The Role of Security Analytics in Information Security Programs
18 infosec pros and analytics experts reveal the role of security analytics in information security programs today.
What is Point-of-Sale (POS) Malware? How it Works and How to Protect Your POS system
Learn how POS malware works and how to protect against it in Data Protection 101, our series on the fundamentals of information security.
Hilton Was Fined $700K for a Data Breach. Under GDPR It Would Be $420M
Consider $2 per lost record versus $1,200 per lost record. That’s the difference between what Hilton will pay to New York State versus what it will pay to EU regulators once the GDPR takes effect in May.
Oracle Issues Emergency Patch for Remote Takeover Vulnerability
Oracle released an out-of-band patch late last week to address a critical remote takeover vulnerability.
What is Event Correlation? Examples, Benefits, and More
Learn about event correlation in Data Protection 101, our series on the fundamentals of information security.
What Happens When There’s No Data Left to Steal?
What would it mean to have a post-breach society, in which there’s no data left to steal because it has all been stolen? We may be about to find out.
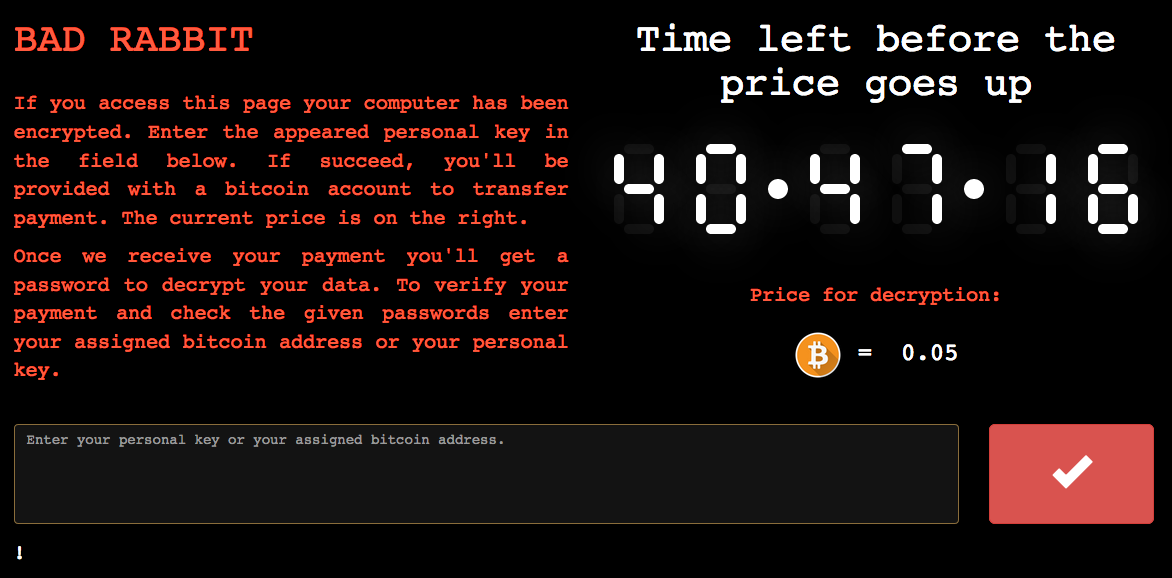
Bad Rabbit Ransomware Hits Russia, Ukraine
A previously unknown strain of ransomware, Bad Rabbit, hit roughly 200 targets across Russia, Ukraine, and Bulgaria, on Tuesday.
Endpoint Detection and Response (EDR) Solutions: Expert Tips & Strategies
12 security experts reveal the best approaches and solutions for Endpoint Detection and Response.
What is Log Analysis? Use Cases, Best Practices, and More
Learn about log analysis in Data Protection 101, our series on the fundamentals of information security.
If You Want an Apple Password, Just Ask Nicely
If you’re an iPhone user, you’re likely well acquainted with the system dialog boxes that iOS spits out on a regular basis, asking for our Apple ID password. It happens on a fairly regular basis, when you’re installing new apps or iOS updates or when you’ve been signed out for some reason. But it’s incredibly simple for non-Apple apps to produce the exact same dialog boxes and collect users’ credentials, making for a potentially highly effective phishing tool.
Don't Fall Behind
Get the latest security insights
delivered to your inbox each week.