Why Threat Aware Data Protection
for Manufacturing
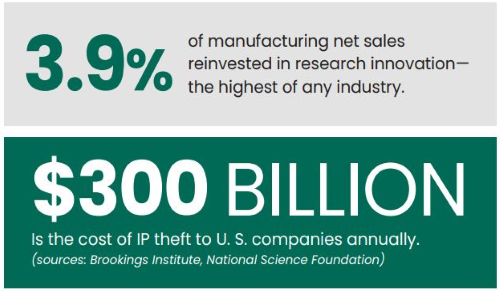
All manufacturers must have a strategy in place to ensure the free flow of information across their global supply chains, while safeguarding that information from malicious insiders, nation states and cyber-criminals. Do not underestimate the capability and persistence of your adversaries. They are smart, nimble and more motivated than ever. They won’t stop until they reach their target—your IP.
The most valuable IP for manufacturers is usually unstructured data, such as CAD files, source code, and formulas. The problem is, most data loss prevention solutions aren’t very good at recognizing or protecting this unstructured data.
Key Challenges
Manufacturers must protect their data from a range of threats:
State Espionage
Well-funded attacks by foreign governments or hacker proxies seeking economic, political or military advantage.
Insider Threats
Data loss by current or former employees, whether by malice or mistake, via egress channels such as email, media, mobile and cloud storage.
Corporate Espionage
Competitors stealing industrial secrets for market advantage, monetary gain or revenge.
Third Party Leaks
Trusted supply chain partners, suppliers, contractors and outsourcers leak data via backdoor access points.
How Digital Guardian Can Help
Our threat aware data protection platform secures your sensitive assets against insider and outsider threats.
Understand: What Data To Protect
With its deepest visibility into data, user and system events, the Fortra™’s Digital Guardian® platform can identify and tag sensitive data in real-time even before you develop formal policies. We accurately identify both structured and unstructured data – like CAD files, source code, business processes and formulas – the most valuable IP for manufacturers.
Understand: When Data Is At Risk
Detecting when data needs to be protected means understanding risky user behavior, unauthorized system access, data movement or process violations. The Digital Guardian platform harnesses our deep visibility and real-time analytics to flag anomalous activity and provides high fidelity alerts. Our solution monitors enterprise data wherever it lives and wherever it is shared – across networks, storage, endpoints, or in the cloud – performing equally across Windows, Mac OS or Linux operating systems.
Enforce And Educate: Flexible & Automated Controls
Digital Guardian employs flexible and automated controls to ensure that sensitive data does not leave your organization. Our context-based and behavior-based rules automatically prompt users or block insider and outsider threats in real-time. Illegal downloads or exfiltration can be blocked and contained before the data is gone.
Share Data Securely Across Your Supply Chain
Digital Guardian empowers your organization to share data securely across the enterprise and with all partners, contractors and suppliers while also preventing unauthorized data access.
Comply With Key Regulatory Requirements
Digital Guardian provides a detailed audit trail to support demonstration of compliance with International Traffic in Arms Regulations (ITAR), Export Administration Regulations (EAR), and other regulatory requirements.