A Definition of Advanced Malware
Advanced malware, sometimes referred to as advanced persistent threats (APT), are malware strains engineered with advanced capabilities for infection, communication and control, movement, or data exfiltration/payload execution. Advanced malware is often built for stealth or persistence and is capable of avoiding detection by traditional antivirus solutions. Recent years have seen a rise in attacks involving advanced malware, putting businesses at risk due to the malware’s sophisticated attack capabilities and the rate at which it evolves to stay ahead of detection.
How Advanced Malware Works
Advanced malware attacks typically follow a common attack sequence:
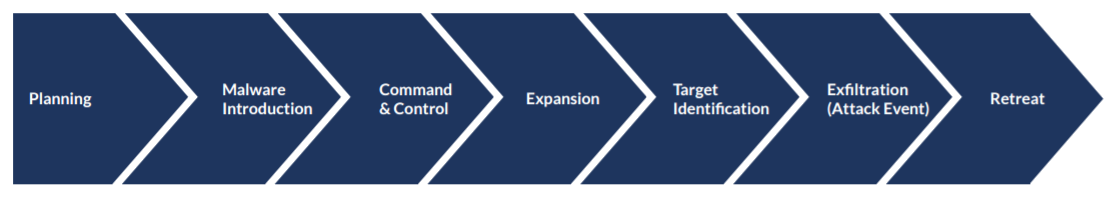
Planning:
This stage involves selecting a target and researching the target’s infrastructure to determine how the malware will be introduced, the communication methods used while the attack is in progress, and how/where the data will be extracted. In advanced malware attacks, this stage typically includes the planning of targeted social engineering attacks (such as spear phishing) for initial malware introduction.
Malware introduction:
In this stage, malware is delivered to its target(s) for initial infection. Malware is commonly delivered via social engineering attacks or via drive-by attacks online.
Command & control:
Advanced malware needs to communicate with the attackers to send discovered information and receive additional instructions. It will send user, network, and machine information to the attackers and receive new instructions on what identities or machines to infect next, how to identify the targets, and instructions for data exfiltration.
Expansion:
Attackers will explore the network and spread malware laterally seeking to infect machine(s) or system(s) that have access to the targeted data. Advanced malware often has robust self-propagation capabilities to identify and infect targets quickly.
Target identification:
Once the attacker has gained an initial foothold and explored the network, the target(s) will be identified for the final phase of malware propagation. In this stage the malware is spread to infect machines or systems that contain or have access to the targeted data.
Attack Event/Exfiltration:
The malware payload is executed; in an attack focused on data theft, this is the stage in which targeted data is compiled and offloaded to a location controlled by the attacker. Advanced malware employs techniques to hide exfiltration and other activity, such as encryption or compression of files using crypter and packer tools.
Retreat:
After an advanced malware attack is complete, the malware will often retreat and hide within a computer network or destroy itself, depending on the target organization and likelihood of discovery by security systems.
Examples of Common Types of Advanced Malware
Ransomware, an increasingly common threat, can be considered a form of advanced malware. Ransomware limits or sometimes completely blocks users from accessing their system through a number of methods such as locking the screen or restricting access to/encrypting files until a required sum is paid. The familiar names Cryptowall and Cryptoblocker are ransomware varieties, as well as the earlier CryptoLocker and the more recent Locky and TeslaCrypt. With victims paying up in order to regain access to vital systems and data, ransomware proves a lucrative tactic, only encouraging further proliferation of this form of advanced malware.
Best Practices for Defending Against Advanced Malware Attacks
As discussed above, the obfuscation techniques employed by advanced malware make many traditional security solutions ineffective at detecting or defending against advanced malware attacks. Organizations are turning to solutions that employ context- and behavior-based detection to identify and stop malware based on its activity rather than signatures. To improve detection of advanced malware attacks, organizations should monitor for increased threat activity or other anomalous behavior within systems. Your organization should monitor at the endpoint level for warning signs of an advanced malware attack, including network exploration, suspicious file transfers, and communication with suspicious command and control servers.
Advanced threat detection technologies provide sandboxing and monitoring to detect advanced malware attacks. Sandboxing enables you to execute and observe the suspect file in an isolated environment before it is permitted on the network, thereby potentially enabling detection before it has the opportunity to infiltrate your systems and cause damage.
Advanced malware prevention and protection efforts should focus on securing threat vectors – both infiltration and exfiltration points – to minimize the potential for infection and data egress. Applying controls at vectors such as email, internet connections, file transfer, and USB provides defense against advanced malware infections for early stage attacks as well as data exfiltration in the event of successful advanced malware infection that is attempting to carry out the final stages of its attack. All sensitive data assets should be encrypted with all keys stored securely as a last line of defense as well. This will help to ensure that damages stay at a minimum even if the network is infiltrated and the event goes undetected.
Finally, with social engineering attacks on the rise, it’s also critical to provide comprehensive and ongoing cybersecurity education to employees. Phishing attacks are a favorite delivery method for advanced malware attacks, and as a result it is important that employees are familiar with these tactics so that they can avoid being infected with malware if they are targeted in an attack.