Securing FTP Usage
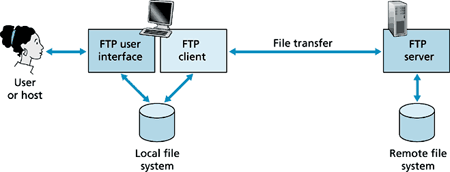
File Transfer Protocol (FTP) is a standard network protocol used to transfer files between computers over the Internet. FTP is built on client-server architecture and was developed by Abhay Bhushan in 1971. The protocol is still commonly used today, but FTP security is a major concern that can limit its usage when not addressed.
Security Challenges of FTP
FTP was not built to be secure. It is generally considered to be an insecure protocol because it relies on clear-text usernames and passwords for authentication and does not use encryption. Data sent via FTP is vulnerable to sniffing, spoofing, and brute force attacks, among other basic attack methods.
There are several common approaches to addressing these challenges and securing FTP usage. FTPS is an extension of FTP that can encrypt connections at the client’s request. Transport Layer Security (TLS), Secure Socket Layer (SSL), and SSH File Transfer Protocol (also known as Secure File Transfer Protocol or SFTP) are often used as more secure alternatives to FTP because they use encrypted connections.
Network Data Loss Prevention Improves FTP Security
Network data loss prevention solutions are often used to secure data sent over FTP sessions. Network DLP solutions are able to inspect and control FTP traffic, blocking or allowing transfers based on policies governing what users can take what actions with data. NDLP solutions can also encrypt data sent via FTP to ensure it is only readable by authorized parties.
Network data loss prevention solutions also are crucial for FTP security in cases when employees may inadvertently share sensitive data and confidential files using FTP. By prompting users, encrypting files, or blocking unauthorized FTP transfers altogether, network DLP tools ensure that sensitive data is not being put at risk of interception or exfiltration.
While FTP has inherent data security risks, the use of alternative secure protocols and data protection solutions such as network DLP can enable secure FTP usage.