In part four of this series we looked at the 7 Trends Driving the Resurgence of DLP. The traditional approaches to security fall short in helping you address these trends. As a result, the data-centric security model has become an increasingly popular approach. At the heart of data-centric security is data classification and data loss prevention (DLP).
Let’s look at the shortcomings of traditional approaches and why data-centric security is what’s next.
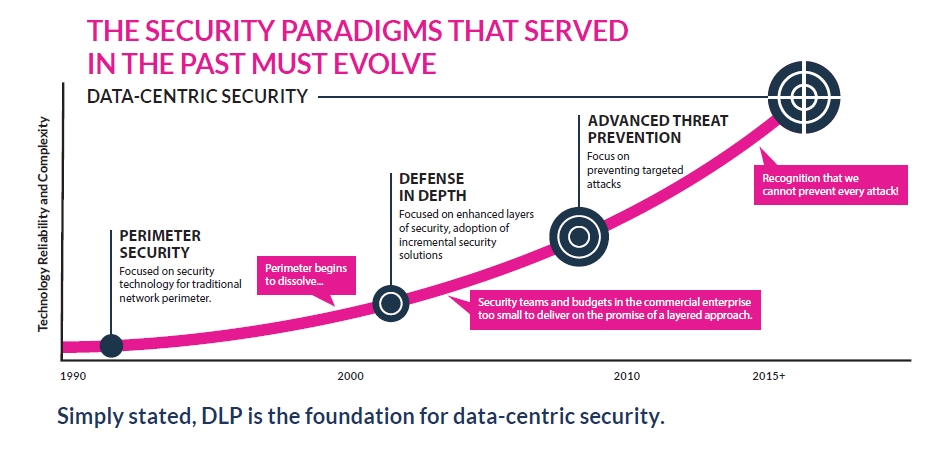
Perimeter Security
It used to be that a predictable, IT controlled network contained your sensitive data. You could use firewalls and IDS to physically insulate your infrastructure from outside threats. But that perimeter has dissolved. Users are increasingly connecting via the public Internet or mobile devices. To quote Forrester Research, “There is fatal flaw in the main assumption underpinning perimeter-based security — the assumption that there is a ‘trusted’ internal network where data is safe and an ‘untrusted’ external network where data is unsafe. This implicit trust assumption is both incredibly naïve and untenable.”1
Network perimeter technologies are still important, but relying on them to protect sensitive data in a perimeter-less world is extremely risky.
Defense-in-Depth
The traditional approach of improving your security posture with more and more layers is also under attack by the force of trend #7 – the security talent shortage. This shortage is the Achilles heel of complex, layer-upon-layer security models. Among our customer base we are seeing CISOs working to simplify their security strategies, cut back on layers and rethink priorities.
Advanced Threat Prevention
With all the high profile breaches in the past few years, many organizations have shifted big resources to advanced threat prevention. But the reality is that:
- You’ve probably already been compromised.
- You can’t prevent every attack.
According to the U.S. DoJ Assistant Attorney General for National Security, “every internet connected device will eventually be compromised. The only question is when.”
Why Data-Centric Security
Data-centric security is a more pragmatic approach. In essence, with data-centric security you shift your focus from securing networks, applications and endpoints to identifying, controlling and securing your “crown jewel” data. Instead of trying to protect everything, you’re focusing on protecting what matters most – your most important data.
With data-centric security, effective risk-based security is centered on three goals:
- Understanding where sensitive data is located, how it flows in the organization and where it’s put at risk.
- Classifying that sensitive data.
- Monitoring and controlling the use (or misuse) of the data.
The foundational security technologies to accomplish these three goals are data classification and data loss prevention.
If you’re interested in learning more, we introduce Forrester’s Data-Centric Security Framework in our new eBook: The Definitive Guide to Data Loss Prevention – start reading now, no registration required.
Read more in our Definitive Guide to DLP Series
- Do you need DLP? Well, do you feel lucky?
- The Evolution of DLP: 4 Reasons Why DLP is Back in the Limelight
- Debunking the Three Myths of DLP
- Call it a Comeback: 7 Trends Driving the Resurgence of DLP
- All Trends Lead to Data-Centric Security
- What is Driving Your Data Protection Agenda? Determining the Right Approach to DLP
- Building a Value-Based Business Case for DLP
- Positioning DLP for Executive Buy-In
- 5 Criteria for Choosing the Right Managed Security Services Provider (MSSP)
- How to Evaluate DLP Solutions: 6 Steps to Follow and 10 Questions to Ask
- Getting Successful with DLP: Two Approaches for Quick DLP Wins
- Two Frameworks for DLP Success
1. The Future Of Data Security And Privacy: Growth And Competitive Differentiation, Forrester Research, Inc., July 10, 2015)
Whether you're just getting started with data loss prevention or looking to learn more, we put everything you need to know about DLP in one eBook.
Get tips and tricks from experts on how to select the right fit for your business.
