User Activity Monitoring for Federal Agencies
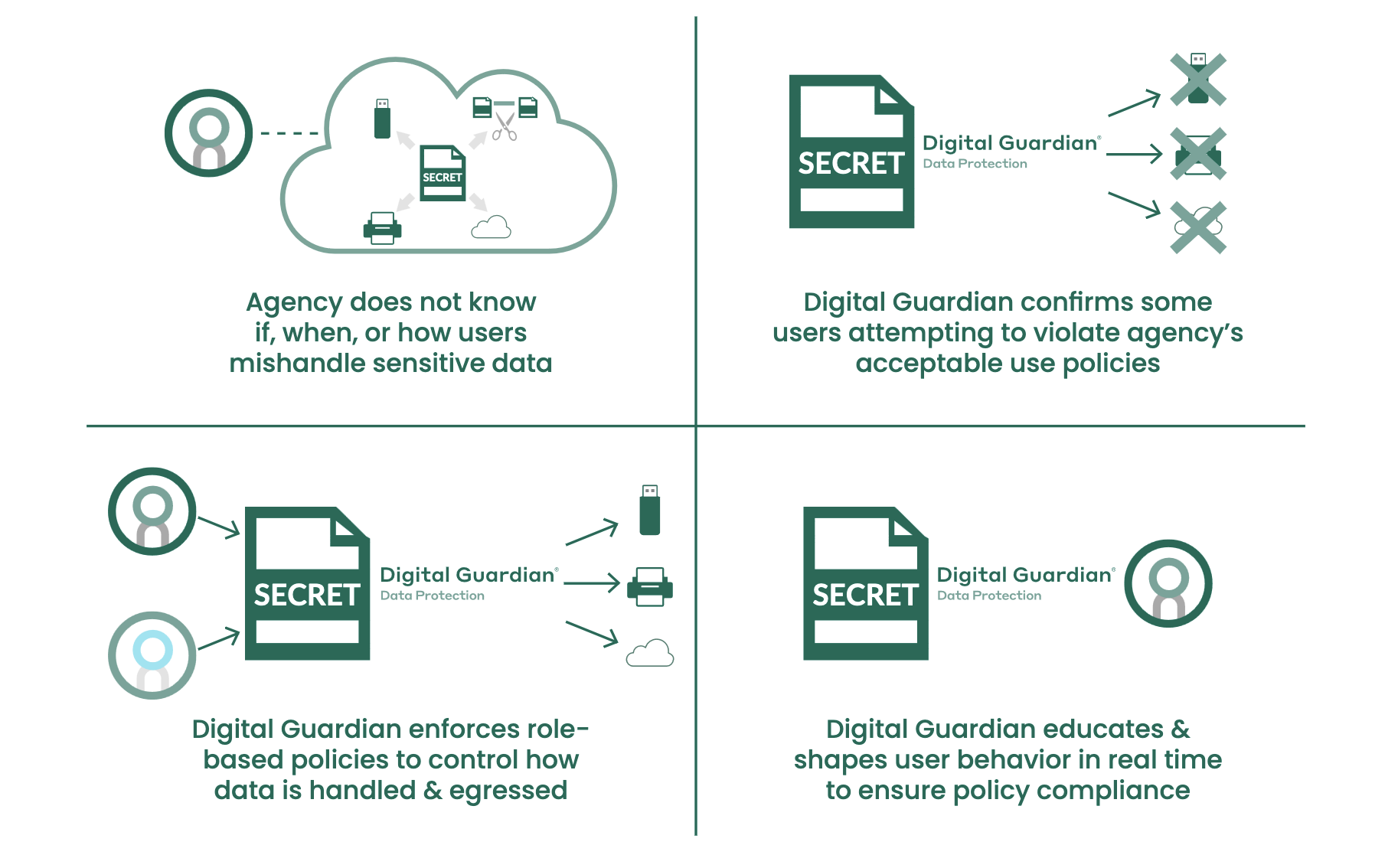
Traditional federal security solutions tend to focus on infrastructure, but overlook the employee or contractor. This can create a blind spot for your agency, preventing you from knowing what data users are accessing and what they’re doing with it. This security void, combined with increasingly open networks among agencies, contractors and programs, leaves your sensitive data vulnerable.
Visibility to Instantly Detect Suspicious User Behavior
Fortra™’s Digital Guardian® User Activity Monitoring offers complete user visibility and control regardless of what users are running, what they’re running it on, and whether or not they’re on the network. Your agency can audit, monitor, limit and report on all end-user activity in real-time, and also perform investigative tasks. Our solution helps government pros classify, categorize and tag data so every action is tracked and accounted for – providing a detailed audit trail that can aid investigations and help your agency show compliance with mandates like Insider Threat Executive Order 13587.
Whether it’s deployed on premise or as a cloud-based managed service, Digital Guardian begins to work as soon as it’s installed, enabling instant detection, investigation and containment of suspicious activity.

MANY GOVERNMENT WORKERS DON’T CONSIDER SECURITY WHEN SHARING WITH THIRD PARTIES
31% of government workers said they never or only occasionally consider data security or privacy issues into account when they share information with vendors or other external stakeholders.
- Wall Street Journal, Survey: Many Government Employees Use Personal Email for Work
User Activity Monitoring in Action