What is HIPAA Compliance?
| Contact Us | |
| Free Demo | |
| Chat | |
Learn about the Health Insurance Portability and Accountability Act (HIPAA) and the requirements for HIPAA compliance in Data Protection 101, our series on the fundamentals of information security.
A Definition of HIPAA Compliance
The Health Insurance Portability and Accountability Act (HIPAA) sets the standard for sensitive patient data protection. Companies that deal with protected health information (PHI) must have physical, network, and process security measures in place and follow them to ensure HIPAA Compliance. Covered entities (anyone providing treatment, payment, and operations in healthcare) and business associates (anyone who has access to patient information and provides support in treatment, payment, or operations) must meet HIPAA Compliance. Other entities, such as subcontractors and any other related business associates must also be in compliance.
The HIPAA Privacy and HIPAA Security Rules
According to the U.S. Department of Health and Human Services (HHS), the HIPAA Privacy Rule, or Standards for Privacy of Individually Identifiable Health Information, establishes national standards for the protection of certain health information. Additionally, the Security Rule establishes a national set of security standards for protecting specific health information that is held or transferred in electronic form.
The Security Rule operationalizes the Privacy Rule’s protections by addressing the technical and nontechnical safeguards that covered entities must put in place to secure individuals’ electronic PHI (e-PHI). Within HHS, the Office for Civil Rights (OCR) is responsible for enforcing the Privacy and Security Rules with voluntary compliance activities and civil money penalties.
The Need for HIPAA Compliance
HHS points out that as health care providers and other entities dealing with PHI move to computerized operations, including computerized physician order entry (CPOE) systems, electronic health records (EHR), and radiology, pharmacy, and laboratory systems, HIPAA compliance is more important than ever. Similarly, health plans provide access to claims as well as care management and self-service applications. While all of these electronic methods provide increased efficiency and mobility, they also drastically increase the security risks facing healthcare data.
The Security Rule is in place to protect the privacy of individuals’ health information, while at the same time allowing covered entities to adopt new technologies to improve the quality and efficiency of patient care. The Security Rule, by design, is flexible enough to allow a covered entity to implement policies, procedures, and technologies that are suited to the entity’s size, organizational structure, and risks to patients’ and consumers’ e-PHI.
Physical and Technical Safeguards, Policies, and HIPAA Compliance
The HHS requires physical and technical safeguards for organizations hosting sensitive patient data. These physical safeguards include…
- Limited facility access and control with authorized access in place
- Policies about use and access to workstations and electronic media
- Restrictions for transferring, removing, disposing, and re-using electronic media and ePHI
Along the same lines, the technical safeguards of HIPAA require access control allowing only for authorized personnel to access ePHI. Access control includes…
- Using unique user IDS, emergency access procedures, automatic log off, and encryption and decryption
- Audit reports or tracking logs that record activity on hardware and software
Other technical policies for HIPAA compliance need to cover integrity controls, or measures put in place to confirm that ePHI is not altered or destroyed. IT disaster recovery and offsite backup are key components that ensure that electronic media errors and failures are quickly remedied so that patient health information is recovered accurately and intact. One final technical safeguard is network, or transmission security that ensures HIPAA compliant hosts protect against unauthorized access to ePHI. This safeguard addresses all methods of data transmission, including email, internet, or private networks, such as a private cloud.
To help ensure HIPAA compliance, the U.S. government passed a supplemental act, The Health Information Technology for Economic and Clinical Health (HITECH) Act, which raises penalties for health organizations that violate HIPAA Privacy and Security Rules. The HITECH Act was put into place due to the development of health technology and the increased use, storage, and transmission of electronic health information.
Data Protection for Healthcare Organizations and Meeting HIPAA Compliance
The need for data security has grown with the increase in the use and sharing of electronic patient data. Today, high-quality care requires healthcare organizations to meet this accelerated demand for data while complying with HIPAA regulations and protecting PHI. Having a data protection strategy in place allows healthcare organizations to:
- Ensure the security and availability of PHI to maintain the trust of practitioners and patients
- Meet HIPAA and HITECH regulations for access, audit, integrity controls, data transmission, and device security
- Maintain greater visibility and control of sensitive data throughout the organization
The best data protection solutions recognize and protect patient data in all forms, including structured and unstructured data, emails, documents, and scans, while allowing healthcare providers to share data securely to ensure the best possible patient care. Patients entrust their data to healthcare organizations, and it is the duty of these organizations to take care of their protected health information. To learn more about best practices for healthcare data protection, read our guide to healthcare cybersecurity.
HIPAA Compliance with Digital Guardian
See how Digital Guardian for HIPAA compliance locates and protect sensitive patient data throughout the integrated delivery network.
HIPAA Compliance in the COVID-19 Landscape
It’s an understatement to say the world is different due to the pandemic. Healthcare is, almost undoubtedly, set to change the most over the next several years. Maintaining privacy compliance is also more difficult. Factors increasing the risk of private health information include:
- Telehealth Visits: The number of healthcare provider visits conducted over the web has skyrocketed. Patients who typically make short trips to the clinic or office decide to stay home and see their physician virtually, unless an in-person visit is absolutely necessary. Data protection over the Internet is difficult if proper precautions are overlooked.
- Increased Patient Count (post-lockdown): Now that many states allow most procedures and visits to occur, there has been an onslaught of appointments. When paired with physical distancing guidelines, offices are often short on staff when schedules are maxed out. This situation creates an opportunity for HIPAA compliance mistakes.
- Multiple Care Providers: Patients often see multiple doctors. However, increased testing and varied result times make things cloudy. Primary care physicians receiving updates from multiple testing labs, patients, or hospitals means data is moving in and out at a faster pace (if dealing with potential virus cases).
Stay Up-to-Date to Avoid Issues
The Department of Health and Human Services (HHS) has proactively updated those who fall under HIPAA coverage (aka, “covered entities”). Here’s what the HHS has to say about the increase in telehealth options:
“A covered health care provider that wants to use audio or video communication technology to provide telehealth to patients during the COVID-19 nationwide public health emergency can use any non-public facing remote communication product that is available to communicate with patients. OCR is exercising its enforcement discretion to not impose penalties for noncompliance with the HIPAA Rules in connection with the good faith provision of telehealth using such non-public facing audio or video communication products during the COVID-19 nationwide public health emergency. This exercise of discretion applies to telehealth provided for any reason, regardless of whether the telehealth service is related to the diagnosis and treatment of health conditions related to COVID-19.” (Source: HHS)
Make sure to follow these updates from those who monitor and enforce HIPAA compliance in order to ensure the safest environment. Communications are likely to provide guidance on the most prominent issues caused by the pandemic, such as increased appointments, data threats, and mitigation techniques.
The Most Recent HIPAA Updates
A number of changes and updates to HIPAA are being considered and may become either guidance or parts of the law within the coming months.
Updated Penalties for HIPAA Violations
Potential fines and penalties were updated in 2019. Details outlined in the document included a tiered structure for violations with corresponding “caps” now starting from $25,000 for Tier 1.
Better Enforcement and Accountability of Violations
2019 was a big year for enforcement. According to HIPAA Journal, the average financial penalty was more than $1.2 million. Enforcement was increased in 2018 and obviously wasn’t slowed this past year. The Health & Human Services Office for Civil Rights (HHS OCR) did tighten enforcement efforts in 2018, obviously continuing through last year. However, due to the current world situation, enforcement may take a backseat for most of 2020.
Potential Permanent Audit Program
The HHS has long spoken of a permanent audit program. When the organization launched “Phase 2” of the HIPAA audit program, it mentioned a permanent audit structure in the future. While, at the time of this writing, the audit program has not been changed to a permanent structure.
Additional Guidance or Regulations Regarding Opioids
The status of opioid addiction and overuse in America has been prominently labeled as a “crisis” and an “epidemic”. New legislation has been promised and debated to battle the issues surrounding the controversial drug. However, it may cause further changes to HIPAA. These changes could range from further guidance or potential compliance issues.
Frequently Asked Questions
What is HIPAA compliance?
The Health Insurance Portability and Accountability Act (HIPAA) defines the security and privacy regulations required to protect sensitive patient health information. Specifically, the Act addresses requirements for handling protected health information (PHI) and electronic protected health information (ePHI). All companies operating in the healthcare industry in the U.S. must comply with HIPAA regulations. This includes business partners such as cloud service providers who process ePHI for healthcare companies.
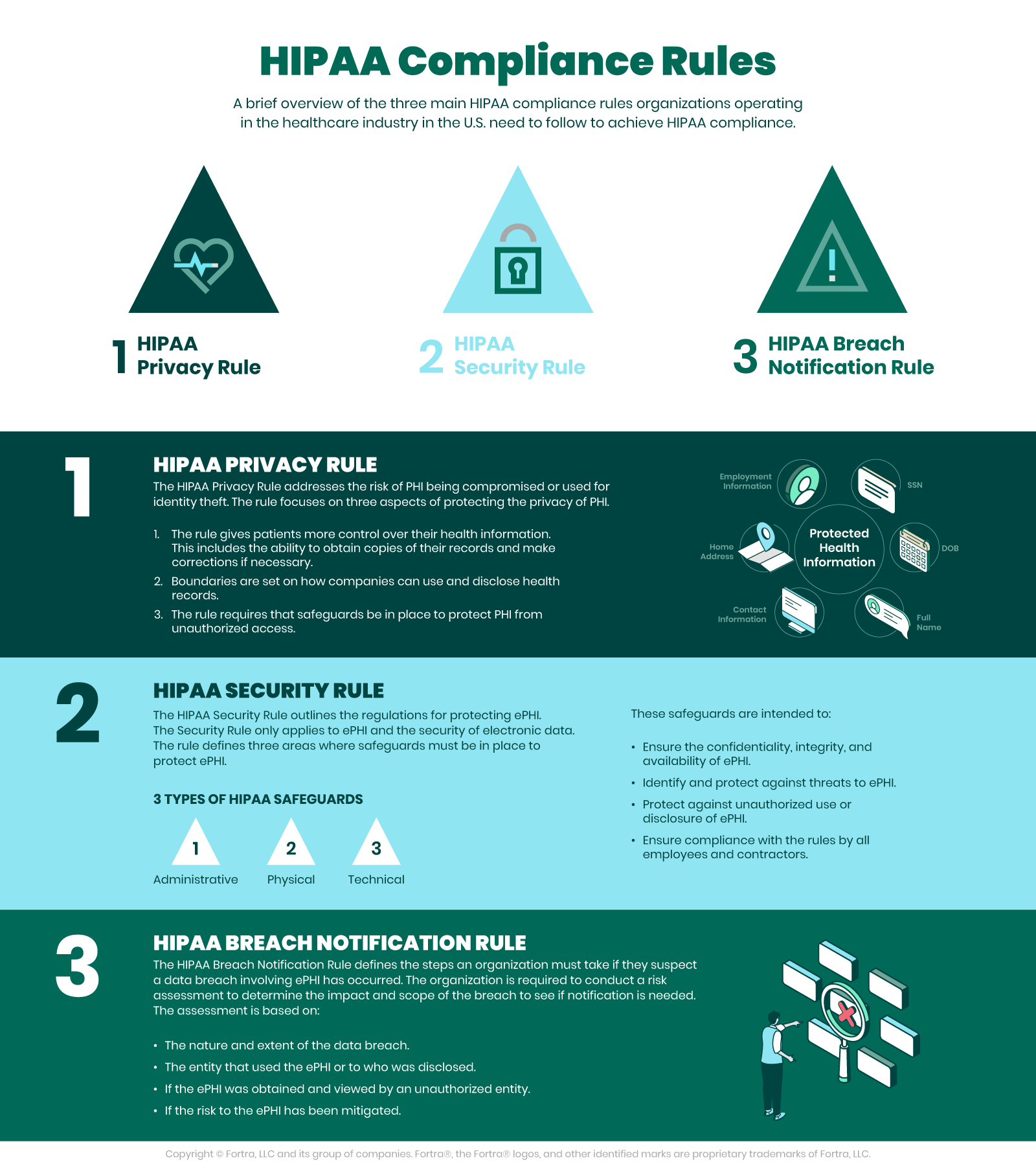
What are HIPAA compliance rules?
There are three main HIPAA compliance rules.
HIPAA Privacy Rule
The HIPAA Privacy Rule addresses the risk of PHI being compromised or used for identity theft. The rule focuses on three aspects of protecting the privacy of PHI.
- The rule gives patients more control over their health information. This includes the ability to obtain copies of their records and make corrections if necessary.
- Boundaries are set on how companies can use and disclose health records.
- The rule requires that safeguards be in place to protect PHI from unauthorized access.
HIPAA Security Rule
The HIPAA Security Rule outlines the regulations for protecting ePHI. The Security Rule only applies to ePHI and the security of electronic data. The rule defines three areas where safeguards must be in place to protect ePHI. These administrative, physical, and technical safeguards are intended to:
- Ensure the confidentiality, integrity, and availability of ePHI.
- Identify and protect against threats to ePHI.
- Protect against unauthorized use or disclosure of ePHI.
- Ensure compliance with the rules by all employees and contractors.
HIPAA Breach Notification Rule
The HIPAA Breach Notification Rule defines the steps an organization must take if they suspect a data breach involving ePHI has occurred. The organization is required to conduct a risk assessment to determine the impact and scope of the breach to see if notification is needed. The assessment is based on:
- The nature and extent of the data breach.
- The entity that used the ePHI or to who was disclosed.
- If the ePHI was obtained and viewed by an unauthorized entity.
- If the risk to the ePHI has been mitigated.
What are the most common HIPAA violations?
The following are some of the most common HIPAA violations
- Lack of employee training on HIPAA compliance.
- Database breaches affecting ePHI.
- Sharing PHI between coworkers.
- Loss of a laptop or mobile device containing unencrypted ePHI.
- Improperly disposing of ePHI in ways that make it accessible to unauthorized users.
What does HIPAA not cover?
HIPAA only covers PHI and ePHI in the United States. Therefore, other types of data are not covered by HIPAA, such as login credentials to social media sites, records an employer keeps about employees, or student health records maintained by a school. Some exceptions apply, such as if a university provides medical care to students. In this case, the university would be subject to HIPAA.
What are HIPAA compliance requirements?
Organizations operating in the healthcare industry in the U.S. need to follow the HIPAA Security, Privacy, and Breach Notification Rules to achieve compliance. This includes implementing all of the required administrative, physical, and technical safeguards to protect PHI and ePHI.
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.