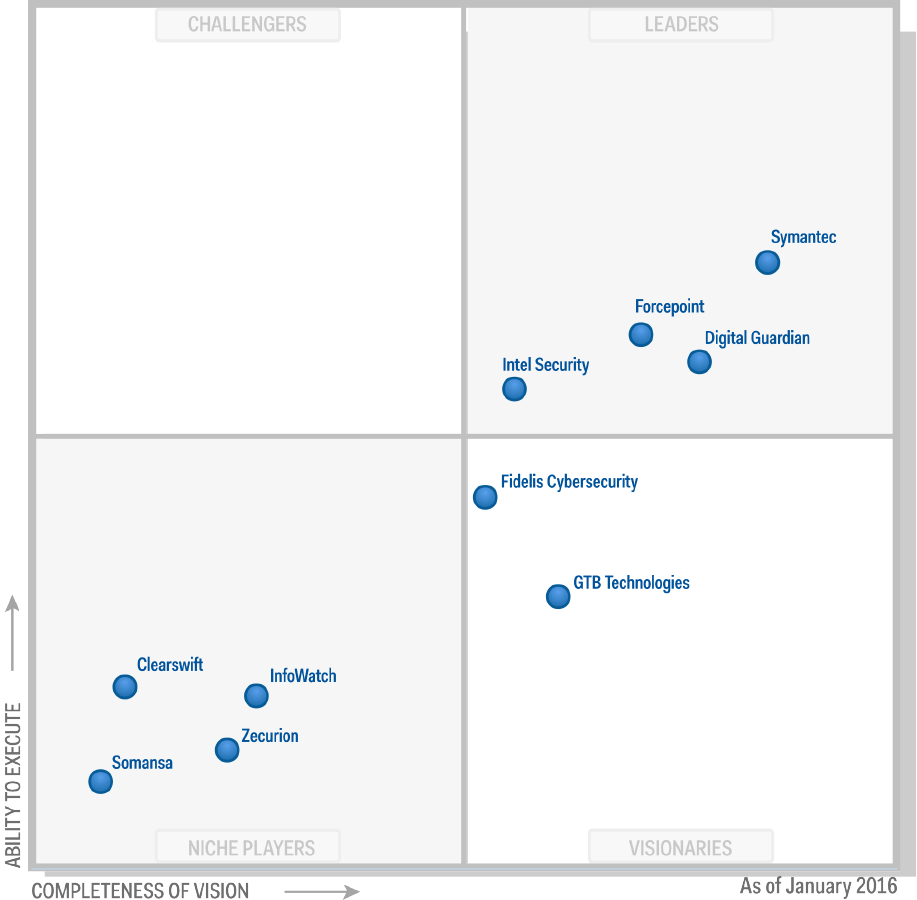
3 Key Takeaways from the 2016 Gartner Magic Quadrant for Enterprise Data Loss Prevention
Gartner’s newly released 2016 Magic Quadrant for Data Loss Prevention presents some interesting findings on the current trends impacting the data loss prevention market. Here are a few of our top takeaways from the report.
Podcast: The Ransomware Problem
Thomas Fischer and Paul Roberts discuss the ransomware problem that is currently impacting businesses around the globe.
Digital Guardian Data Protection for your OS X Environment (Mac DLP Video Demo)
How many Macs do you have in your company and your data protection program? Watch this video demo to learn about Digital Guardian Data Loss Prevention for Mac environments.
Tax Fraud Two-Step Starts with Phishing for W2s
A spate of spear phishing attacks aimed at harvesting employees’ W2s has direct links to tax ID fraud.
Of Bugs and Bounties
When vendors first began crediting security researchers for reporting vulnerabilities in their products, the reward typically was your name in 12-point Arial at the bottom of a security advisory*. Those days are long past, and the bug bounty game has changed so dramatically now that independent security researchers can make a very comfortable living by finding bugs in the right kinds of products.
6 security risks of enterprises using cloud storage and file sharing apps
The following are six of the top risks that must be addressed when using cloud storage and file sharing apps for business.
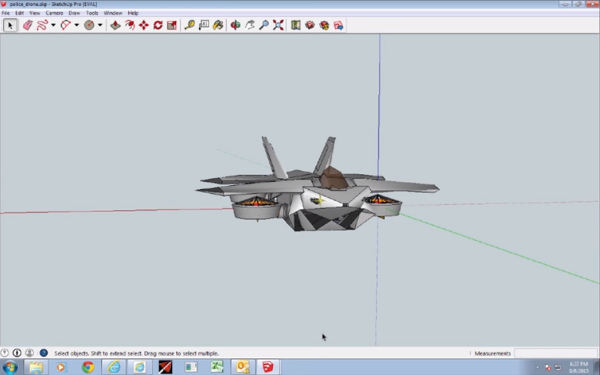
Digital Guardian Keeps your CAD in the Cradle (Video Demo)
Intellectual property takes serious work to create and requires a smart solution for protection. Watch this video demo to learn how Digital Guardian secures IP in a variety of forms.
What’s The Value of a Stolen Chest X-Ray? More Than You’d Think.
A panel on security in the healthcare field at the South by Southwest Festival reveals the diversity of threats to health data.
Making Data Public on Private Connections
Encrypted connections are becoming an industry standard for high-traffic websites, and for good reason.
The Gamification of Data Loss Prevention: Educating and Enabling Employees with DLP
Applying gamification concepts to your DLP policies can transform a traditional DLP deployment into a fun, educational and engaging employee experience.
Don't Fall Behind
Get the latest security insights
delivered to your inbox each week.