Biometrics Finally Ready for Prime Time
There are relatively few things we know for certain in the security industry, but one of them is that the password has become nearly useless as an authentication mechanism. Users are bad at creating them and modern computing resources have advanced to the point that attackers have little trouble cracking even complex passwords.
What is Spear-phishing? Defining and Differentiating Spear-phishing from Phishing
Learn about spear-phishing attacks as well as how to identify and avoid falling victim to spear-phishing scams.
Sister Act: Medical Peeping Tom Spawns Class Action Lawsuit
A case involving a Canadian healthcare group alleges that patient records were left exposed to a medical assistant and “Peeping Tom” who abused her access to snoop on patients’ confidential data – including information on her sister.
What is Driving Your Data Protection Agenda? Determining the Right Approach to DLP
Understanding your goals is a critical first step in your journey toward building the right data protection program for your organization. Part six of our Definitive Guide to Data Loss Prevention series examines some of the key considerations for this process.
Seek Evil, and Ye Shall Find: A Guide to Cyber Threat Hunting Operations
On the heels of our Cyber Hunting Safety webinar, here’s a guide on where to start in your own cyber threat hunting efforts.
What is Ransomware? Understanding and Protecting Against Ransomware Attacks
Learn more about ransomware and how to protect against ransomware attacks in Data Protection 101, our series on the fundamentals of information security.
Digital Guardian Advanced Threat Protection: Visibility and Behavior-Based Detection (Video Demo)
Digital Guardian’s data protection capabilities go well beyond traditional DLP – watch our latest video demos to learn how our Advanced Threat Protection provides unparalleled visibility and behavior-based detection of advanced attacks.
IBM Employee, Linux Kernel Hacker, Charged with Spying for China
The U.S. Department of Justice filed charges against a 30 year-old IBM employee who absconded with source code IBM uses to manage cloud software.
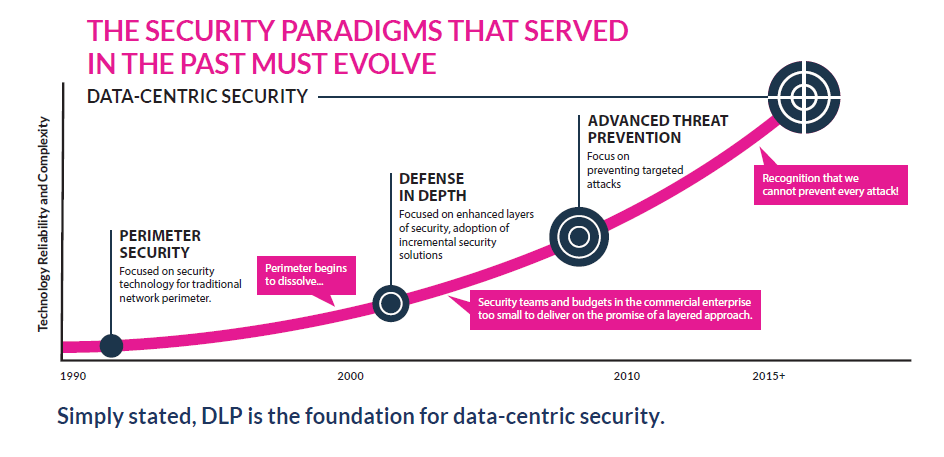
All Trends Lead to Data-Centric Security
As traditional approaches to security become less effective, enterprises are shifting towards a security model that focuses on data protection at its core. Learn more about this shift to data-centric security in part five of our series, The Definitive Guide to Data Loss Prevention.
Security Investments and the Definition of Insanity
A survey of IT professionals finds companies continuing to prioritize network perimeter protections – with little to show for it.
Don't Fall Behind
Get the latest security insights
delivered to your inbox each week.