Deus ex Machina: Securing Industrial Control Systems
| Contact Us | |
| Free Demo | |
| Chat | |
The critical infrastructure that we rely on every day is becoming increasingly vulnerable to attack. What can be done to secure these systems?
As many recent incidents have demonstrated, critical infrastructure around the globe is extremely vulnerable to attack – especially within industrial control system (ICS) environments commonly found in process industries, utility plants and manufacturing facilities. Unlike typical IT environments in businesses, which are comprised of workstations, routers, networks, servers and switches, ICS environments are integrated with their own proprietary technology that makes up its own production control system network. This network includes PLCs, remote terminals, protocol converters and data acquisition servers and it’s separated from the business network by its own firewall.
These networks are highly complex and are built with business operations and speed in mind – not security. As a result, they often don’t go through the full range of security validation tests and are found to be full of weaknesses including improper input validation, poor credentials management, improper authentication and flaws found in permissions, privileges and access controls (see charts below). Furthermore, many ICS networks were originally designed with physical network separation as a key element of security, a technique that has since been compromised by the modern need for remote management of systems – a feature that was added after the fact without fully compensating for the potential loss of security. All of this leaves ICS environments susceptible to attackers, who can access and take control of the systems through a number of entry points. In addition, according to the Open-Source Vulnerability Database, more than 1000 ICS vulnerabilities have been found since 2001, ranging from remote code execution to cross site scripting, denial of service and buffer overflows.
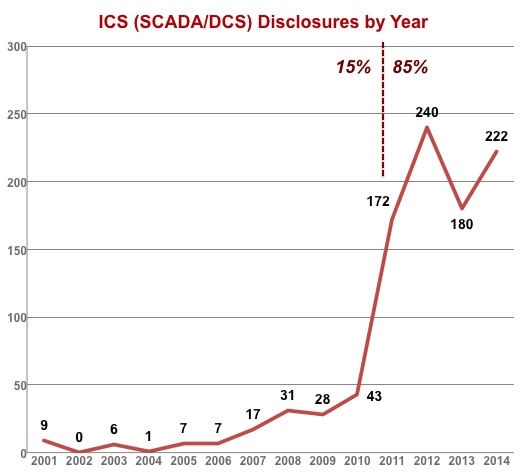
ICS (SCADA/DCS) disclousres by year. Image via Scadahacker.com
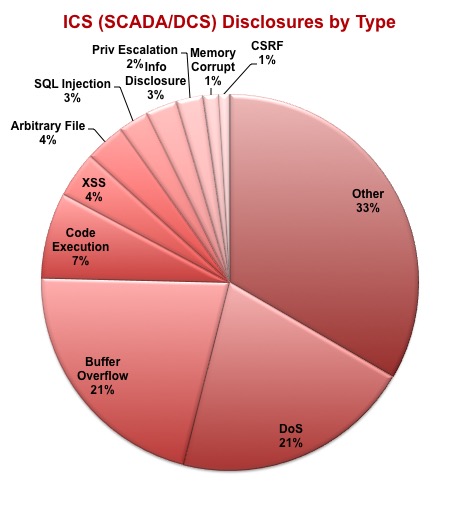
ICS (SCADA/DCS) disclousres by type. Image via Scadahacker.com
So what kind of attacks are ICS environments typically susceptible to, and why would an ICS be targeted in a cyberattack? Attacks can fall under a number of categories including politically motivated hacktivists or nation-state sponsored groups as well as cybercriminals looking to extort money by disrupting operations in ICS environments. An attack on a water treatment plant, a telecommunications network or a power station can result in major impacts across the federal, civilian and corporate levels. Drinking water could be compromised, communications could be completely shut down or major electric power outages could result from a successful attack. Each scenario has their own level of damages, both direct and indirect, and the scope of the impact would be determined by the scale of the targeted victim.
With the amount of vulnerabilities found in ICS environments and the lack of strong security posture that many suffer from, it’s realistic to state that if an attack was launched it could likely be successful and inflict some serious damages. We have already seen a proof of concept being laid by attacks like Stuxnet and the Duqu 2.0 attack on Kaspersky Lab. These incidents have shown that – particularly when sponsored by a nation-state – a severely powerful and sophisticated attack is very possible. They have also proven beyond a doubt that there are organizations with the desire and the capability to execute a potentially catastrophic attack.
Protecting against targeted cyberattacks on ICS systems requires a combination of updated security protocols and the right protection technologies. Companies looking to secure ICS environments must have strict processes in place for patch management, event monitoring, and incident response. ICS network segmentation should be extended to isolate remote management consoles from other business networks. Cybersecurity protocols must be integrated with physical security strategies to ensure that protection efforts are aligned against targeted attacks that combine cyber and physical security exploits.
Finally, protection technologies should be applied to detect and remediate cyberattacks or potential intrusions. The networks used in ICS environments should have firewalls in place to control inbound and outbound network traffic as well as intrusion detection systems to monitor for malicious activity on the network. Unidirectional security gateways, widely used in defense, are now commonly used in industrial control system security to restrict sensitive data flows to a single direction between networks. Access, device and application control solutions such as application whitelisting should be deployed to restrict activity by users, devices and applications in an ICS environment on a default-deny basis. There’s no single model to guarantee that ICS are secure, but developing a security strategy to incorporate these policies and solutions based on your specific environment and requirements makes ICS security achievable.
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.