Govt Experienced Fewer Security Incidents in 2019 but Risk Remains High
| Contact Us | |
| Free Demo | |
| Chat | |
Findings from the latest FISMA report are out and while the number of total cybersecurity incidents in 2019 were down, the federal government continues to face challenges mitigating basic security vulnerabilities.
The U.S. government has to do a better job protecting what it calls high-value IT assets - systems that are integral to federal agencies - according to a new Federal Information Security Management Act (FISMA) report.
According to the Office of Management and Budget (OMB) - which submitted the annual report to Congress last week - these systems are particularly susceptible to basic security vulnerabilities. The number one risk issue for these assets is susceptibility to spear-phishing, followed by patch management, admin password reuse, insecure default configuration, and employing a weak password policy.
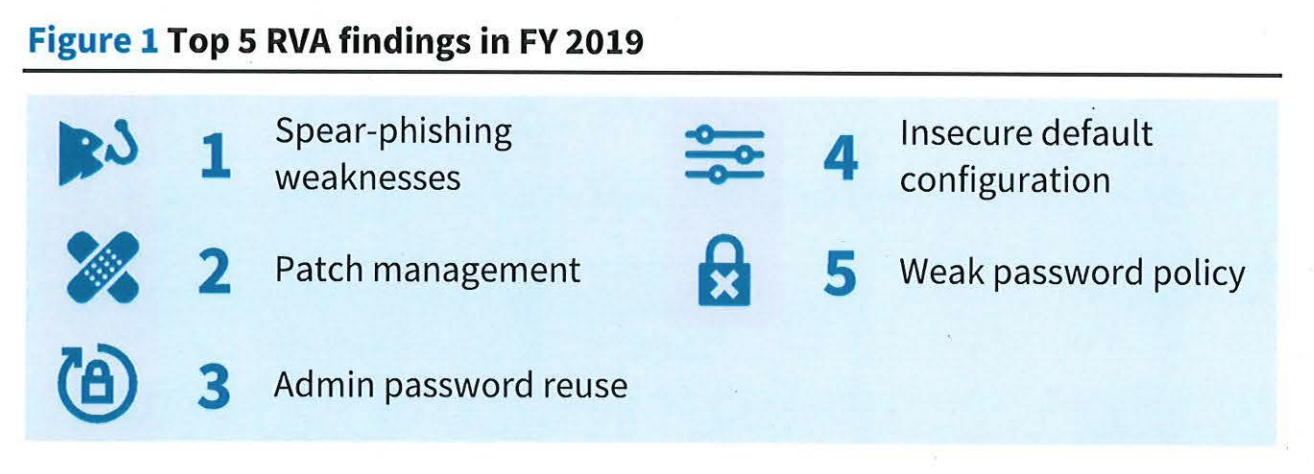
For the report, the OMB audited 71 high-value asset (HVA) assets, identifying 448 findings and 244 risk and vulnerability findings. Risk and vulnerability assessements traditionaly include network mapping and vulnerability scanning, phishing engagements, web application or database evaluations, and a full penetration test.
“These assessments revealed that the Federal Government continues to face challenges mitigating basic security vulnerabilities,” the report reads.
All of this isn’t to downplay some of the successes the government have achieved securing systems. According to the report, improvements have been made when it comes to securing the government's systems. There was an 8 percent drop in reported cybersecurity incidents in 2019, 28,581 compared to 31,107 in 2018.
It’s the second year in a row that the report has shown a decrease in cybersecurity incidents. Last year’s report showed a 12 percent decrease from 2017’s figures. For those curious, the last time there was an increase was in 2017, when agencies experienced 35,277 cybersecurity incidents, a 14% increase over the 30,899 incidents that agencies reported in 2016.
The report makes a point to say that while there's been a decline in incidents, something it attributes the continued maturation of agencies' information security programs, it shouldn't indicate that there's been a reduction in the cybersecurity threat posed to the Federal Government.
When looking at all of the incidents, one of the biggest was improper usage; there were 12,507 incidents, government-wide. As the name suggests, it accounts for any incident that results from the violation of an organization's acceptable use policy. The report links this statistic to the fact that while agencies have processes and capabilities in place to detect when policies are violated, they lack the necessary mechanisms to enforce or prevent them from happening.
The report breaks down each department and the incidents identified at each by attack vector. It also gives a rating as to how each has fared identifying, protecting, detecting, responding, and recovering from incidents.
Some departments fare better than others. Agencies like the Department of Energy, which faces many cyber threats, is considered an “At Risk” agency, according to the report. The Environmental Protection Agency is in the same boat, although less because it's a target and more because it doesn't receive the necessary funding to aid its cybersecurity strategy, according to the report. Smaller, more fringe agencies, like the Federal Communications Commission, the Armed Forces Retirement Home, Commission of Fine Arts, and the Marine Mammal Commission, are also labeled at risk. It's worth noting that the some of those agencies don't collect or store classified information, something which effectively reduces their risk.
72 agencies in total received a rating of "Managing Risk." 25 agencies are considered "At Risk," meaning they have policies, processes, and tools in place to mitigate risk but gaps remain.
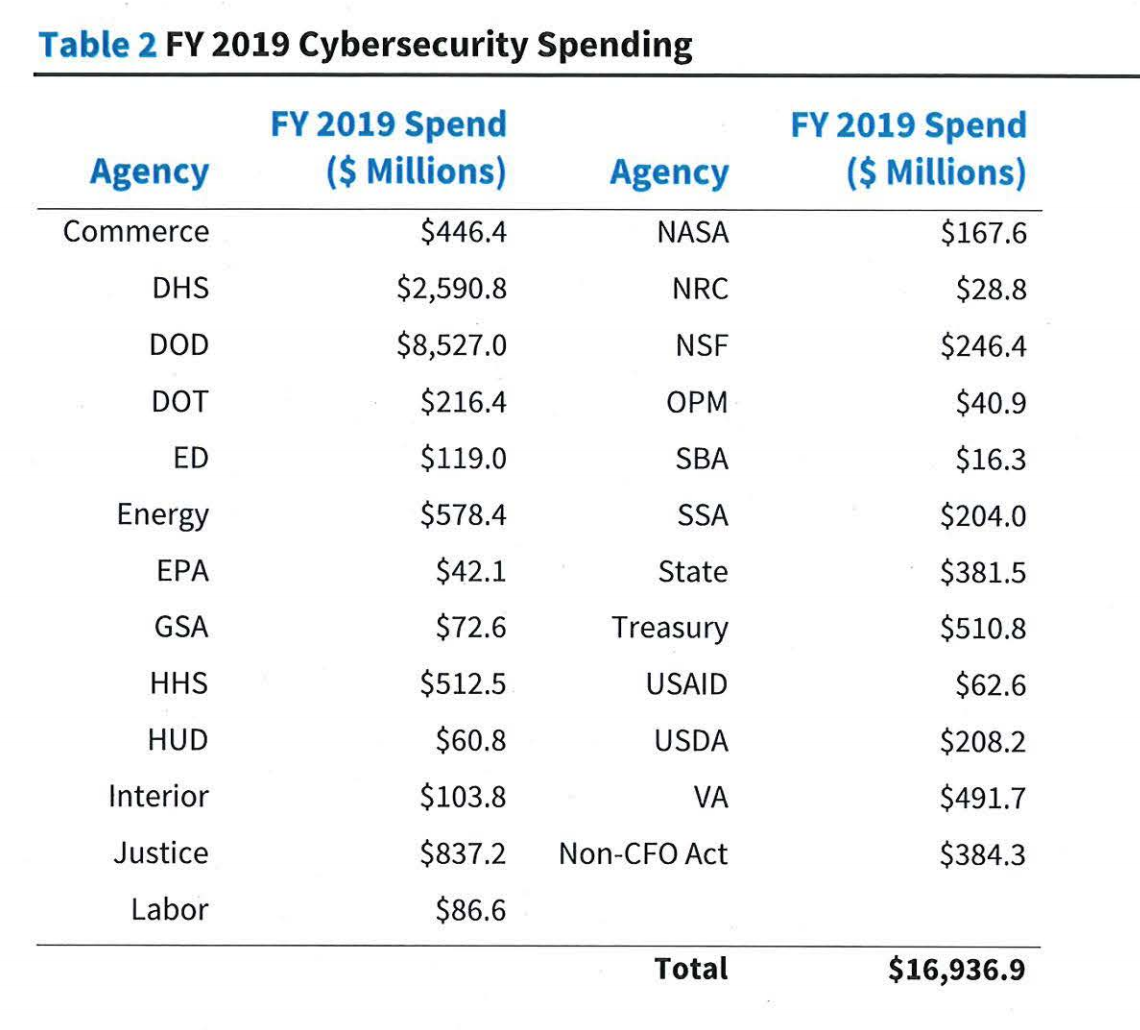
As usual, the report recaps the amount of money spent by each federal entity on cybersecurity. Collectively the agencies spent almost $17 billion on cybersecurity in 2019. Most of that can be attributed to the Department of Homeland Security, which spent about $2.6 billion and the Defense Department, which spent about $8.5 billion. The Small Business Adminstration spent the least, $16.3 million,
The report also digs into three major cybersecurity incidents experienced by federal agencies in the 2019 calendar year:
• An incident involving Federal Emergency Management Agency’s (FEMA) National Emergency Management Information System Information Assurance (NEMIS-IA) sending sensitive personally identifiable information belonging to disaster victims (2.5 million hurricane survivors) to a contractor after it was no longer required.
• An incident reported by the DHS involving the sharing of PII of 895,000 disaster survivors by FEMA with a third party volunteer organization.
• A ransomware attack reported by DHS involving a contractor that makes license plate readers used by U.S. Customs and Border Protection at check points across the U.S. The contractor took license plate images and facial images of the profile and front of travelers inside of a vehicle.
Creation and release of the annual report is mandated under 2002's Federal Information Security Modernization Act, part of the larger E-Government Act of 2002, introduced to improve the management of electronic government services and processes.
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.