For the past few months we’ve featured a Definitive Guide to DLP blog series, covering everything from why you need DLP to how to determine the right approach to DLP and evaluate DLP solutions. Our previous post in the series outlined two approaches for quick DLP wins, so now it’s time to examine two frameworks for sustained DLP program success.
There are many sophisticated DLP frameworks out there, but many DLP projects fail or stall because the security and risk team tries to execute a complex framework from the start. We recommend two simple frameworks that provide an efficient path to protecting sensitive data, mitigating risk, and affecting change across your entire organization. As with our two “quick win” approaches from the previous post in this series, the framework you choose will depend on your DLP objective: gaining insights to mitigate data security risks or meeting the requirements of regulatory compliance mandates. Here’s a quick look at both options:
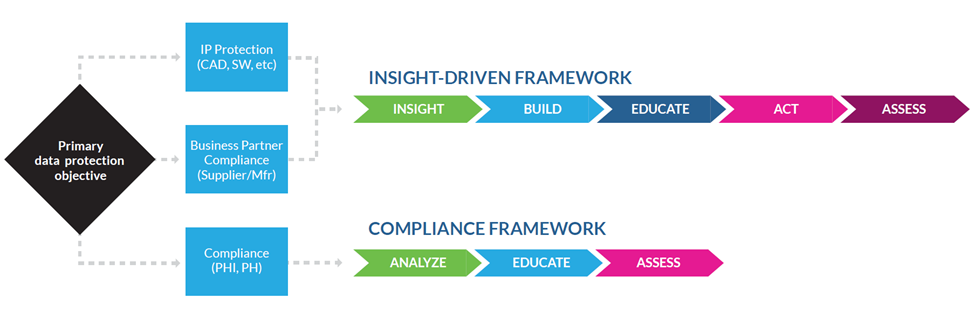
An Insight-Driven Framework for DLP Success
Driven by the need to protect intellectual property or meet business partner data protection requirements, this framework focuses on gaining insights about how sensitive data is actually used, then working with business leaders to build protection policies from the ground up. There are five stages to this framework:
- Insight: Deploy context-based endpoint DLP to get a good understanding of how sensitive data is actually being accessed, stored, and used within your organization.
- Record actions
- Build trends
- Normalize behavior
- Identify outliers
- Identify concerns & share with business leaders
- Build: Use DLP data visibility insights to create initial classifications and policies.
- Combine context with known sensitivities (e.g. source, group, file type) to develop baseline classifications & policies
- Develop user prompting rules
- Develop admin alert rules
- Educate: Employees are your biggest risk. Use DLP to prevent user actions that put your organization’s sensitive data at risk and educate users in real time on the appropriate handling of that data. If a user potentially violates a policy:
- Display prompts
- Request justification
- Educate users with positive reinforcement (gamification)
- Act: Where appropriate use DLP to block a user action, and encrypt data for the ultimate data protection.
- Display blocks
- Enforce policies
- Alert admin on violations
- Encrypt egress
- Assess: You can’t improve what you don’t measure. DLP provides a mechanism to continuously assess, iterate, and improve security policies and procedures.
- Conduct regular reviews of risk and policy enforcement
- Rebuild trending
- Tune classification and policies
A Compliance-Focused Framework for DLP Success
Done right, DLP can provide the foundation for a straightforward compliance framework that combines people, processes, and technology to prevent breaches. This framework has three stages:
- Analyze: Compliance and protection start with understanding your risks. Deploy Network DLP to identify, analyze, and control risks to regulated data such as PII, PHI, and PCI. Discover, monitor, and control PII/PHI/PCI that is being:
- Emailed out of your organization
- Transferred out of your organization in unencrypted FTP
- Copied to USB devices or burned to CDs or DVD
- Uploaded to the cloud
- Educate: Employees are your biggest risk. Use DLP to prevent user actions that put your organization’s data at risk and educate users in real time on the appropriate handling of regulated data. If a user potentially violates a policy:
- Display prompts
- Request justification
- Educate users with positive reinforcement (gamification)
- Assess: You can’t improve what you don’t measure. DLP provides a mechanism to continuously assess, iterate, and improve security policies and procedures.
- Regular review of risk and policy enforcement
- Rebuild trending
- Tune classification and policies
Policy: There’s No One Right Way
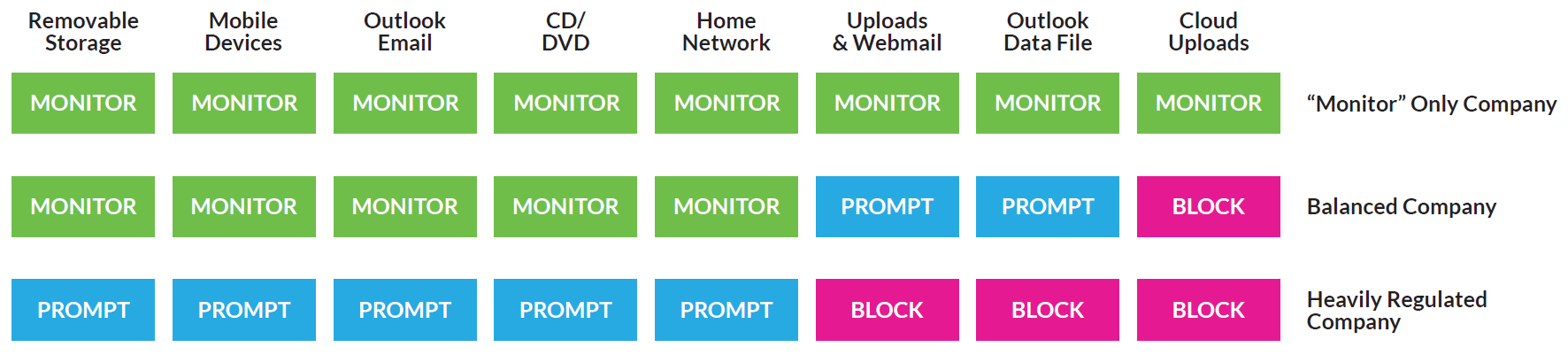
Following these frameworks will ensure that your DLP efforts stay on track for your objectives. Of course, no two DLP deployments are the same – you will still need to build your own policies that are tailored to your business and its unique data protection needs. We often see that DLP strategy is more closely aligned to corporate culture than anything else. A culture focused on employee workflow leads to a “monitor only” deployment, while on the other end of the spectrum a heavily regulated company may implement strict prompting and blocking rules. Consider your company culture and determine what policies would work best. Here are some examples:
We hope our Definitive Guide to DLP series has offered some helpful advice for your own DLP efforts. For more data loss prevention tips, read our Definitive Guide to DLP eBook:

Learn more about DLP:
- Do you need DLP? Well, do you feel lucky?
- The Evolution of DLP: 4 Reasons Why DLP is Back in the Limelight
- Debunking the Three Myths of DLP
- Call it a Comeback: 7 Trends Driving the Resurgence of DLP
- All Trends Lead to Data-Centric Security
- What is Driving Your Data Protection Agenda? Determining the Right Approach to DLP
- Building a Value-Based Business Case for DLP
- Positioning DLP for Executive Buy-In
- 5 Criteria for Choosing the Right Managed Security Services Provider (MSSP)
- How to Evaluate DLP Solutions: 6 Steps to Follow and 10 Questions to Ask
- Getting Successful with DLP: Two Approaches for Quick DLP Wins
Want to see Digital Guardian in action?
Learn how we can help your organization meet compliance, protect valuable IP and help reduce data loss.

