Microsoft and Digital Guardian customers can use Microsoft’s Information Protection to extend their data protection policy to automatically label and protect files. Now there's an easier way to educate and enforce proper labeling and handling of data across all of your users.
Lots of customers I speak with are either currently rolling out MIP labeling/classification or are starting to explore how to utilize it in their environments. Customers I’ve talked with share two main concerns:
1. How do I train my users to properly use this classification system?
2. How do I enforce usage and how do I ensure the system is being used correctly?
DG Integrated Functionality
With the recent release of Digital Guardian Windows Agent version 7.7, we have introduced an integration with the MIP SDK that allows the DG Agent to:
1. Read MIP labels of files (both unprotected and protected labels)
2. Inspect the contents of both unprotected and protected MIP files
- “Unprotected” files have always been inspectable as their contents are clear text.
- “Protected” files are encrypted. The DG Agent can now decrypt and inspect these files.
3. Detect when a user changes the MIP label of a file
The User Problem
The labeling of data by the authors/users of that data is a valid approach to identifying what is sensitive data. The problem with any user-based labeling system resides in the users themselves. In fact, any process that relies on user involvement will always have the potential for failure due to that involvement. Specific to MIP labeling, there are four user types prone to introduce failure to the process:
1. The Uninformed User – a user that is not aware that the data they are interacting with is sensitive data. It could be that they are focusing on the first three to four pages of a document, but further down on the seventh page there is sensitive data. This user may mark the document as “general” even though, unbeknownst to them, it does contain sensitive data.
2. The Knucklehead User – a user that is knowledgeable to the labeling system but just trying to get through their day. As this user creates data, they may accidentally (due to oversight or out of pure repetition) select an incorrect label for a file. It could be that they have a deadline to meet. It could be that they’re working past 5 p.m. on a Friday. It could be that they don’t typically deal with sensitive data so their default selection is a “general” label. It could be that “general” is the first item in the list and that just happens to be what they select so they can proceed with their day.
3. The “But, I’m not a bad person” User – a user that understands security protocols and is knowledgeable about the labeling system but feels that the rules are too restrictive and shouldn’t apply to them. Imagine a user that is working on a time sensitive project and they want to work on it during the evening/weekend. This user should take their laptop home with them, but that’s problematic as they have an appointment on the way home and don’t want to leave their laptop in the car. Wouldn’t it be easier to just send the file to their personal webmail, download it to their home computer, finish the document, and then send it back in? Or maybe just transfer it to a USB drive that they can put in their pocket? This user may intentionally set or downgrade the existing label of a document to “public” for the sole purpose of making it easier for them to access the file temporarily on a remote system.
4. The Malicious User – this is a user that is determined to take sensitive data from the environment. They may be accepting a job with a competitor. They may be the author of source code and feel that they have ownership of the algorithms they’ve created for the company. They may be selling user/account information to a third party.
How DG Helps Reinforce MIP Labeling Practices
Digital Guardian’s integration with MIP means that you now have a method to identify the behaviors of ALL users and a means to educate and enforce proper labeling and handling of data.
For all scenarios, the DG Agent can identify that the file contains sensitive data. The agent can do this either based on inspection of the full contents of the file, based on the context of the file (or the data added to the file), or a combination of content or context.
Additionally, the DG Agent can read the MIP label that has been assigned to the file.
Piecing these two data elements together, the DG Agent can now optionally enforce policies, such as:
- If the label is a lower sensitivity than the classification that DG has detected, then block egress operations with a prompt.
- If the label is a higher sensitivity than the classification that DG has detected, then warn on egress operations with a prompt.
- If the label is appropriate to the classification that DG has detected, then permit egress operations without a prompt.
The “prompt” piece is important. A prompt will allow the security team to continuously interact and educate users when they are performing risky operations. The prompt is fully customizable such that any/all labels, logos, formatting, sizing, text/content/messaging can be customized to your specific needs. Below is an example prompt:
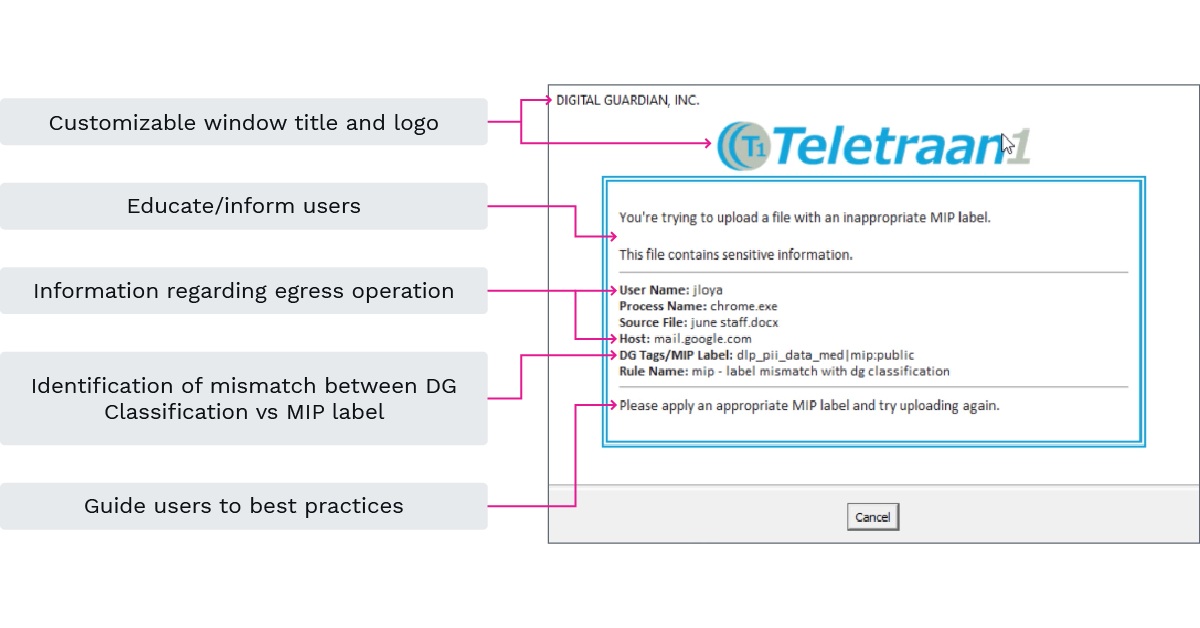
Forensics for MIP Labels
Educating and interacting with users is a large portion of the functionality that DG brings to the game. The other piece that DG brings is visibility into how MIP labels are being set/used in your environment. DG does this in two ways:
For actions (copy, move, rename, delete, upload, email, archive, etc.) involving files, DG will log the action along with the DG Classification as well as the MIP Label.
- For actions where the user is changing a MIP label, either upgrading or downgrading, DG will log the change in MIP label as a “File Classify” event.
- Having this visibility is important for understanding how MIP labeled files are being used and interacted with throughout your environment, but also in terms of identifying suspicious/malicious behaviors with your sensitive data. Is a user frequently mislabeling data? Did a user downgrade a MIP label prior to attempting an egress operation? DG can help answer these questions.
Below is an example of a user attempting to upload a file with an incorrect label, changing the label, then successfully uploading the file to an internal repository:
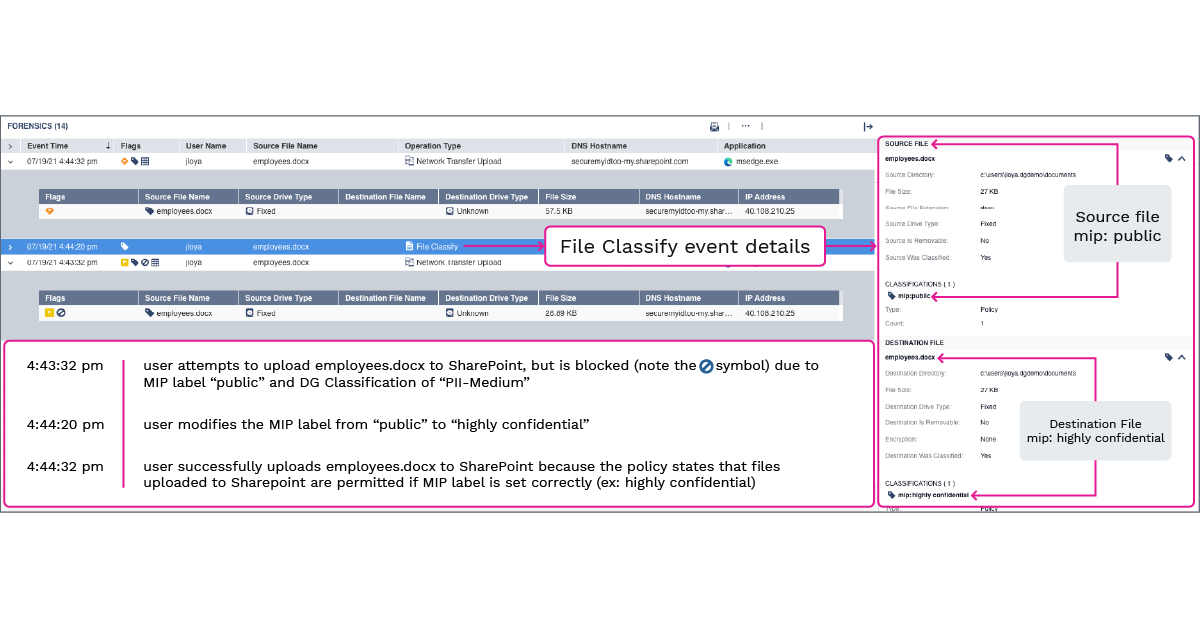
All operations are logged and available to an analyst investigating a user’s activities.
DG’s Agent integration with MIP labeling provides enterprises the ability to view, analyze, educate, control, and investigate users’ labeling practices. This yields a more effective labeling practice, an educated user base, and a reduction in misuse/abuse of the labeling system.
If you’re not a customer but looking to learn more about how Digital Guardian can help improve your MIP labeling practices, request a free demo today!
