Digital Guardian Deployment Options
Enterprise DLP needs enterprise class infrastructure. Add the option of dedicated cybersecurity experts to manage your program and you have world-class sensitive data protection. Learn more about how Digital Guardian can make your data protection efforts more effective whether you manage it or we manage it for you.
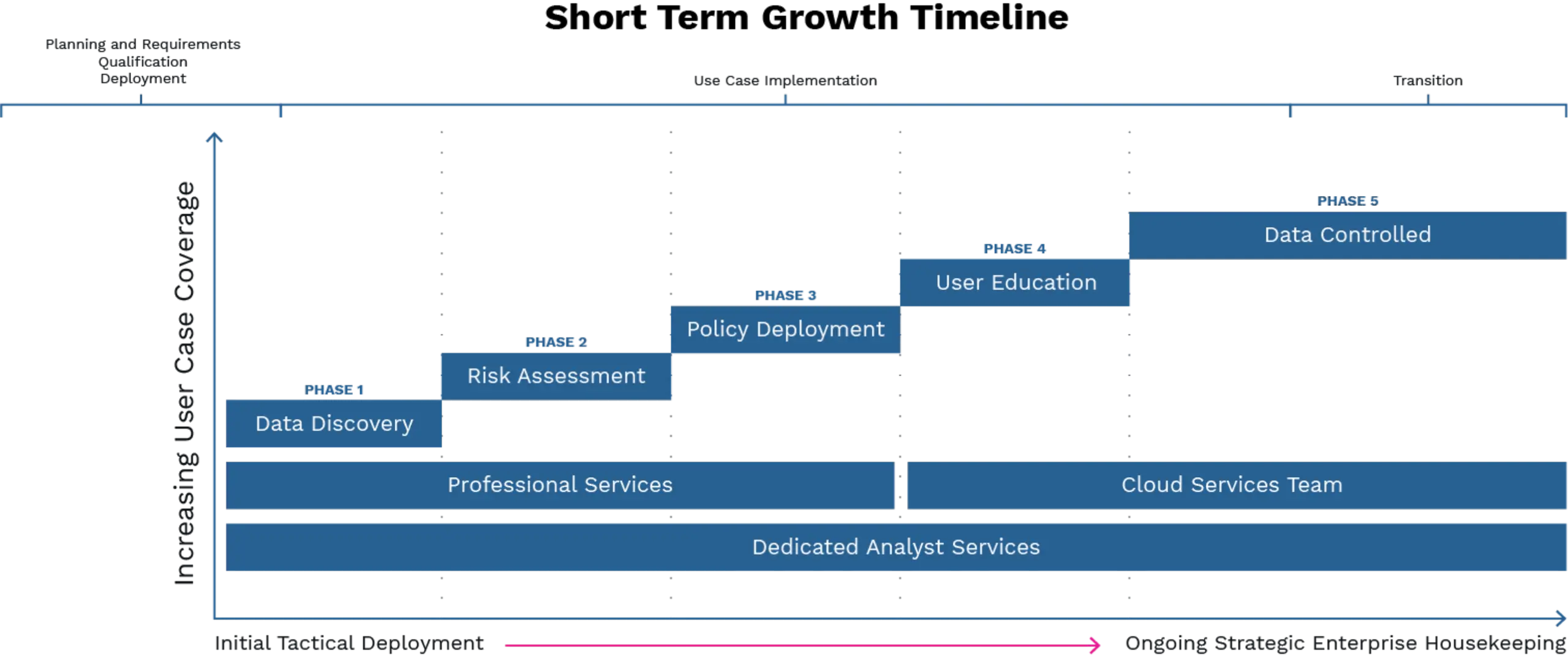
Roadmap to Data Protection - MSP
Image
PHASE 1
Data Discovery Goals
- Provides experienced Digital Guardian subject experts to help you pinpoint security and compliance goals.
- Documents the existence, scope, and severity of your data risks.
- Shows complete usage context from executive summaries to detailed forensics.
- Measures effectiveness of your current security policies and technology investments.
- Identifies how you can best take action on potential data threats.
Image
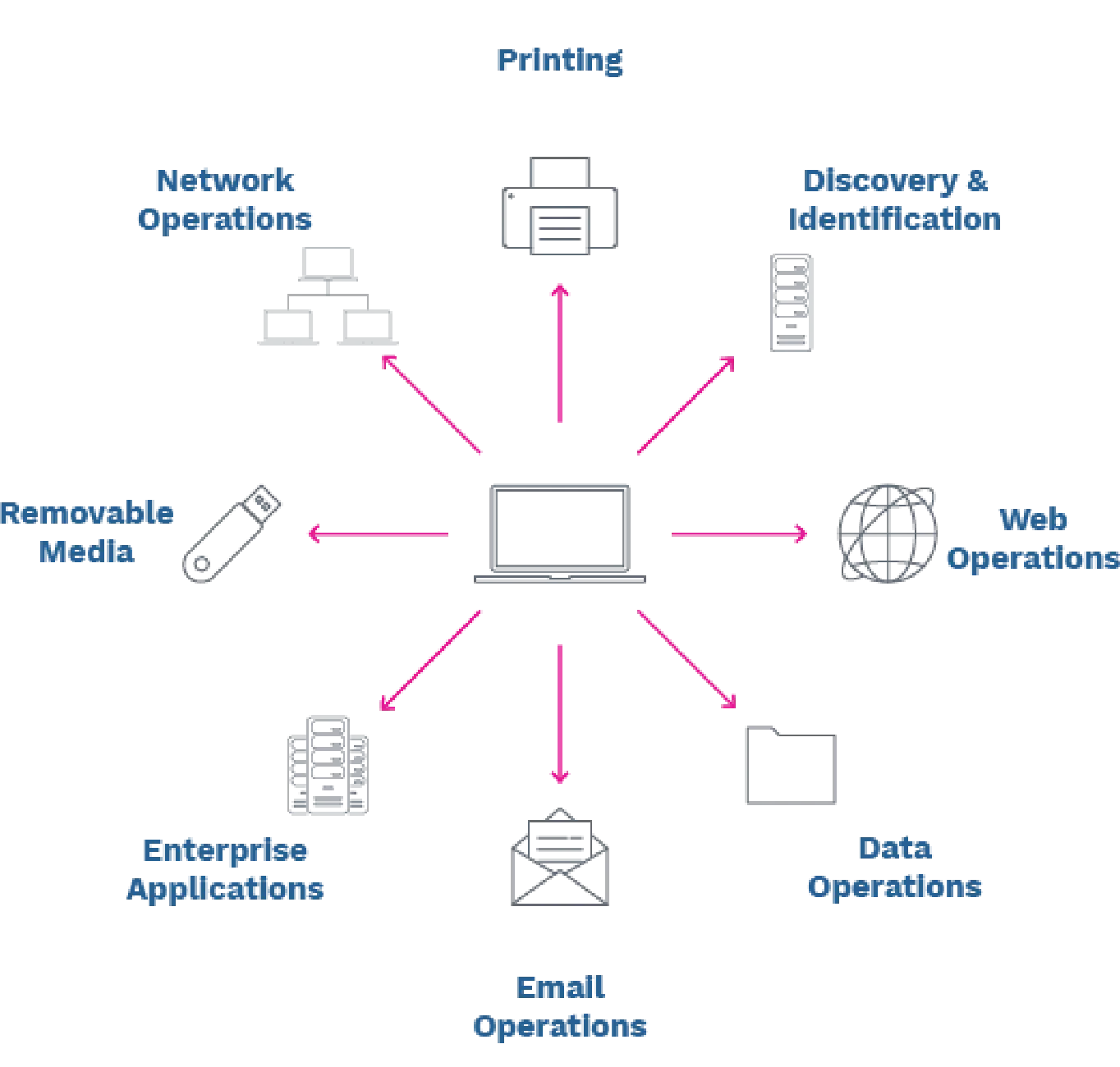
Data Discovery Analytics
Text
On-demand and regularly scheduled overviews of activity.
Send Mail | NTU | CD/DVD | Removable | Copy & Paste | Print | Custom
Image
PHASE 2
Risk Assessment Goals
Risk Assessment Methodology
Data Classification
Data and Entity Inventory
Current Control Review
Vulnerability Assessment
Data Sensitivity and Risk
Cost Benefit Analysis
PHASE 3
Policy Deployment
Image
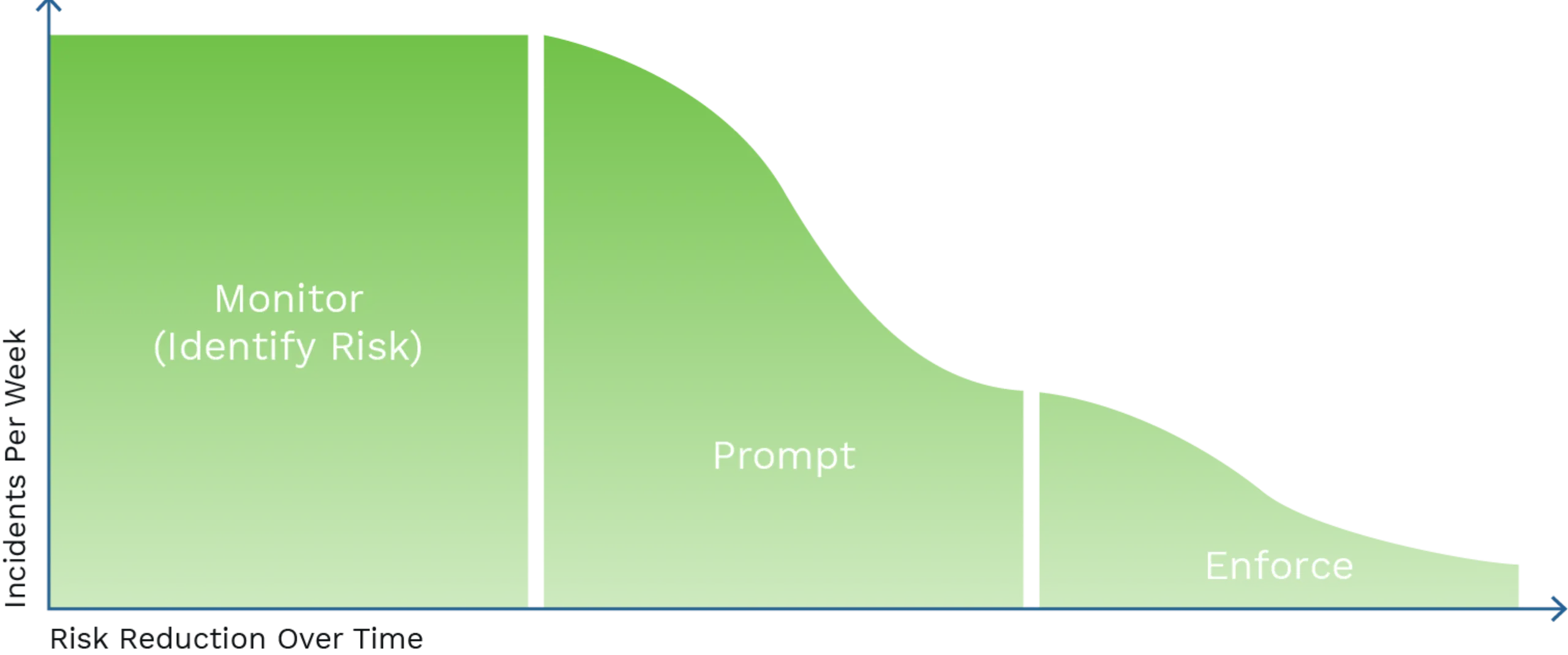
Image
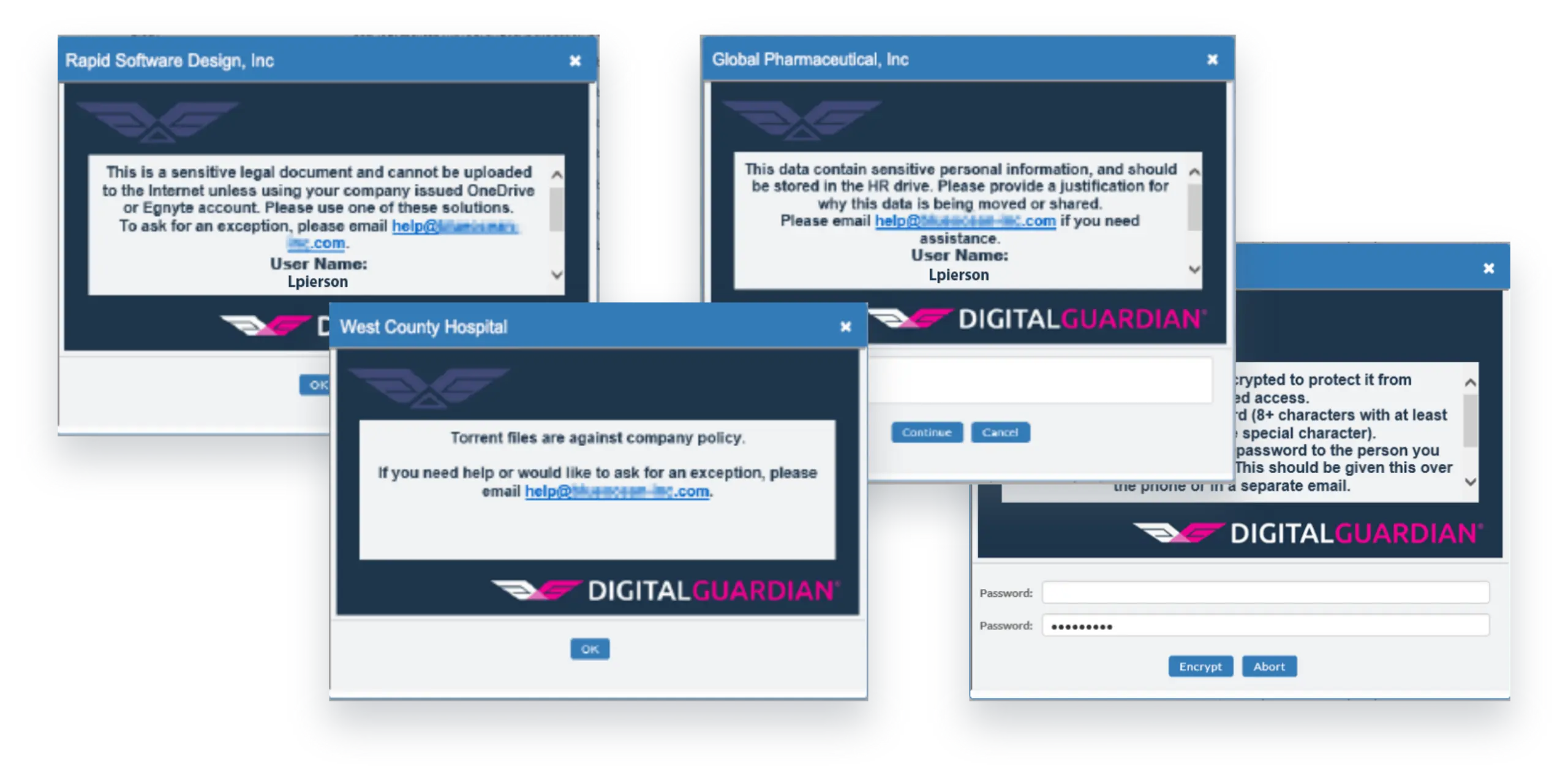
Policy Visibility
Text
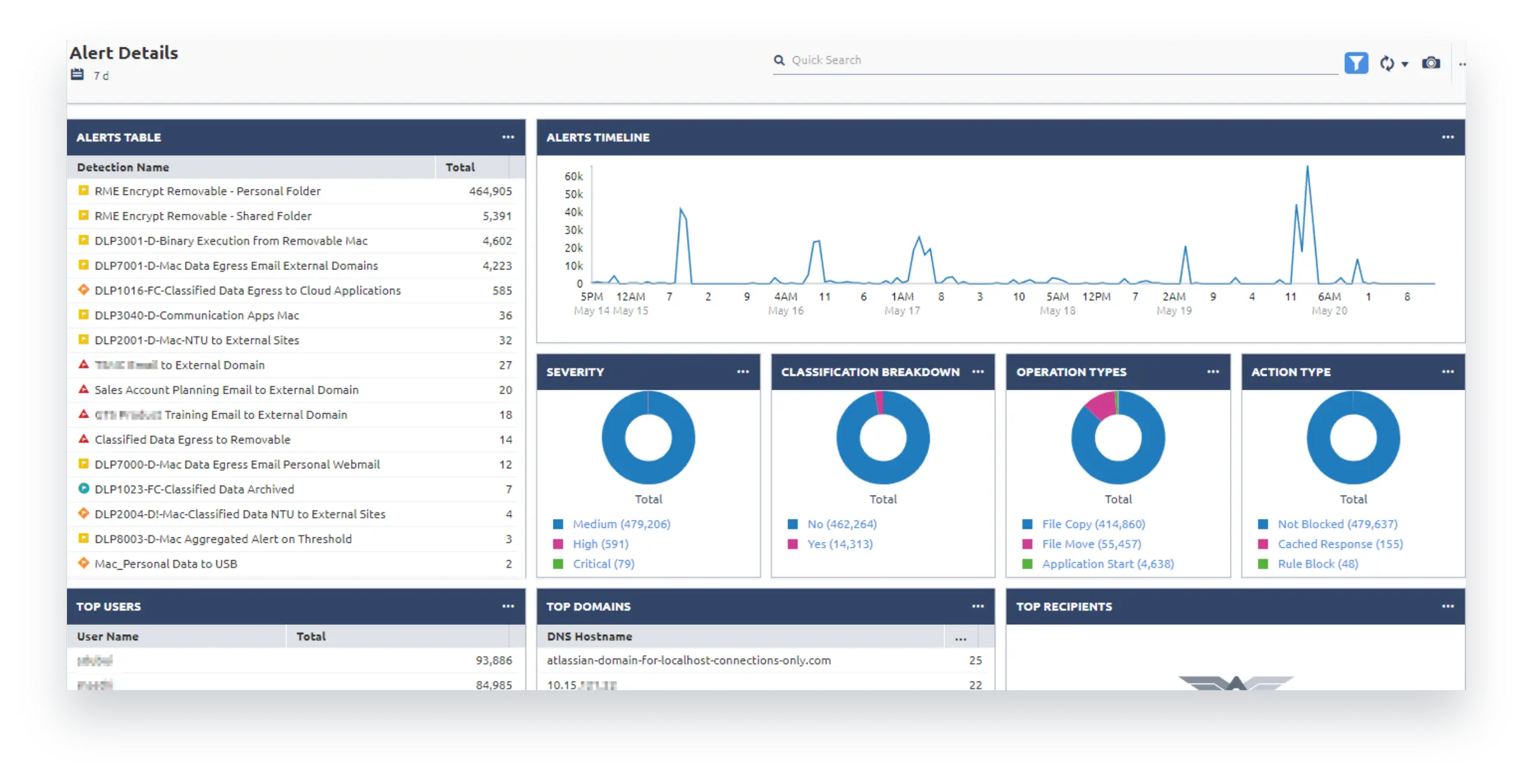
Incredible insight on day one
Image
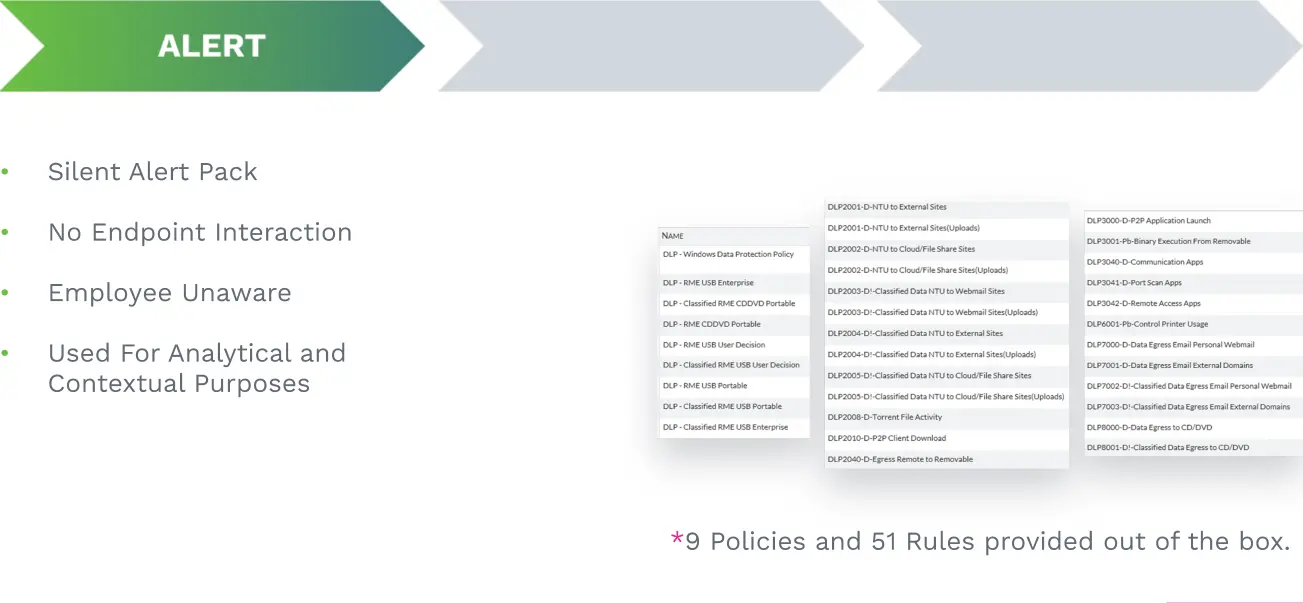
PHASE 4
User Education
Text
Image

Image

PHASE 5 - CONTINUOUS EFFORT
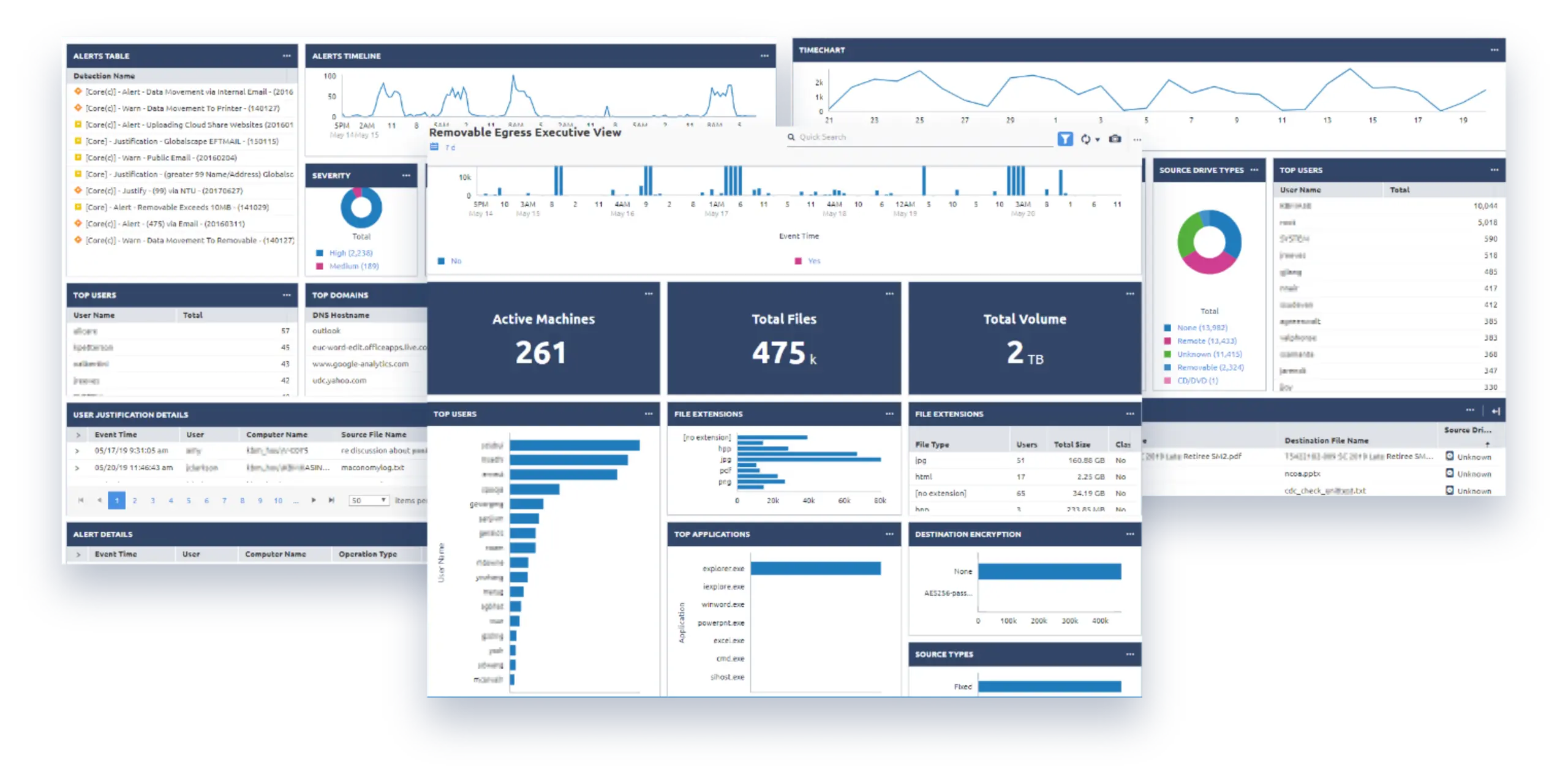
Controlling Data
Text
Image

Image