Why Read This Guide?
Careful cyber security incident response planning provides a formal, coordinated approach for responding to security incidents affecting information assets. This e-book provides easy-to-follow steps for crafting an incident response plan in the event of cyber security attacks.
What Data is Sensitive?
IF YOU ARE... | GO TO... |
|---|---|
New to Incident Response Plan | Part One: Incident Response Do's and Don'ts |
Not sure where to start? | Part Two: Get Ready |
Familiar with Incident Response Plans, but how do I implement in my organization | Part Three: The Five Stages of Incident Response |
Worried about managing Incident Response with limited resources | Part Four: Managed Detection & Response |
Looking to understand what makes Fortra’s Digital Guardian® different | Appendix: Digital Guardian — No-Compromise Data Protection |
PART ONE Incident Response Do's And Don'ts
5 Things Not To Do During An Incident
PANIC
Do not panic. It's the worst thing you can do. You want to remain calm and having an IR plan will help to do just that. An IR plan will provide you with a predefined path that outlines the best course of action to take during an incident.
SHUT DOWN SYSTEMS
Do not shut down infected systems. By shutting them down, you could lose volatile data that contains important forensic information. This information can be essential in determining the timeline of what transpired.
SOCIALIZE
Do not discuss the incident with others unless otherwise directed. It’s important to be cautious about the audiences that you choose to communicate with about an incident that has just begun to unravel.
USE DOMAIN ADMIN CREDENTIALS
Do not use domain administrative credentials when accessing systems environment. Threat actors patiently wait for a user with enterprise-wide access to login in order to capture the password to gain complete control over the environment.
NON-FORENSIC TOOL USAGE
Do not execute any non-forensic software on the infected systems because this will overwrite the timelines associated with the attack in the Master File Table.
4 Things To Do During An Incident
COLLECT DATA
Collect volatile data and other critical artifacts off the system using forensic tools. Forensically sound tools have the ability to connect to the system without modifying any timestamps on the device.
EXTERNAL INTELLIGENCE
Gather external intelligence based on identified indicators of compromise (IOC). Search the web for intelligence about specific MD5s, IP addresses, domains that you discovered during your initial incident investigation. You are attempting to identify what the potential infection is or what type of malware may have been executed within the environment.
SAFEGUARD
Safeguard systems and other media for forensic collection.
COLLECT LOGS
Collect the appropriate logs. This may include Windows Events, Firewall, Netflow, Anti-Virus, Proxy, etc. It is important to view the story both at the network and at the endpoint level.
PART TWO: Get Ready
Build Your IR Team
An Incident Response team is a centralized team that is responsible for incident response across the organization. The team receives reports of security breaches, analyzes the reports and takes necessary responsive measures. The team should be composed of:
Get Cross-Functional Support
All business representatives must fully understand and advocate the Incident Response plan in order to ensure that the plan is properly executed, smooth information flow occurs and remediation takes place
Management
Management buy-in is necessary for provision of resources, funding, staff, and time commitment for incident response planning and execution.
Human Resources
Human Resources is called upon when an employee is discovered to be involved with the incident.
Audit And Risk Management Specialists
The specialists help develop threat metrics and vulnerability assessments, along with encouraging best practices across the constituency or organization.
General Counsel
The Attorney’s role is to ensure the forensic value of any evidence collected during an investigation in the event that the company chooses to take legal action. An attorney can also provide advice regarding liability issues in the event that an incident affects customers, vendors, and/or the general public.
Public Affairs
The Public Relations’ role is to communicate with team leaders, ensuring an accurate understanding of the issue and the company’s status, so as to communicate with the press and/or informing the stockholders about the current situation.
Communication Within and Across Teams is Critical
EXPERT TIPS
"Communications during an incident should be conducted in a manner which protects the confidentiality of the information that is being disseminated. The incident response manager should be the central point of all communication and only those with a valid need-to-know is included in communications regarding key incident details, indicators of compromise, adversary tactics and procedures. Securing this communication so that Mr. Threat Actor is unable to snoop your messages is extremely vital to avoid tipping them off that an on-going investigation is occurring. Any indication that ‘You’re On to Them’ may lead to swift changes by the attackers to further mask their activity."
- Fortra Team
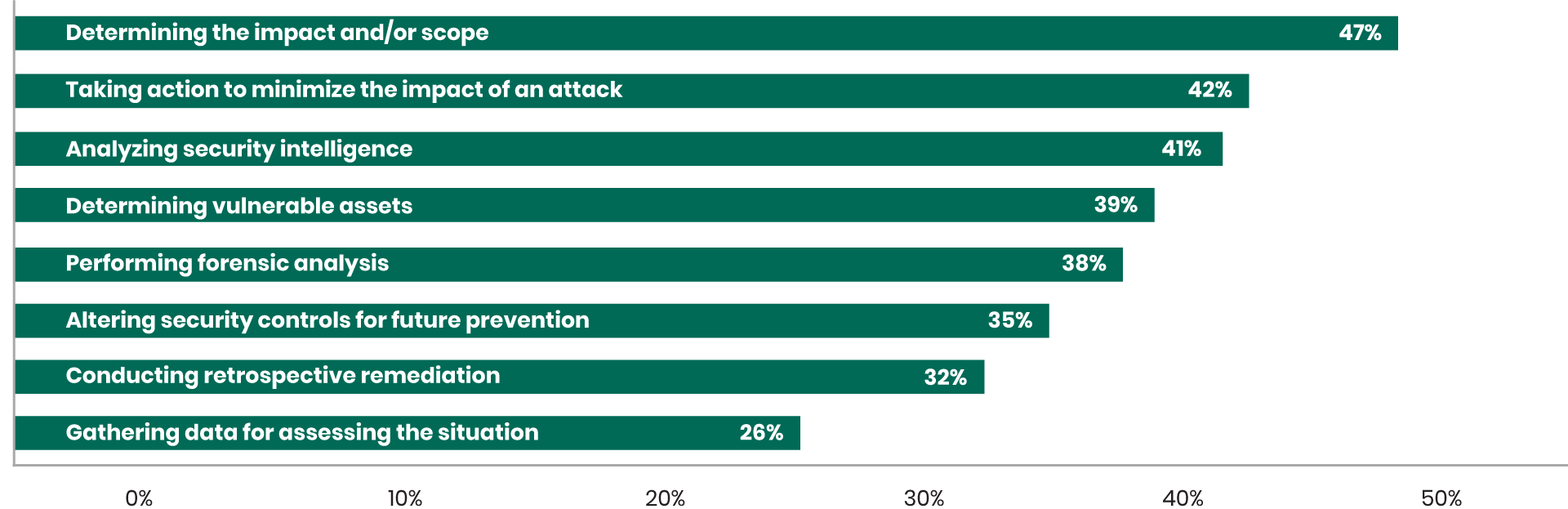
Most Time Consuming IR Tasks
Create Your Incident Classification Framework
Creating an Incident Classification Framework is a critical component in enabling the proper prioritization of incidents. It will also help you derive meaningful metrics for future remediation purposes. We recommend a two-tiered classification scheme.
Incident Classification Framework

Note: Incident classification may change several times during the incident management lifecycle as the team learns more about the incident from the analysis being performed.
Incident Classification Framework
This first tier of classification organized by category, type and severity give the information you need to prioritize incident management.
Incident Taxonomy
Taxonomy gives you additional information you need to identify root cause, trends and intelligence. It also provides you with the information for essential incident response metrics.
Incident Taxonomy (CONT.)
Taxonomy gives you additional information you need to identify root cause, trends and intelligence. It also provides you with the information for essential incident response metrics.
Detect Threat Actors Through Antivirus Logs
EXPERT TIPS
"Your good ol' antivirus solution may only detect 10 to 15 percent of malware, but your antivirus logs may contain critical indicators of the attack. When threat actors break into your environment, one of their first objectives is to acquire passwords by running a credential dumping program. Your antivirus might detect this activity the first time and block the program from executing. But further executions of different credential dumping programs may go unnoticed, so it's important to alert on any activity associated with these types of malicious tools. Having the log of the first attempt is critical because that might be the single thread that you need to pull and unravel to identify a potential incident."
- Fortra Team
PART THREE: 5 Stages of Incident Response
1. Preparation
“Preparation is the key to effective incident response.”
Develop And Document IR Policies
Define Communication Guidelines
Conduct Cyber Hunting Exercises
Assess Your Threat Detection Capability
Incorporate Threat Intelligence Feeds
Expert Tips
5 Tips To Make Incident Communication Effective
1. Avoid using speakerphones. You don’t want people in the hallway to overhear your discussions.
2. Avoid using instant messenger systems unless they are encrypted end to end or secure in some other way.
3. Try to avoid using email as much as possible because threat actors may have access to your email systems (“Man in the Mailbox”) watching every message coming in and out.
4. Communicate in-person if possible and use secure lines for phone conversations.
5. Use pre-shared access codes for authenticating users for bridge/conference calls.
2. Detection and Reporting
The focus of this phase is monitoring and correlation of security events in order to detect, alert, and report on potential security incidents.

MONITOR
Monitor and correlate security events occurring across various systems in your environment. These systems include firewalls, intrusion prevention systems and data loss prevention.
DETECT
Detect potential security incidents through correlating alerts within a SIEM solution
ALERT
Analysts create an incident ticket and document any initial findings and assign an initial incident classification.
REPORT
Initiate reporting process including accommodation for regulatory reporting escalations.
Centralized Logs Can Often Tell You The Story
EXPERT TIPS
"A centralized SIEM that ingests logs from all of your security systems—such as antivirus, firewall, intrusion prevention systems, data loss prevention, is a critical tool. A SIEM enables you to search across all devices within your enterprise to identify malicious activity and enable you to trace back and determine how a potential threat gained access. What boxes did they touch? What firewall did they go through or what data leak prevention logs may have been generated when they were on a system. Incident Responders need to answer these types of questions and having a SIEM will make it easier in doing so. "
- Fortra Team
3. Triage and Analysis
The triage and analysis phase initiates the bulk of the effort in properly scoping and understanding the security incident. Resources should be engaged to collect data from tools and systems for further analysis and identifying Indicators of Compromise. These individuals should have indepth skills and a detailed understanding of Live System Response, Digital Forensics, Memory Analysis, and Malware Analysis. As evidence is collected, the analyst will now focus on 3 primary areas:
END POINT ANALYSIS
- Determine what tracks may have been left behind by the threat actor.
- Gather the artifacts needed to build a timeline of activities.
- Analyze a bit-for-bit copy of systems from a forensic perspective & capture RAM to parse through and identify key artifacts of what occurred on a device. RAM is feature rich with data on activities executed by a threat.
BINARY ANALYSIS
- Investigate malicious binaries or tools leveraged by the attacker in order to document the purpose and functionality of those programs. This analysis is performed in two ways:
- Behavioral Analysis - Executes malicious program in a VM to monitor its behavior.
- Static Analysis - Reverse engineer the malicious program in order to scope out the entire functionality.
ENTERPRISE HUNTING
- Enterprise hunting is performed to identify all systems impacted by a security incident.
- Analyze existing systems and event log technologies to determine machines in scope of a compromise.
- This will allow the responder to document all compromised accounts, machines, malware used, etc. so that effective containment and neutralization can be performed.
4. Containment and Neutralization
This is one of the most critical stages of the incident to ensure that a malicious infection is completely eradicated from the environment. The strategy for containment and neutralization is based on intelligence and indicators of compromise developed throughout the incident analysis phase. After the system is restored and verified that there are no further security compromises, normal operations can resume.

COORDINATED SHUTDOWN
Once you have identified all systems within the environment that have been either accessed or compromised by a threat actor, perform a coordinated
shutdown of these devices at the same time. When performing the coordinated shutdown, a notification is sent out to all IR team members to gain alignment
on timing and the resources required to perform the remediation.
WIPE AND REBUILD
Wipe the infected devices and rebuild the operating system from the ground up. Change passwords of all compromised accounts.
THREAT MITIGATION REQUESTS
If you have identified domains or IP addresses that are known to be leveraged by threat actors for command and control, issue threat mitigation requests to block the communication at all egress channels.
Coordinate System Shutdown
EXPERT TIPS
"I recall once during an incident that a compromised server was not shutdown during a coordinated effort. It actually alerted the threat actors and they knew that something was going on within our environment and that we were attempting to kick them out. So they immediately came back in, not even within 10 minutes of those servers being shut down to move laterally again within the environment and installed a whole set of new malware and tools. We had to go through the entire process again of conducting triage and analysis. Therefore, it is extremely important that all parties involved in a neutralization process follow the instructions carefully to avoid this from happening. "
- Fortra Team
Never Let A Good Incident Go To Waste
EXPERT TIPS
"Now is the time to answer those critical questions: How did this happen? What were they targeting? What controls should we have had in place that would’ve prevented this intrusion from occurring in the first place? Are there specific areas within our security that require additional resources or funding to cover those gaps? As you think through these questions that relate to the Incident at hand, also begin to think about the organization in general and what security metrics could be reported each week/ month/quarter to further shed light on any chinks in the armor. Develop a heat-map of your Cyber Security Readiness Scorecard and include areas such as Vulnerability Assessments / Remediation, SIEM Event Collection, Continuous Visibility, Security Configurations, etc. A scorecard that appears to have been dipped in red paint, indicating serious control gaps, will undoubtedly get the attention that it deserves." - Fortra Team
5. Post-Incident Activity
1. COMPLETE INCIDENT REPORT
2. MONITOR POST-INCIDENT
3. UPDATE THREAT INTELLIGENCE
4. IDENTIFY PREVENTATIVE MEASURES
5. GAIN CROSS-FUNCTIONAL BUY-IN
Be Sure To Reset Credentials
EXPERT TIPS
"You have to be sure to reset any passwords that may have been compromised during the incident. It’s important to note though that, once a threat actor has gained access to a system they immediately dump the credentials. Consequently, they have a whole bunch of credentials and it might not just be the one or two that they’ve used. Therefore as part of the postincident monitoring, identify any failed login attempts with those accounts. It could be a potential indication that they’re back in within the environment attempting to use what they've previously harvested."
- Fortra Team
PART FOUR: Managed Detection & Response
When Does It Make Sense To Consider EDR As A Service?
If any of these apply to your organization it may make more sense to outsource or augment your incident response team with a Managed Detection & Response Program:
Managed Detection & Response Program
The Latest Defense Strategies And Intelligence
Our Managed Detection & Response Program is led by an experienced cybersecurity expert, with the practical knowledge from building a program at a Fortune 100 organization. The program combines security researchers and analysts’ expertise, Digital Guardian’s No-Compromise Data Protection Platform and a centralized threat intelligence management system. This combination enables Digital Guardian to detect and remediate threats faster and more efficiently. You can expect the highest level of protection from threats including polymorphic malware, zero-day attacks, advanced persistent threats (APTs), ransomware and attacks involving sophisticated data theft methods.

Why Digital Guardian?
Real-Time Visibility
Threat Intelligence
Eyes On Glass Identifying Your Real Risks
Indicators of Execution
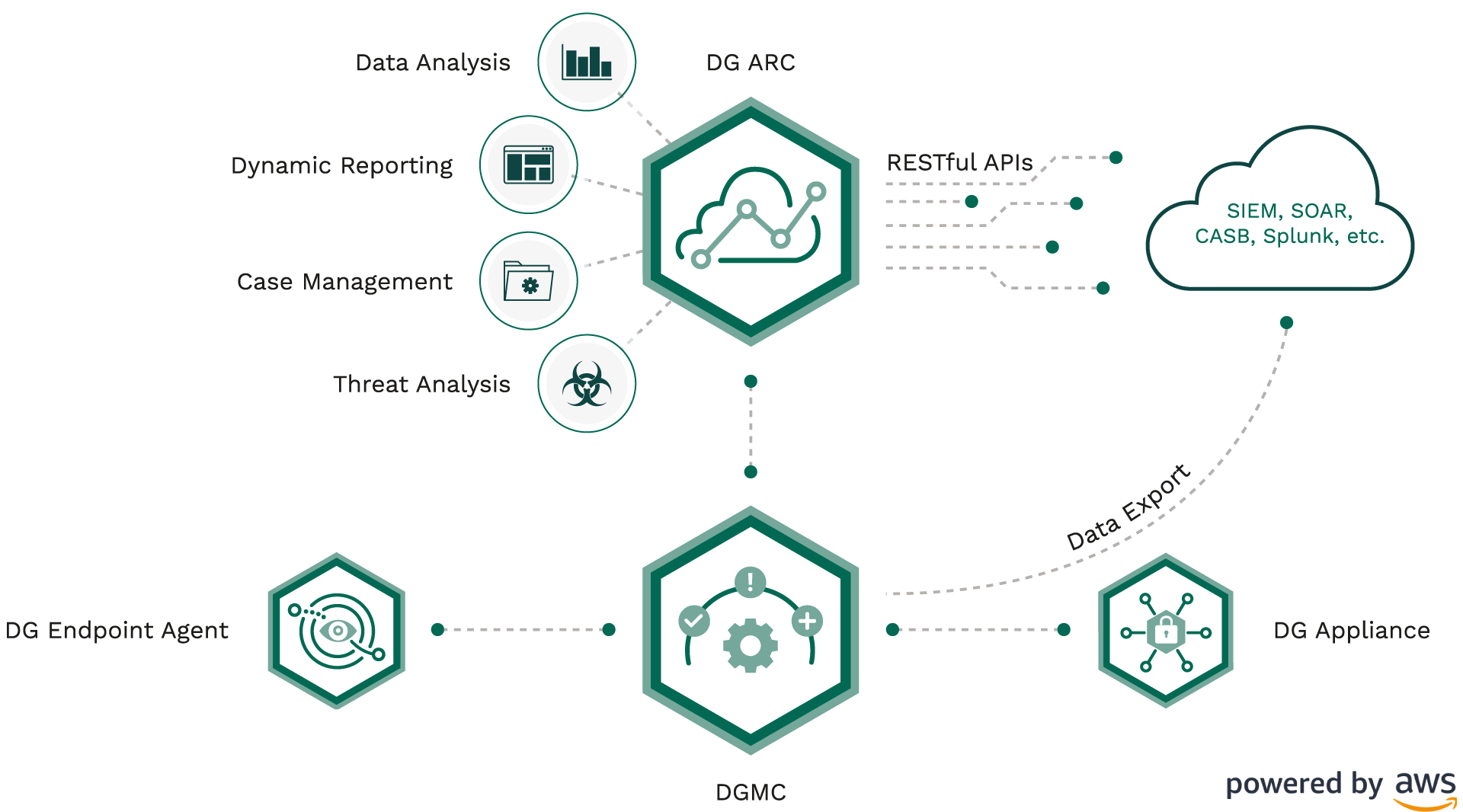
APPENDIX: Digital Guardian No-Compromise Data Protection Platform
Digital Guardian Data Protection Platform
No-compromise data protection for your nocompromise organization. Our platform, powered by AWS, performs on traditional endpoints, across the corporate network, and cloud applications, making it easier to see and block threats to sensitive information. Cloud-delivered means simplified deployment, cross platform coverage for no gaps, and flexible controls to stop the riskiest behavior. Available either as SaaS or managed service deployment, Digital Guardian gives you the deployment flexibility to match your enterprise needs.