently use (and are likely to purchase in the future, as these devices must be supported by your company’s BYOD policy), what employees see as advantages and disadvantages to using their own devices for work purposes, and what applications they perceive as necessary to be able to carry out business tasks on their personal devices. For instance, some employees may have concerns about their own privacy should they use their personal devices for business. Armed with this data, you can begin to craft a BYOD policy that addresses these concerns and encompasses the full range of devices your employees are likely to use.
Defining a BYOD Security Policy
Defining a BYOD security policy is a critical step in maintaining company security when employees are bringing their personal devices to the workplace. TechTarget SearchMobile Computing outlines a few essential elements of a BYOD policy, including:
- Acceptable use: what applications and assets are employees permitted to access from their personal devices?
- Minimum required security controls for devices
- Company-provided components, such as SSL certificates for device authentication
- Company rights for altering the device, such as remote wiping for lost or stolen devices
In an article for CIO, Jonathan Hassell describes a few additional components of effective BYOD policies, such as specifying the permissible device types and establishing a stringent security policy for all devices. For example, consumers may opt not to utilize native security features such as the ability to lock device screens or require passwords because these features create additional steps that inconvenience users. Employees are motivated to make use of these simple features when clear company policies exist, and even simple measures can enhance company security.
Additionally, your BYOD policy should clearly outline a service policy for BYOD devices, including what support is available from IT for employees connecting to the company network, support for applications installed on personal devices, and support for resolving conflicts between personal applications and company applications.
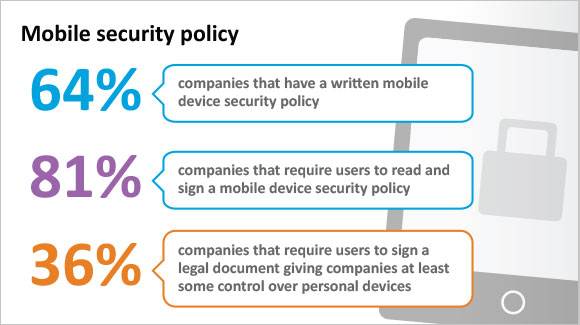
Image via TechTarget SearchSecurity
Your BYOD policy should clearly outline the ownership of apps and data, as well as the applications that are permitted or prohibited and reimbursement (e.g., will the company reimburse employees a standard use fee, pay for certain applications, or a portion of monthly bills?). It should also outline security requirements for BYOD devices (e.g., will the company provide a mobile device security application that must be installed on employee devices before they are granted access to company data or will employees be permitted to choose their own security solutions provided they meet criteria outlined by your IT department?).
Employee exits are also an important consideration when outlining your BYOD policy. When an employee leaves the company, what happens to the company data that may be stored on the employee’s device? Defining clear policies that explain the procedures that must be followed when an employee separates from the company, such as the wiping of the employee’s device by IT, should be explained in detail in written policies.
Finally, risks, liabilities, and disclaimers should be disclosed in a written BYOD policy. This includes company liability for an employee’s personal data, should a device have to be wiped for a security precaution, as well as employee liability for the leakage of sensitive company data brought about by employee negligence or misuse.
Example Elements of a BYOD Policy
There is a great deal of technology to better secure employee-owned devices. That said, a strong policy and widespread adoption of the policy is vital to ensuring proper (and secure) BYOD use in an organization. While each company is different, there are a number of elements (relatively) universal to most policies.
Password Provisions
For sensitive information, either belonging to the company or its customers, password protections are non-negotiable. Most organizations require strong passwords on mobile devices and computers. Some enact regular password changes every 30 or 90 days, for example. You also may want to consider 2-factor authentication for any applications and programs accessed from employee-owned devices.
Privacy Provisions
Company data belongs to the company, but it happens to be on a privately owned device. Privacy is a big deal, and your BYOD policy needs to address how you protect data while ensuring employees’ privacy. Some companies choose to tell workers to expect no privacy when using personal devices for work purposes.
Data Transfer Provisions
It only takes one person to use a new app with sensitive data for a breach to occur. If someone is using a certain app that’s unapproved to transfer data, and this application is breached, there could be serious legal ramifications. Data should be encrypted, password protected and only transferred on company mandated applications.
Proper Maintenance/Updates
Patches and updates not only provide new features, but also shore up the code from known attacks. Keeping devices and applications up-to-date is a major part of overall digital security and must be included in any company or private device use policy.
Common Sense Provisions
Technology is indifferent, but people have bad habits. Work selfies and short “vlogs” may occur, even when prohibited. And without provisions in your policy, device misuse is sure to occur more often. Other common-sense rules include things like:
- No device use while driving
- Limit personal calls while at work
- Do not take video (except possible in areas like break rooms with coworker permission)
Approved Applications
There are a number of apps used in the workplace. One study found employees use more than five business applications every day. Without a firm list of approved programs, your team may establish their own apps to use. Make sure to include dedicated secure messaging, email, CRM, and other apps and explicitly forbid the use of unapproved programs.
Upon Termination
Leaving company data on a personal device when that person retires, finds work elsewhere, or possibly gets terminated is a bad idea. Even worse is not having a specific set of procedures when this occurs. Upon any termination, an organization is obliged to ensure all data is removed from the device and permissions removed from company applications.
Data Wipe Procedures
The complexity of wiping data from an employee’s phone, tablet, or computer is enough to make some businesses provide all devices to employees. Parsing through multiple email accounts and deleting certain things from apps used for both private and company affairs isn’t easy. It’s for these reasons the steps are clearly laid out in the policy.
Accountability Provisions
A policy with a list of guidelines, yet without clear disciplinary action for failing to abide by those provisions, means your policy has no teeth. Your policy should describe in detail how accountability is tracked, measured, and enforced. Every member of the team should understand not only how devices are to be used but also the consequences of failing to keep company data safe.
Evaluate Your Technology Capabilities
In addition to creating and communicating your BYOD policy, you must ensure that you have the right technology resources at your disposal. An evaluation of your current capabilities will help to identify and fill these gaps to ensure a successful BYOD rollout.
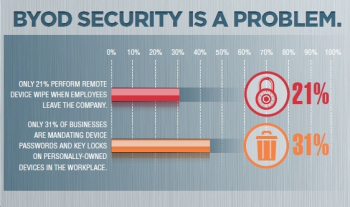
Image via Brian Pennington
Lack of oversight is one of the most common concerns surrounding BYOD implementation. Companies implementing BYOD policies need to have adequate staff in their IT support departments to help employees get set up and provide ongoing support and monitoring. Not all solutions are compatible with all devices or operating systems. Companies may opt to purchase a software solution with cross-device compatibility, or they may place greater importance on features and offer a different solution for different devices and OS.
Companies should implement measures and procedures for verifying installation of security solutions on all devices accessing company data. They should also create protocols for identifying and enforcing policies related to the evaluation of the risks of various apps and determining which specific applications are deemed safe as well as which applications should be prohibited. Finally, if reimbursement is included in the BYOD policy, budgetary issues should be considered and appropriate resources allocated for this purpose.
Considering BYOD Security Solutions
Once your systems and protocols are in place, providing ongoing employee education on the importance of acceptable use as well as basic data security hygiene is critical for BYOD success. Beyond this, the right security solutions can minimize your BYOD risk and enable your policy to run smoothly. There are several elements that should be addressed by an effective BYOD security solution. The ideal solution is one that encompasses several or all of these elements and facilitates a comprehensive mobile security strategy. Below are short descriptions of various security measures which may be used as part of a comprehensive BYOD security program.
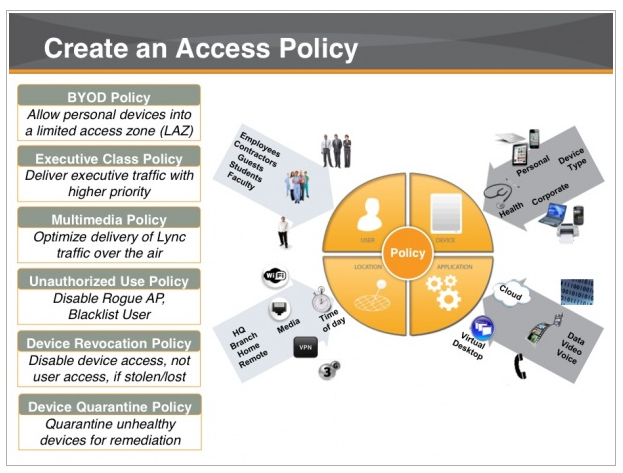
Image via Flickr by Bernard Goldbach
Encryption for data at rest and in transit
Because BYOD usage takes data outside of the control of many other enterprise security measures, it is important that organizations encrypt sensitive data at rest and in transit. Encryption ensures that the contents of sensitive files are protected even in a worst-case scenario such as a stolen device or traffic being intercepted over an unsecure network.
Requiring the use of strong passwords offers some protection, but encryption is better. As this article on the InfoSec Institute notes, “To ensure protection, organizations need to implement encryption for the entire duration of the data lifecycle (in-transit and at-rest). And to prevent unauthorized access and maintain the encryption in case of a security breach, the IT department of the concerned organization should take control of encryption keys.”
Application installation control
There are some controls available with certain devices and operating systems that IT can utilize to exert control over the apps installed on an employee’s device. For instance, Apple iOS devices can be configured to deny access to the App Store, and for Android devices, companies can make use of Android Enterprise for a managed Google Play portal that contains only approved applications (among many other useful features for BYOD).
However, restricting an employee’s ability to download or install applications on their own devices for personal use isn’t a practical solution for most companies. These methods are similar to measures taken for parental control purposes, so naturally, employees are likely to feel as though this is an infringement on their personal freedoms. Most employees have the expectation that they will be able to use their personal devices as they choose when they’re not on the clock, conducting business, or connected to a secured company network, making other solutions more practical for BYOD security. It’s worth noting that Android Enterprise offers a containerized environment to separate work and personal applications and data, which allows companies to have better control over devices used for work purposes without limiting an employee’s personal use of their device. We’ll discuss containerization in more detail below.
Mobile device management
Mobile device management (MDM) solutions offer a balance between total control for employers and total freedom for employees, offering the ability to deploy, secure, and integrate devices into a network and then monitor and manage those devices centrally. The MDM field is still finding its footing and is not without its share of problems. For instance, this article in CIO reports that some enterprises could take advantage of more advanced features available with MDM, creating a less-than-ideal user experience that’s too restrictive and leading employees to resist the enterprise’s BYOD program.
Containerization
Containerization is increasingly being offered in conjunction with (or paired with) MDM solutions. Containerization is a method by which a portion of a device can essentially be segregated into its own protected bubble, protected by a separate password and regulated by a separate set of policies, from the remainder of the applications and content on the device. This allows employees to enjoy full, uninhibited use of their devices on their own time without introducing security risks to the company’s network. When a user is logged into the containerized area, personal apps and other features not managed by the container are inaccessible. Containerization is an appealing solution that doesn’t limit employees’ ability to use their personal devices as they choose, while eliminating the possibility of employees using or accessing apps that don’t meet the company’s security threshold when working.
Containerization limits corporate liability without impacting personal use, but on the downside, it doesn’t protect employees’ personal data on devices that are lost or stolen and must be wiped. This is a challenge that’s easily overcome with proper personal data backup.
Blacklisting
Blacklisting is a term that describes the process of blocking or prohibiting specific applications that are determined to pose a risk to enterprise security. Blacklisting is also a method some companies use to restrict employee access to apps that can hinder productivity, such as games or social networking apps. File-sharing services are another category of apps that often find themselves on blacklists, as companies fear that sensitive information could be shared with unauthorized third parties, either intentionally or inadvertently, by employees.
While it can be effective by limiting access to applications that don’t meet your company’s security criteria, blacklisting is not often used for BYOD, as the process means controlling access to applications on employees’ personal devices both during work and during off-hours. Naturally, this poses an issue for some employees who enjoy playing Pokémon GO when they’re not at work.
Whitelisting
Whitelisting is simply the opposite of blacklisting. Instead of blocking access to a list of specific applications, whitelisting allows access only to a list of approved applications. It’s often considered a more effective process simply because of the sheer number of applications and websites that exist. Waiting until an employee has downloaded an app and used it to transmit data to determine that it poses a security risk is sometimes too little, too late.
Whitelisting circumvents this issue by simply not allowing access to anything unless it has been pre-approved as safe by IT. Of course, like blacklisting, this can create problems for BYOD by blocking employees’ access to apps that they might want to use when they’re not at work.
Other BYOD security measures
There are a variety of other security measures that are sometimes used as part of a comprehensive BYOD security program. Antivirus software installed on individual devices, for instance, is often a staple of such security programs. Companies may purchase a volume license and install software on BYOD devices or simply require employees to install their own and verify with IT that their devices are protected. With more malware targeting mobile devices, the risk of such a malicious program impacting the company network by way of an employee’s personal device is very real.
Monitoring is another component sometimes used as part of a BYOD security program, albeit with mixed opinions. IT could implement systems that monitor the GPS location of employee devices, or Internet traffic on individual devices. While these monitoring systems can prove beneficial for detecting unusual activity or locating a lost device, many consider these solutions to venture too far into employees’ privacy.
The bottom line is that BYOD security, like enterprise security, requires a multi-faceted approach that addresses the potential risks while minimizing intrusions on employee privacy and usability when it comes to personal use. Context-aware security solutions that provide control over user access, applications, network connectivity, and devices, in addition to encryption capabilities, combine the key elements necessary for ensuring enterprise security in the BYOD landscape. Enterprises embracing these solutions capitalize on the benefits and reap the rewards of BYOD, such as employee productivity and satisfaction due to greater work-life balance, while effectively mitigating the security risks that once plagued companies adopting BYOD.
Further Reading on BYOD:
- BYOD Security: Expert Tips on Policy, Mitigating Risks, & Preventing a Breach
- BYOD security policy: Mitigate BYOD risk with device requirements
- Bring Your Own Device: Security and risk considerations for your mobile device program
- BYOD: Why the biggest security worry is the fool within rather than the enemy without
- The Future of BYOD: 6 Key Trends for 2020
- Survey: BYOD security remains spotty, with users unaware or unmotivated about risks
- Best Practices to Make BYOD, CYOD and COPE Simple and Secure
- A Look at BYOD Environments and the Role They Play During the COVID-19 Pandemic
- Half of U.S. businesses have no formal BYOD policy for security
- BYOD Security: 5 Ways CIOs Can Securely Embrace BYOD
- Is a Remote-Wipe Policy a Crude Approach to BYOD Security?
- BYOD: IT’s Security Nightmare or a Dream Come True?
- 5 ways to shore up security in your BYOD strategy
- BYOD security: Tips to mitigate the risks
- Network Security Concerns With BYOD

